In a concerning development, sophisticated threat actors are increasingly exploiting free email services as part of their cyber espionage campaigns, targeting government and educational institutions.
Recent investigations highlight how Advanced Persistent Threat (APT) groups like GreenSpot are leveraging the infrastructure of widely-used platforms, such as the Chinese email provider 163.com, to steal sensitive credentials through elaborate phishing operations.
The GreenSpot APT group, operational since 2007 and active primarily in East Asia, employs highly deceptive tactics aimed at user credential theft.
By creating counterfeit domains and phishing websites, they impersonate legitimate email services to lure users into divulging their login details.

These malicious campaigns often target government, academic, and military organizations entities that frequently rely on free email services for internal and external communications.
Sophisticated Infrastructure with Spoofed Domains
A detailed examination of the group’s recent operations reveals the deployment of domains closely resembling legitimate 163.com infrastructure.
For instance, domains such as mail.eco163[.]com and mail.ll63[.]net were observed hosting fake login interfaces that mimic the authentic design of 163.com services.
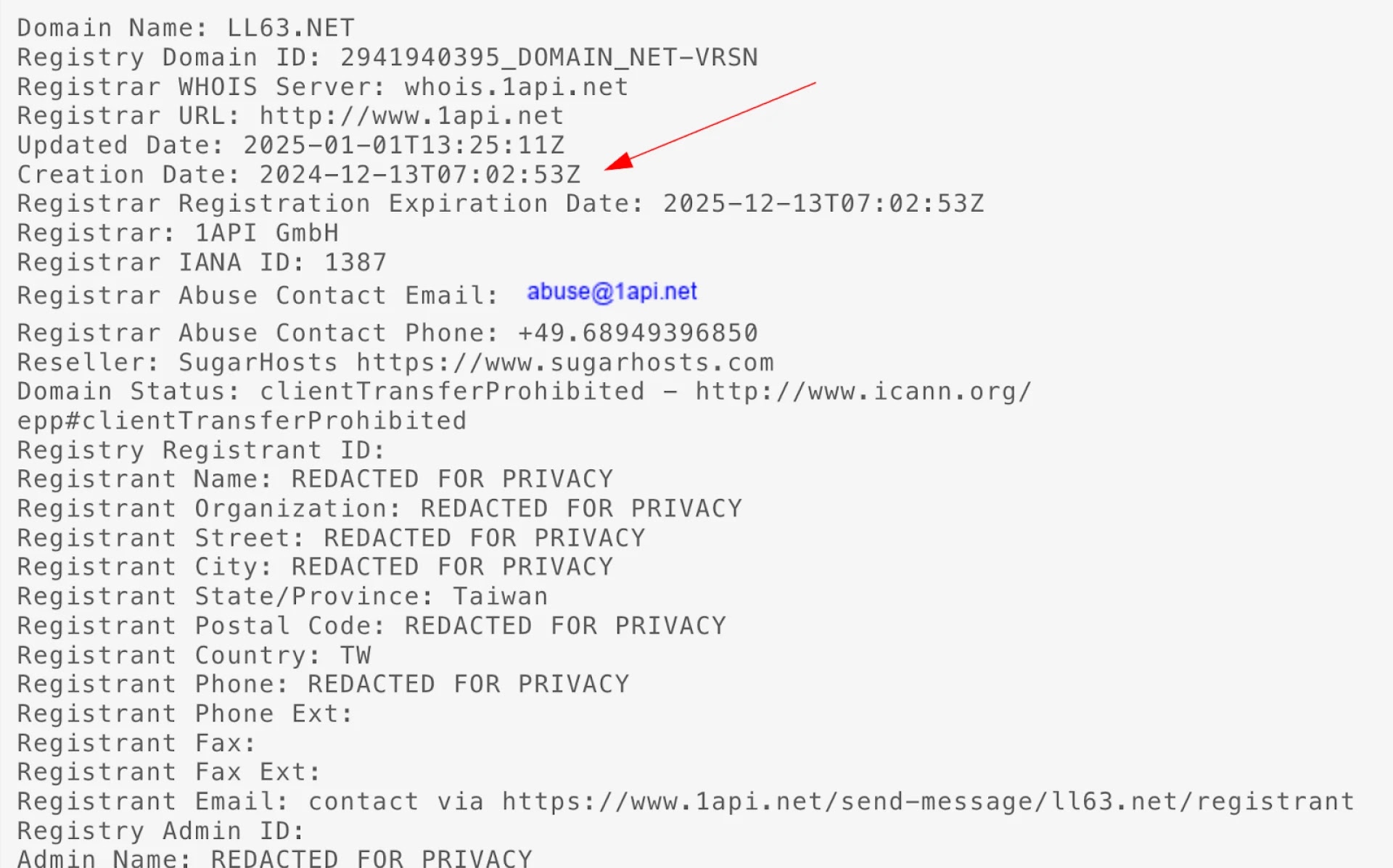
These domains are often registered within hours of one another via third-party resellers, a tactic that obfuscates links to the threat actor and complicates tracing efforts.
Furthermore, GreenSpot’s infrastructure demonstrates advanced capabilities, such as the misuse of TLS certificates and server configurations.
Some malicious servers intentionally generate non-standard HTTP status codes, which may serve to evade detection by network security tools.
These deceptive setups enable the seamless collection of user credentials, which are either exploited directly or sold within underground cybercriminal marketplaces.
Another layer of sophistication comes from malicious download pages masquerading as legitimate file-sharing services.
These pages, imitating 163.com’s large attachment features, pressure users into entering their credentials under the guise of accessing shared documents.
Any password entry is tested for validity, with the successful capture of credentials executed through embedded PHP scripts.
Implications for Government and Educational Sectors
While the current campaign is geographically focused on East Asia, the tactics employed by GreenSpot present a global threat.
Free email platforms, despite their ubiquity and accessibility, are often inadequately protected compared to enterprise-grade communication systems.
This vulnerability makes them a lucrative target for threat actors seeking to exploit the absence of multi-factor authentication and other advanced security measures.
Educational institutions and government agencies are particularly attractive targets due to the sensitive nature of the data exchanged via their email systems.
Credential theft in these sectors may lead to data breaches, intellectual property theft, and even compromises in national security.
According to the Hunt report, this campaign underscores the importance of adopting proactive cybersecurity measures.
Organizations are urged to enable multi-factor authentication, maintain updated threat intelligence feeds, and closely monitor for anomalies in domain activity and certificate usage.
Increased user awareness training about phishing tactics is also critical in mitigating the risks associated with credential theft.
With threat actors continually evolving their tactics, a coordinated effort between institutions and cybersecurity experts is essential to safeguard sensitive information and prevent further exploitation of free email services.