Cybercriminals are leveraging TinyLoader’s versatile infection and propagation techniques to steal cryptocurrency and deploy additional malware on Windows systems.
Advanced Persistence, Propagation, and Payload Delivery
TinyLoader establishes deep persistence by creating hidden copies of itself named “Update.exe” in users’ Desktop and Documents folders, and by modifying Windows registry settings to hijack .txt file associations so that the malware executes whenever text files are opened.
The loader spreads through USB drives by copying itself under deceptive filenames such as “Photo.jpg.exe” and “Document.pdf.exe,” complete with autorun entries that infect any system the removable media is plugged into.
On network shares, it leverages existing user permissions to plant “Update.exe” in accessible folders, enabling lateral movement across corporate networks. Beyond propagation, TinyLoader functions as a multi-stage delivery platform.
Once executed, it reaches out to attacker-controlled URLs to download secondary payloads, most notably Redline Stealer for credential theft and cryptocurrency wallet exfiltration, and DCRat for full remote access and command-and-control capabilities.
The malware continuously monitors the Windows clipboard at a high frequency to detect copied cryptocurrency addresses (Bitcoin, Ethereum, Litecoin, TRON). It transparently replaces them with attacker-owned addresses, ensuring funds are redirected without the user’s awareness.
Infrastructure Analysis and Mitigation Strategies
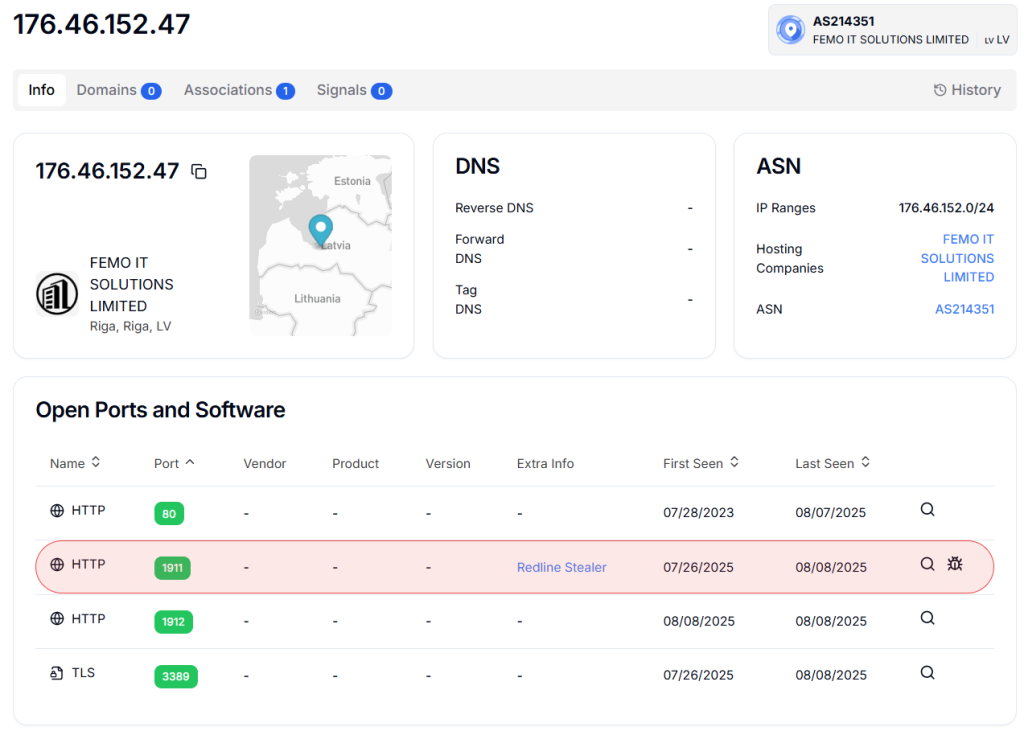
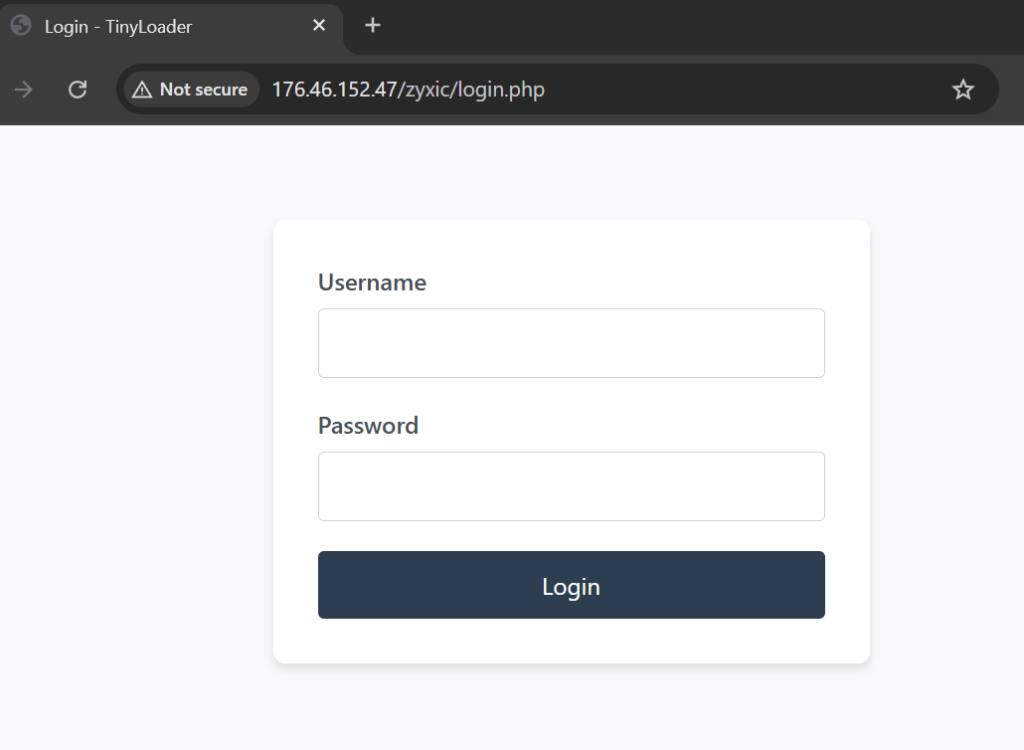
Investigation of IP address 176.46.152.47 revealed an active TinyLoader C2 panel hosted on Apache/2.4.58 (Windows x64), with the HTML title “Login – TinyLoader” serving as a distinct signature for identifying additional panels.
A crawler search uncovered companion panels at 176.46.152.46 (Riga), and servers in London and the Netherlands, all provisioned by Virtualine Technologies, highlighting a distributed, multi-country infrastructure designed for resilience against takedowns.
AttackCapture™ data confirmed live DCRat payload distribution from Railnet LLC–hosted servers, capturing four malware samples totaling 211 KB in August 2025.
To defend against TinyLoader campaigns, organizations should block known malicious IPs (176.46.152.47, 176.46.152.46, 107.150.0.155) and monitor HTTP traffic for the “Login – TinyLoader” signature.
Enforcing USB device policies, scanning removable media for executables with double extensions, and auditing network share activity for unexpected “Update.exe” files can thwart lateral spread.
Deploying endpoint monitoring to detect registry modifications targeting file associations and high-frequency clipboard access will help catch stealthy persistence and crypto-hijacking behavior.
User education on verifying cryptocurrency addresses and exercising caution with desktop shortcuts, especially those masquerading as backup tools, adds a critical layer of defense against this evolving threat.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates