This article should read as a concise cybersecurity news piece summarizing a sophisticated APT campaign by TransparentTribe (APT36) targeting Indian defense systems running BOSS Linux. Here’s the full write-up:
TransparentTribe Targets Linux Systems
In a significant escalation of cross-border cyber-espionage activity, researchers have uncovered a new campaign by the Pakistan-linked threat actor TransparentTribe (APT36) targeting Linux-based systems used by Indian defense and government entities.
The operation, active since June 2025, delivers a Golang-based Remote Access Trojan (DeskRAT) through weaponized .desktop files embedded in phishing campaigns.
Evolution of the Infection Chain
According to joint analyses by CYFIRMA and Sekoia.io, the attack begins with phishing emails containing malicious ZIP archives masquerading as official defense communications.
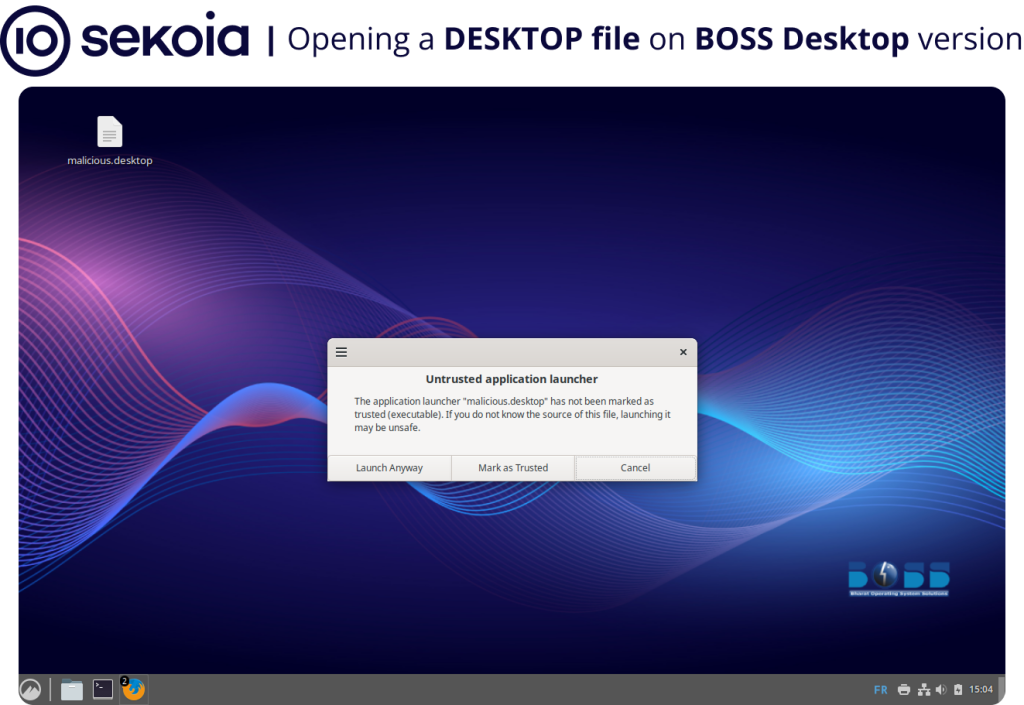
These archives—such as Cyber-Security-Advisory.zip or MoM_regarding_Defence_Sectors_by_Secy_Defence_25_Sep_2025.zip—contain malicious .desktop files designed to exploit BOSS Linux, India’s government-endorsed operating system.
