A major cloud security incident has surfaced, exposing advanced threat actor tactics aimed at compromising AWS environments via stolen credentials.
Security researchers have uncovered a campaign dubbed TruffleNet that leverages the popular open-source tool TruffleHog to test compromised access keys and conduct systematic automated reconnaissance.
The operation’s hallmark is high-scale abuse of Amazon Simple Email Service (SES), which facilitates Business Email Compromise (BEC) campaigns using AWS’s trusted infrastructure.
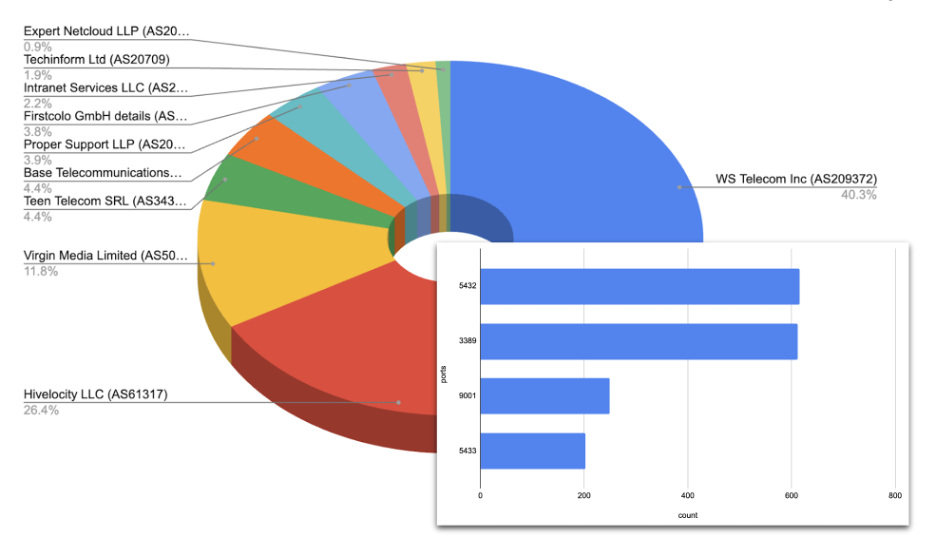
Over 800 unique hosts spanning 57 Class C networks were involved, highlighting how attackers now deploy dedicated, cloud-native infrastructure to evade conventional detection mechanisms.
TruffleNet: Credential Testing and Infrastructure Automation
TruffleNet’s attack playbook begins with credential validation, typically through AWS’s GetCallerIdentity API.
Once keys are confirmed, hosts quickly move to query the SES GetSendQuota endpoint, a precursor to large-scale email abuse. Unlike many cloud threats, most TruffleNet-origin IPs lacked reputation flags or antivirus detections, indicating bespoke infrastructure.
Host-level analysis revealed prevalent use of open ports 5432 and 3389 (commonly PostgreSQL and RDP,) though neither was exploited for standard purposes.
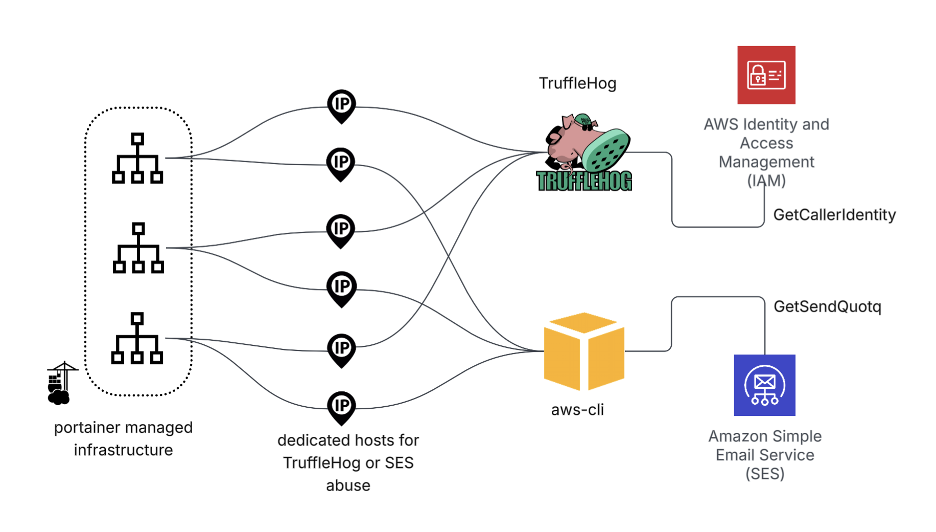
Instead, attackers configured Portainer as a Docker and Kubernetes management UI to coordinate fleets of nodes, essentially running malicious campaigns as “infrastructure-as-a-service” operations.
Key hosting providers for TruffleNet included WS Telecom Inc. and Hivelocity LLC in the United States.
The attack topology was methodically structured: some systems focused solely on reconnaissance (testing identities and quotas), while others likely acted as staging grounds for more invasive follow-on operations.
Security teams should monitor for unusual automation activities, such as repeated GetCallerIdentity and GetSendQuota calls, which may indicate credential theft attempts or SES reconnaissance.
SES Abuse Powers Sophisticated Business Email Compromise
After reconnaissance, the threat actors exploited AWS SES to set up new email-sending identities the prime enabler of BEC scams.
Attackers used APIs including ListIdentities, GetAccount, CreateUser, and CreateEmailIdentity to enumerate, escalate privileges, and establish persistent access.
Notably, one campaign used DomainKeys Identified Mail (DKIM) on compromised WordPress domains, allowing adversaries to authenticate fraudulent emails as originating from trusted brands.
Six compromised domains, including cfp-impactaction[.]com and restaurantalhes[.]com, were linked to active scams and known malware.
The group’s modus operandi included “BEC vendor onboarding W-9 scams,” where forged invoices and stolen EINs targeted oil and gas companies, demanding payments to typosquatted domains such as zoominfopay[.]com.
API patterns such as rapid sequence calls to PutAccountVdmAttributes and PutAccountDedicatedIpWarmupAttributes provided strong behavioral indicators of SES abuse, enabling attackers to fine-tune deliverability and bypass security checks.
To mitigate these evolving threats, organizations must implement least-privilege IAM policies, monitor for abnormal SES activity, and deploy behavioral analytics.
Fortinet’s FortiCNAPP suite, along with real-time alerting and composite anomaly detection, is vital for early detection and response to credential-driven cloud attacks, especially in environments where traditional security controls may fall short.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates