In a recent security research effort, three critical vulnerabilities have been identified in the firmware of the TOTOLINK X6000R router (version V9.4.0cu.1360_B20241207, released March 28, 2025). Exploitation of these vulnerabilities allows unauthenticated attackers to trigger denial-of-service conditions, corrupt system files, and execute arbitrary commands on the device.
Given the widespread deployment of TOTOLINK home and small-office routers globally, these discoveries underscore the urgent need for firmware updates and robust IoT security practices.
Vulnerability Summary and Impact
A concise overview of the three newly documented security issues is provided below:
| CVE Identifier | Severity | CVSS 3.1 Score | Description |
|---|---|---|---|
| CVE-2025-52905 | High | 7.0 | Argument injection vulnerability in input sanitization allowing denial-of-service attacks that crash the router or overwhelm remote servers. |
| CVE-2025-52906 | Critical | 9.3 | Unauthenticated command injection vulnerability enabling remote execution of arbitrary commands with web server privileges. |
| CVE-2025-52907 | High | 7.3 | Incomplete input blocklisting lets attackers bypass security checks to corrupt system files, cause persistent DoS, or achieve arbitrary file writes and chained RCE. |
These vulnerabilities all reside within the router’s web interface, specifically the /cgi-bin/cstecgi.cgi endpoint.
This central handler processes incoming requests via a topicurl parameter, which is used to dispatch internal configuration and management functions.
Because the endpoint fails to enforce comprehensive input validation, attackers can inject crafted payloads to subvert intended operations and seize control of the device.
Technical Analysis
Argument Injection (CVE-2025-52905)
The firmware input validation relies on a blocklist approach intended to reject malicious characters. However, the hyphen (-) character is not filtered, permitting hostile input to slip through.
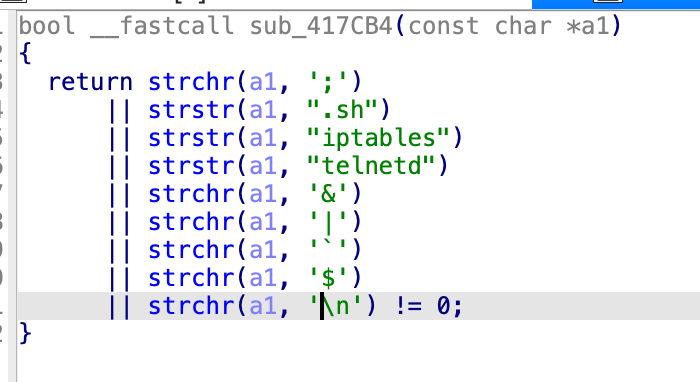
When combined with certain function calls, this argument injection enables denial-of-service scenarios. Specifically, carefully structured topicurl values can trigger repeated internal restarts or resource exhaustion, leading to service crashes or overloaded remote endpoints.
Unauthenticated Command Injection (CVE-2025-52906)
Within the setEasyMeshAgentCfg function—used to configure the EasyMesh agent—the agentName parameter is passed directly to system shell commands without proper sanitization.
An attacker able to reach the router web interface can inject shell metacharacters to execute arbitrary commands.
Successful exploitation yields code execution under the privileges of the web server process, granting access to privileged operations such as traffic interception, lateral movement across the network, and installation of persistent malware.
Security Bypass and Arbitrary File Write (CVE-2025-52907)
The flawed input sanitization routine applies across multiple components beyond EasyMesh, including the setWizardCfg function.
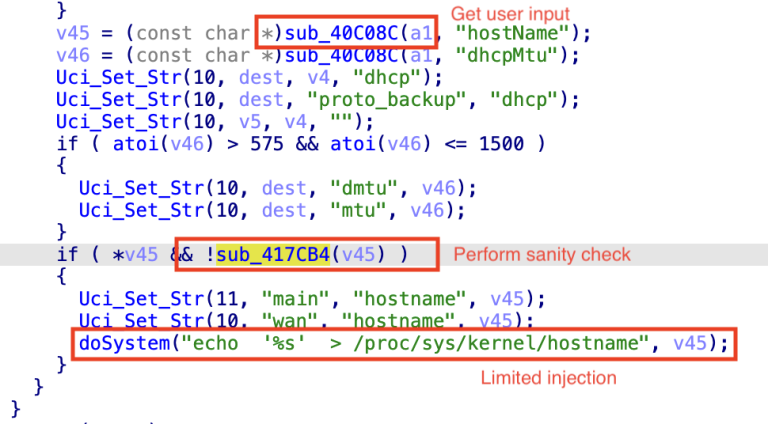
By exploiting the same incomplete blocklist, an attacker can bypass the confidence check for user-supplied values, enabling arbitrary file writes.
This allows modification of critical files such as /etc/passwd or boot scripts—paving the way for root-level access and persistent remote code execution following device reboot.
Mitigations
In collaboration with security researchers, TOTOLINK has released firmware V9.4.0cu.1498_B20250826, which corrects the input validation logic and enforces strict sanitization for all user-controlled parameters.
All users of the X6000R router are strongly advised to upgrade immediately via the official TOTOLINK download portal to eliminate exposure to these critical vulnerabilities.
Beyond firmware updates, users should:
- Change default router credentials and employ strong, unique passwords for web administration.
- Disable remote management if not required.
- Segment IoT devices on a dedicated network to limit potential lateral movement.
- Monitor network traffic and update intrusion prevention systems to detect anomalous web interface calls.
For customers of Palo Alto Networks, protective measures include:
- Next-Generation Firewall with Threat Prevention or Advanced Threat Prevention subscriptions to block exploit attempts.
- Device Security solution for real-time visibility and risk assessment of IoT devices.
- Cortex Xpanse and ASM add-on for XSIAM to discover internet-exposed TOTOLINK routers and continuously monitor for policy compliance.
Home routers serve as the frontline defense for connected devices and corporate assets. Timely patching and layered security controls are essential to safeguard against unauthorized access, service disruption, and remote code execution.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.