A critical unauthenticated Remote Code Execution vulnerability has been discovered in Ubiquiti’s UniFi OS, affecting the backup API infrastructure across UniFi devices.
Identified as CVE-2025-52665, the vulnerability stems from improper input validation in the backup export endpoint, allowing attackers to execute arbitrary commands with elevated privileges.
The discovery was rewarded with a $25,000 bounty, highlighting the severity of the security flaw.
Vulnerability Overview and Discovery
Security researchers identified the vulnerability during a routine security assessment of a UniFi deployment.
The flaw originated from a misconfigured API endpoint that lacked proper access controls and input validation mechanisms.
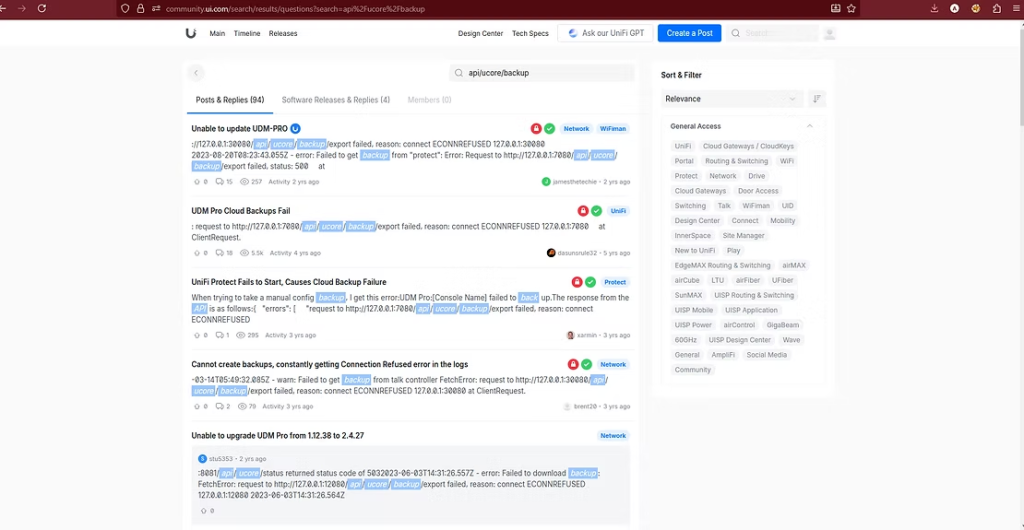
What made this discovery particularly concerning was that it represented only a portion of a broader issue involving multiple unauthenticated APIs throughout the UniFi OS ecosystem.
The vulnerability chain begins with network reconnaissance, where attackers can identify UniFi devices running on standard ports and probe for exposed API endpoints.
The vulnerability exists within the /api/ucore/backup/export endpoint, which is designed to handle backup operations across multiple UniFi service modules, including Network, Protect, and Access.
Researchers found that this endpoint accepts a directory parameter (dir) without any sanitization or escaping.
By injecting shell metacharacters into this parameter, attackers can break out of the intended command context and execute arbitrary system commands.
The backup export routine chains multiple shell operations, including mktemp, chmod, tar, and du commands, all of which process the unsanitized input.
The exploitation process demonstrates how multiple design weaknesses combine to create a critical vulnerability.
While the sensitive backup operation is intended to listen only on 127.0.0.1 with restricted access, researchers discovered that the endpoint was also exposed on port 9780 via an external-facing proxy.
This configuration oversight allowed unauthenticated network access to what should have been an internal-only service.
Attackers can craft a specially formatted JSON POST request that mimics legitimate backup orchestration calls.
The successful exploit payload uses command injection to execute arbitrary code while maintaining shell syntax validity.
By terminating injected commands with a semicolon and commenting out remaining tokens with a hash symbol, attackers bypass shell parsing errors that would otherwise prevent command execution.

This technique allowed researchers to exfiltrate sensitive files and establish interactive reverse shell access to affected devices, demonstrating complete system compromise.
Beyond the RCE vulnerability itself, researchers identified additional security gaps in the UniFi OS architecture.
Unauthenticated endpoints across the system expose sensitive operations, including NFC credential provisioning and retrieval of cryptographic key material used for access control systems.
The live Swagger documentation accessible on affected devices further simplifies endpoint enumeration and exploitation.
These interconnected vulnerabilities create multiple pathways for attackers to gain unauthorized access to UniFi Access systems, including door controls and NFC credential management systems.
Organizations running UniFi OS should prioritize immediate patching and review network access controls to restrict API endpoint exposure.
| Vulnerability Metric | Details |
|---|---|
| CVE ID | CVE-2025-52665 |
| Vulnerability Type | Remote Code Execution (RCE) |
| Authentication Required | No |
| Attack Vector | Network |
| CVSS Score | 9.8 (Critical) |
| Affected Component | UniFi OS – Backup API |
| Impact | Full System Compromise |
| Bounty Reward | $25,000 |
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today