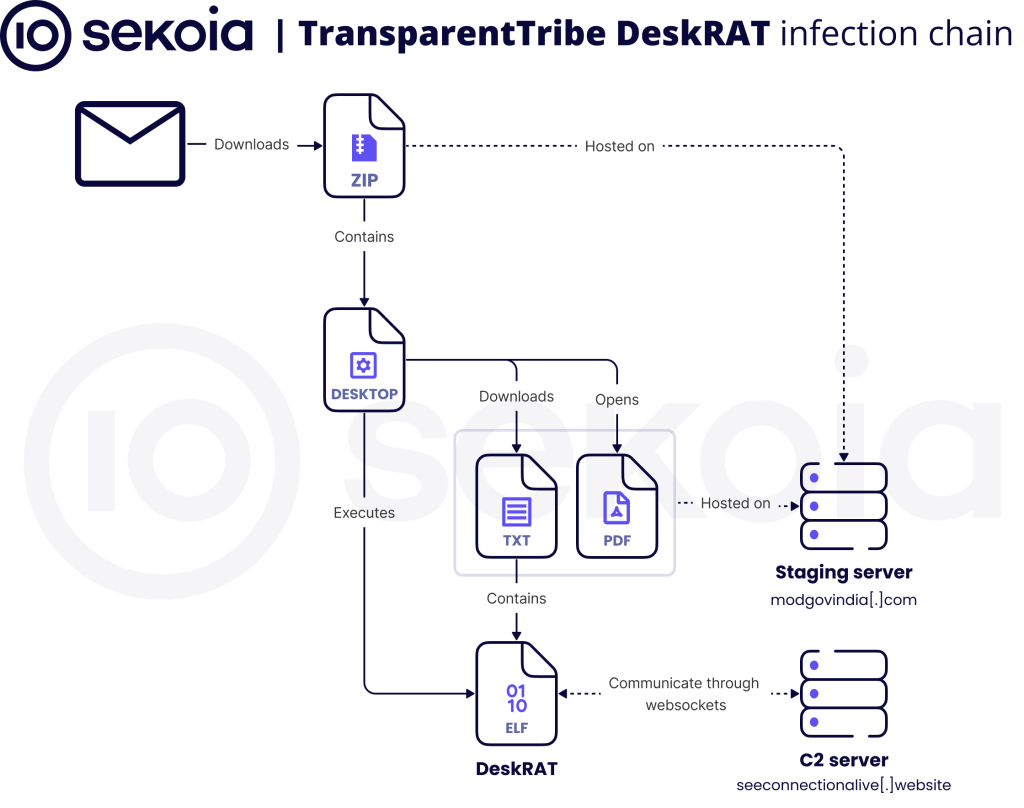
When executed, the shortcut file silently runs Bash one-liners that download base64-encoded payloads from attacker-controlled domains like modgovindia[.]com.
The payload is decoded, written into the /tmp/ directory, granted executable permissions, and launched in the background. Simultaneously, a decoy document, often a defense-related PDF, is opened using Firefox to distract the victim.
The technique leverages built-in Linux utilities such as curl, base64, and eval, minimizing dependencies and bypassing typical detection mechanisms. Earlier versions of the campaign used Google Drive links to distribute the payloads, but recent samples indicate a move toward dedicated staging servers, enhancing control and persistence.
DeskRAT: Golang-Based Espionage Tool
The final stage deploys DeskRAT, a custom Golang remote administration tool engineered for Linux environments.
Analysis of the sample (MD5: 3563518ef8389c7c7ac2a80984a2c4cd) reveals modular functions suggesting LLM-assisted development, with several fake “evasion” routines embedded to waste analyst time and confuse detection systems.
Once executed, DeskRAT establishes WebSocket-based command and control communications with servers such as seeconnectionalive[.]website and newforsomething[.]rest on port 8080.
The malware can browse files, exfiltrate data, execute remote commands, and upload additional payloads, offering operators complete control over infected machines.
The C2 infrastructure features a web-based “Advanced Client Monitoring & File Management System” interface used to manage compromised hosts, monitor real-time telemetry, and execute post-exploitation actions.
The campaign timing aligns with political unrest in the Ladakh and New Delhi regions, events that APT36 has seemingly exploited to enhance phishing credibility. Analysts are highly confident that these intrusions serve Pakistan’s strategic intelligence objectives, focusing primarily on Indian defense institutions.
Security researchers warn that TransparentTribe’s evolution from Windows to Linux espionage operations underscores a dangerous shift in threat actor sophistication.
Defense networks relying on BOSS Linux should reinforce email filtering, system hardening, and real-time monitoring to mitigate exposure to future campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates