Cybersecurity analysts have observed sustained exploitation campaigns targeting unpatched Ivanti Connect Secure VPN appliances.
Threat actors have actively leveraged newly disclosed vulnerabilities CVE-2025-0282 and CVE-2025-22457 to breach enterprise networks and deploy sophisticated malware, including the notorious Cobalt Strike Beacon.
The Japanese CERT Coordination Center (JPCERT/CC) has issued a detailed report outlining the deployment techniques, malware families, and operational tradecraft witnessed through July 2025, highlighting the advanced methodologies attackers now use to evade detection and maintain persistent access.
Custom Malware Deployment
Investigations detail a complex infection chain, beginning with exploitation of the VPN’s remote access flaws.
Attackers first establish a beachhead utilizing legitimate system binaries such as rmic.exe or push_detect.exe which are abused to sideload a custom loader called MDifyLoader.

Based on the open-source libPeConv project, MDifyLoader consumes an encrypted payload and decrypts it in-memory using an RC4 key derived from the MD5 hash of an accompanying executable.
This convoluted three-file requirement (legitimate binary, loader DLL, and encrypted payload) is likely designed to hinder both automated and static malware analysis.
Upon decryption, MDifyLoader loads Cobalt Strike Beacon v4.5 directly into system memory, making forensics especially challenging.
Technical analysis also shows significant junk code injection and obfuscation within the loader randomized function calls and variable assignments impede dynamic and static unpacking by researchers.
Notably, unlike standard implementations where configurations are XOR-decoded, this campaign utilized RC4 encryption with the hardcoded key “google” for its Beacon configs, indicating a custom twist aimed at bypassing signature-based detections.
Emergence of Vshell RAT
Parallel to Cobalt Strike activity, the attackers deployed the Golang-based vshell RAT (version 4.6.0) on compromised endpoints.
A notable operational blunder revealed the tool’s built-in language check for Chinese locale, as repeated execution attempts failed until a compatible environment was found implying development or test code was inadvertently shipped in the wild.
Reconnaissance and lateral movement are facilitated by a heavily modified, fileless variant of the Fscan network scanner.
Using python.exe to sideload a malicious python311.dll developed from FilelessRemotePE, attackers loaded an RC4-encrypted Fscan executable (“k.bin”) directly into memory, bypassing disk-based detections.
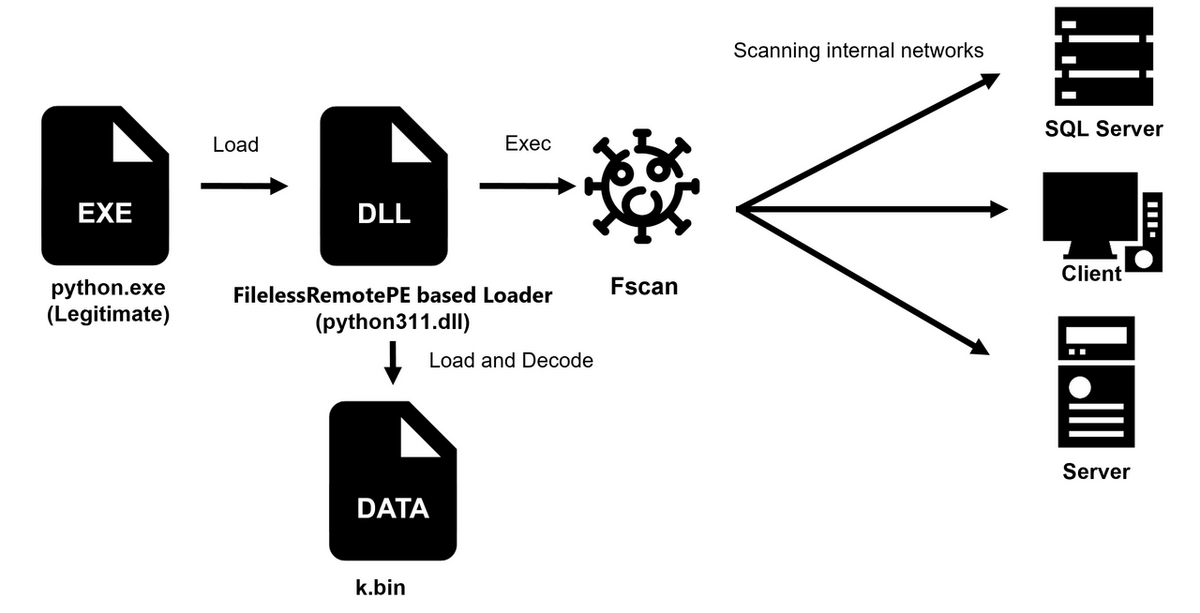
An ETW bypass embedded in the loader further disables Windows telemetry, highlighting an EDR-aware attack.
Following initial breach, actors conduct broad internal reconnaissance, leveraging brute-force attacks against Active Directory, SMB, FTP, MSSQL, and SSH to accumulate valid credentials.
Exploitation of the notorious MS17-010 (EternalBlue) SMB vulnerability persists as a preferred lateral movement method.
Using newly obtained credentials, attackers move laterally via RDP and SMB, dropping additional malware as they pivot.
Persistence is ensured through the creation and group-assignment of new domain accounts, malware registration as system services, and scheduled task configuration. These measures are taken to maintain access even if initial compromise vectors are remediated.
Throughout, attackers employ extensive defense evasion tactics: continual masquerading using legitimate binaries, aggressive log and artifact deletion, and deobfuscation-resistant loader design.
The observed campaign underscores the urgent need to patch vulnerable VPN appliances, monitor for anomalous lateral movement, and hunt for malicious sideloading activity. Below are key indicators to assist defenders in threat hunting:
Indicators of Compromise (IOCs)
| Category | File/Domain/IP | SHA256 Hash |
|---|---|---|
| Legitimate File | python.exe | 0cbf71efa09ec4ce62d95c1448553314728ed5850720c8ad40352bfbb39be99a |
| Loader | python311.dll (Fscan Loader) | 699290a753f35ae3f05a7ea1984d95f6e6f21971a146714fca5708896e5e6218 |
| Fscan Payload | k.bin (Encoded Fscan) | cff2afc651a9cba84a11a4e275cc9ec49e29af5fd968352d40aeee07fb00445e |
| MDifyLoader | jli.dll | 45ecb7b23b328ab762d8519e69738a20eb0cd5618a10abb2c57a9c72582aa7e7 |
| Cobalt Strike | update.dat | 09087fc4f8c261a810479bb574b0ecbf8173d4a8365a73113025bd506b95e3d7 |
| Cobalt Config | config.ini | 1652ab693512cd4f26cc73e253b5b9b0e342ac70aa767524264fef08706d0e69 |
| Vshell Variants | ws_windows_amd2.exe, ws_windows_amd64.exe, ws.exe | 48f3915fb8d8ad39dc5267894a950efc863bcc660f1654187b3d77a302fd040f, 54350d677174269b4dc25b0ccfb0029d6aeac5abbbc8d39eb880c9fd95691125, 85f9819118af284e6b00ce49fb0c85ff0c0b9d7a0589e1bb56a275ed91314965 |
| C2 Domains/IPs | 172.237.6[.]207:80; proxy.objectlook[.]com:80; api.openedr.eu[.]org:443; community.openedr.eu[.]org:443; query.datasophos[.]com:443 |
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates