A sophisticated cyber espionage campaign attributed to UAC-0057, a Belarusian government-linked threat actor also known as UNC1151 and Ghostwriter, has been targeting Ukrainian and Polish organizations since April 2025 using weaponized archives containing legitimate-appearing PDF invitations and malicious Excel spreadsheets.
Decoy Documents Mask Malicious Payloads
Security researchers identified two distinct infection clusters that leverage carefully crafted decoy content to establish initial access.
In one notable case targeting Poland, attackers distributed a legitimate PDF invitation for the May 8, 2025, general assembly of the Union of Rural Municipalities of the Republic of Poland, which researchers found available on the union’s official website.
The Ukrainian campaign employed a three-page PDF document providing information about “Diia” services from Ukraine’s Ministry of Digital Transformation.
The decoy content matched formatting from an official April 17, 2025, government post, demonstrating the threat actor’s attention to authenticity.

However, these benign-appearing PDFs served as cover for malicious XLS spreadsheets containing obfuscated VBA macros. The macros, primarily obfuscated using MacroPack offensive security tools, implement sophisticated execution chains that drop and load malicious DLL implants.
Technical Execution Chain Analysis
The infection process varies between campaigns but follows consistent patterns. Ukrainian-targeted archives contain XLS files that write DLLs to locations %TEMP%\DefenderProtectionScope.log and execute them using regsvr32 /u /s commands.
More recent samples create Microsoft Cabinet (CAB) files and use Windows’ native expand.exe utility to extract payloads before execution.
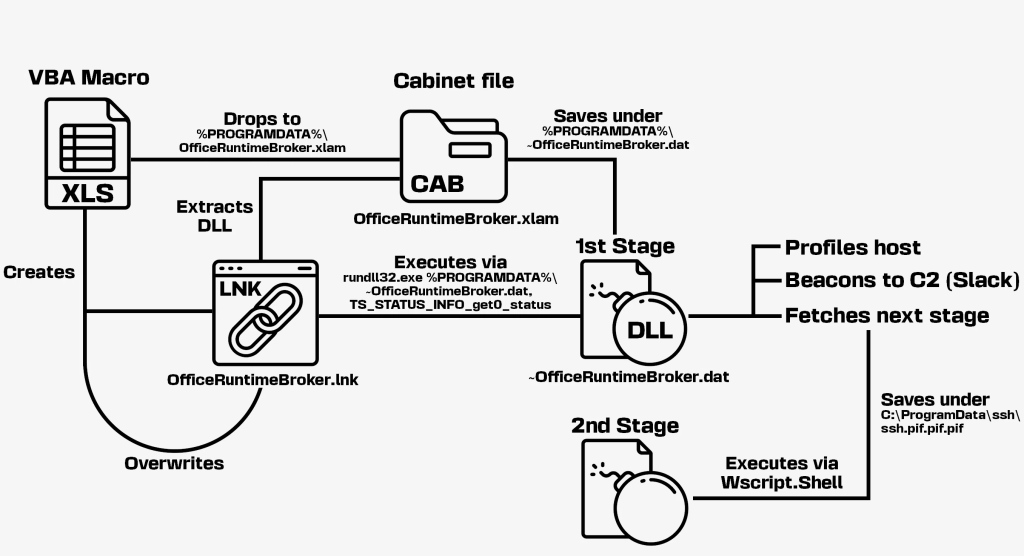
Polish campaigns demonstrate similar techniques but leverage different persistence mechanisms. One variant writes CAB files to %PROGRAMDATA%\OfficeRuntimeBroker.xlam and creates LNK files that execute extraction and loading commands through rundll32.exe shell32.dll,ShellExec_RunDLL.
The dropped DLL implants, written in both C# and C++ and obfuscated with ConfuserEx or packed with UPX, serve as first-stage downloaders that collect comprehensive system information, including OS details, hostname, CPU specifications, antivirus products, and external IP addresses via https://ip-info.ff.avast.com/v1/info.
Infrastructure Mimics Legitimate Services
UAC-0057’s supporting infrastructure demonstrates sophisticated impersonation techniques, registering domains through PublicDomainRegistry with .icu and .online TLDs that mimic legitimate websites.
Command and control servers use URLs identical to legitimate sites, such as sweetgeorgiayarns[.]online/wp-content/uploads/2025/04/06102226/Kims-hand-cards.jpg, those that replicate the exact path structure of the legitimate Sweet Georgia Yarns website.
Some Polish-targeted implants utilize Slack webhooks for command and control communication, representing an evolution in the threat actor’s tactics.
The persistent targeting of Ukraine and Poland aligns with UAC-0057’s historical operations and geopolitical interests linked to the Belarusian government.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates