Hacktivist campaigns in 2025 have evolved into obvious, fast-moving, and slogan-driven operations seeking maximum exposure rather than stealth.
A new analysis of more than 11,000 posts from over 120 hacktivist groups reveals that these politically motivated actors are now weaponizing open social platforms, particularly Telegram, to orchestrate cyberattacks and spread propaganda far beyond conflict zones.
Although the focus of this research centers on the MENA region, the digital battlefield spans continents, affecting targets across Europe, the Americas, and Asia.
Open Platforms Drive Coordination and Propaganda
Unlike earlier assumptions that hacktivists operate mainly within the dark web, today’s campaigns take place primarily in public.
Telegram has become the beating heart of hacktivist ecosystems, serving as the central hub for planning attacks, issuing calls to action, and boasting of successful operations. The platform’s high channel density allows threat groups to mobilize participants instantly.
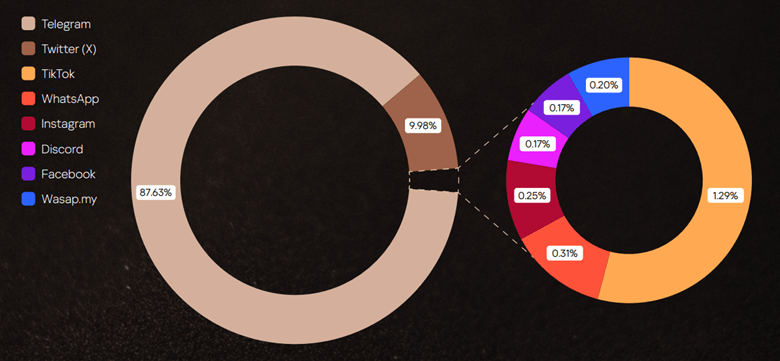
X (formerly Twitter) ranks second as a tool for amplifying messages and spreading related hashtags that act as connective tissue for these operations.
Hashtags are integral to hacktivist communication strategies. In 2025, researchers identified 2,063 unique tags with 1,484 appearing for the first time, signifying evolving alliances and shifting agendas. Tags often represent political causes, target nations, or the names of attacking groups.
The lifecycle of a typical hashtag is short, lasting about two months before being retired or replaced due to channel takedowns or campaign dissolution. However, when several groups collaborate, popular hashtags can persist longer, fueling broader awareness and influence.
DDoS Attacks Remain the Weapon of Choice
Analysis shows that 58% of hashtagged posts report completed attacks, with Distributed Denial of Service (DDoS) incidents making up 61% of those. These attacks remain the most accessible and high-impact method for hacktivist collectives seeking visibility over precision.
The timing of posted threats often correlates with near-term action, typically within the same week or month. This pattern makes monitoring open channels a valuable early-warning tool for security teams.
Researchers stress the importance of prioritizing scalable DDoS defenses, active threat intelligence collection, and continuous monitoring of Telegram ecosystems.
They advise that even organizations outside geopolitical hotspots maintain heightened vigilance, as hacktivists seek spectacle rather than geographically limited outcomes.
The 2025 hacktivist landscape proves that influence, not technical sophistication, drives modern cyber activism. Visibility is both the means and the end, and Telegram has firmly positioned itself as the new global headquarters for these digital insurgents.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates