eSentire’s Threat Response Unit (TRU) responded to a sophisticated attack targeting a certified public accounting firm in the United States.
The eSentire security investigation revealed that the threat was enabled through a clever combination of social engineering and cutting-edge malware obfuscation, harnessing the cloud-based Zoho WorkDrive platform to deliver the elusive PureRAT remote access trojan (RAT).
Social Engineering Opens the Door
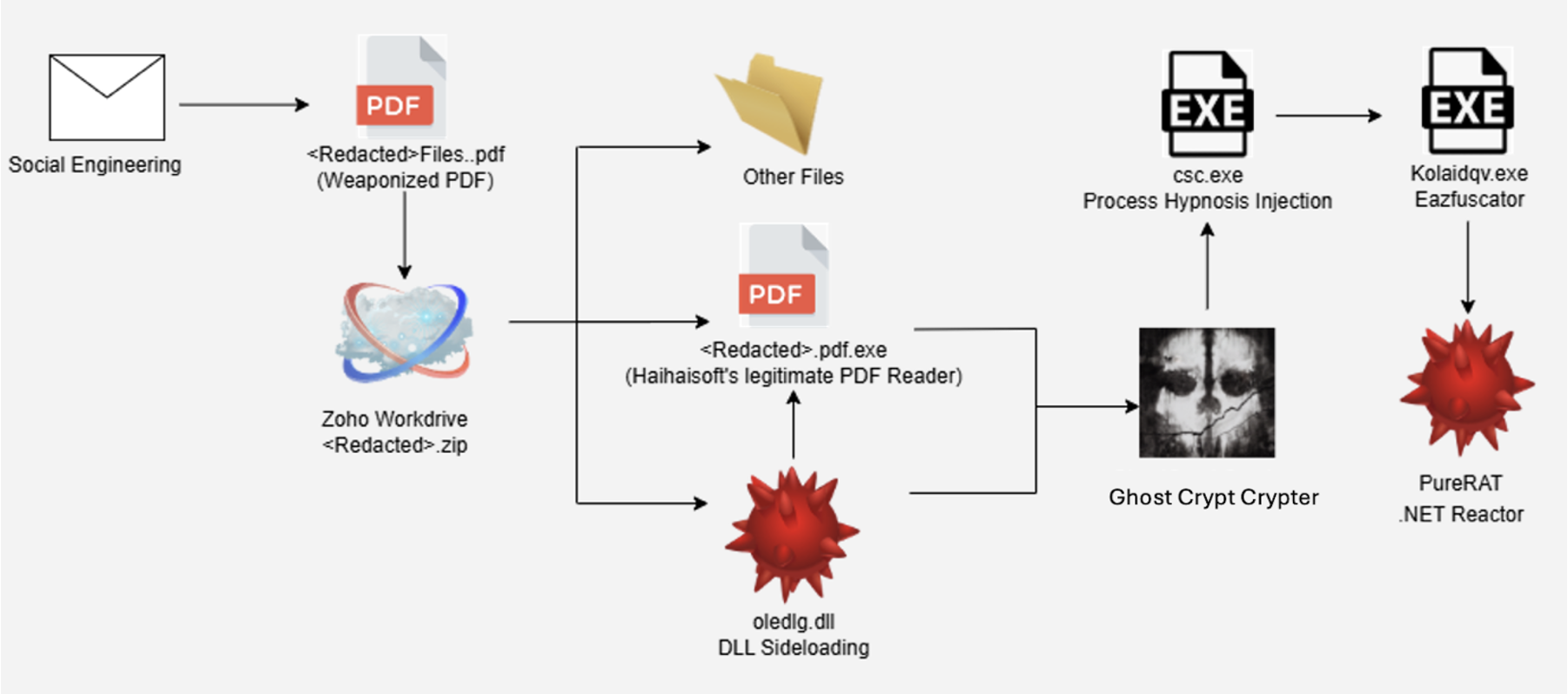
The initial compromise began when a threat actor posed as a legitimate new client and sent the victim a PDF via email, urging quick action with a follow-up phone call.
The PDF itself contained a link to a Zoho WorkDrive folder an increasingly popular method to bypass traditional email security controls.
Upon accessing the folder, the victim downloaded a ZIP archive masquerading as innocuous tax documents and identification files, but which in fact contained a double-extension executable (“.pdf.exe”) and a malicious DLL renamed as “CriticalUpdater0549303.dll.”

Central to this attack was the utilization of a new crypter-as-a-service named “Ghost Crypt,” first seen advertised on hackforums in April 2025.
Ghost Crypt is designed to evade antivirus and cloud-based security solutions, delivering both executables and DLLs packed with advanced sideloading and injection techniques.
The malicious payload, hidden within the DLL and encrypted with a modified ChaCha20 algorithm, was sideloaded via a benign third-party application (“hpreader.exe”).
Once executed, the DLL established persistence by copying itself to the user’s documents and creating a registry run key for subsequent execution.
Ghost Crypt’s approach included a custom process-injection method dubbed “Process Hypnosis,” where the malware launched a legitimate Windows binary in debug mode and injected the PureRAT malware into its memory space.
This technique, leveraging APIs such as CreateProcessW, VirtualAllocEx, and WriteProcessMemory, ensured the malicious code operated within a trusted process, while further evading detection by patching specific Windows functions to circumvent Microsoft’s modern anti-injection defenses.
Targeted Data Collection
The subsequent payload, PureRAT, emerged from multiple layers of AES-256 encryption and GZIP decompression managed by obfuscated .NET binaries.
PureRAT, now the principal offering from the developer PureCoder, loads additional payloads by resolving hardcoded class and method names, then leveraging .NET’s Assembly.Load mechanisms.
Notably, PureRAT uses embedded X.509 certificates uniquely generated per campaign for secure command and control (C2) communications, and maintains stealth by preventing system sleep states.
Once active, PureRAT performs extensive reconnaissance, targeting a broad range of Chrome and Chromium-based browser extensions for cryptocurrency wallets, alongside checks for local installations of popular messaging applications and desktop crypto-wallet software.
All collected information is exfiltrated to the C2 server, with the malware then awaiting additional plugins or instructions to be delivered by operators.
This attack typifies the increasing sophistication of financially motivated threat actors, who combine agile social engineering, commodity malware, and rapidly evolving obfuscation services.
The seamless use of legitimate cloud collaboration platforms such as Zoho WorkDrive for malware delivery, together with on-demand crypters like Ghost Crypt which even offer “bypass guarantees” and integration with dark web malware testers like Kleenscan compounds the detection challenges faced by defenders.
According to the Report, eSentire’s 24/7 Security Operations Centers (SOCs), backed by the TRU’s original threat research, were able to rapidly detect, investigate, and contain the threat before further damage occurred.
The case highlights the necessity of both advanced technical controls and continuous human-led threat hunting, especially as nation-state techniques increasingly become accessible to common cybercriminals.
Continuous vigilance, layered detection mechanisms, and proactive user education are all crucial in combating this latest wave of obfuscated malware attacks.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates