A novel exploitation technique has been developed that significantly lowers the barrier to abusing the critical Linux kernel use-after-free (UAF) vulnerability tracked as CVE-2024-50264.
Awarded the Pwnie Award 2025 for Best Privilege Escalation, this vulnerability affects the AF_VSOCK subsystem in Linux kernels dating back to version 4.8, enabling unprivileged attackers to trigger a UAF within the virtio_vsock_sock object during socket connection operations.
Prior defenses such as randomized slab caches and SLAB bucket hardening thwarted naive heap spraying and cross-cache attacks, making exploitation largely impractical.
However, researchers have now demonstrated that a combination of innovative primitives and precise timing can reliably bypass these mitigations, rendering modern Linux distributions vulnerable to local privilege escalation.
Exploitation Methodology
Researchers utilized kernel-hack-drill, an open-source testing framework that simulates kernel behaviors and accelerates exploit development, to craft a multi-stage chain that reliably triggers the UAF race condition without terminating the exploit process.
The core advancement lies in interrupting the vulnerable connect() syscall via an “immortal” POSIX signal.
Unlike traditional signals that kill the process, this immortal signal repeatedly interrupts the syscall while preserving its stack state, sustaining the race window until the UAF is instantiated.
Once the vulnerable object is freed, the exploit pivots to a cross-cache allocation approach.
By submitting a carefully tuned sequence of allocation and deallocation requests, the attacker reclaims the freed virtio_vsock_sock object with a controlled slab cache allocation.
This deterministic replacement of the freed object permits precise corruption of its function pointers and internal fields.
Following object reclamation, the exploit corrupts crucial kernel structures such as msg_msg and pipe_buffer.
The UAF-induced corruption within the message queue subsystem yields out-of-bounds reads, exposing sensitive kernel pointers, including credential structures.
Concurrently, manipulation of the pipe_buffer’s page pointer facilitates arbitrary kernel memory writes.
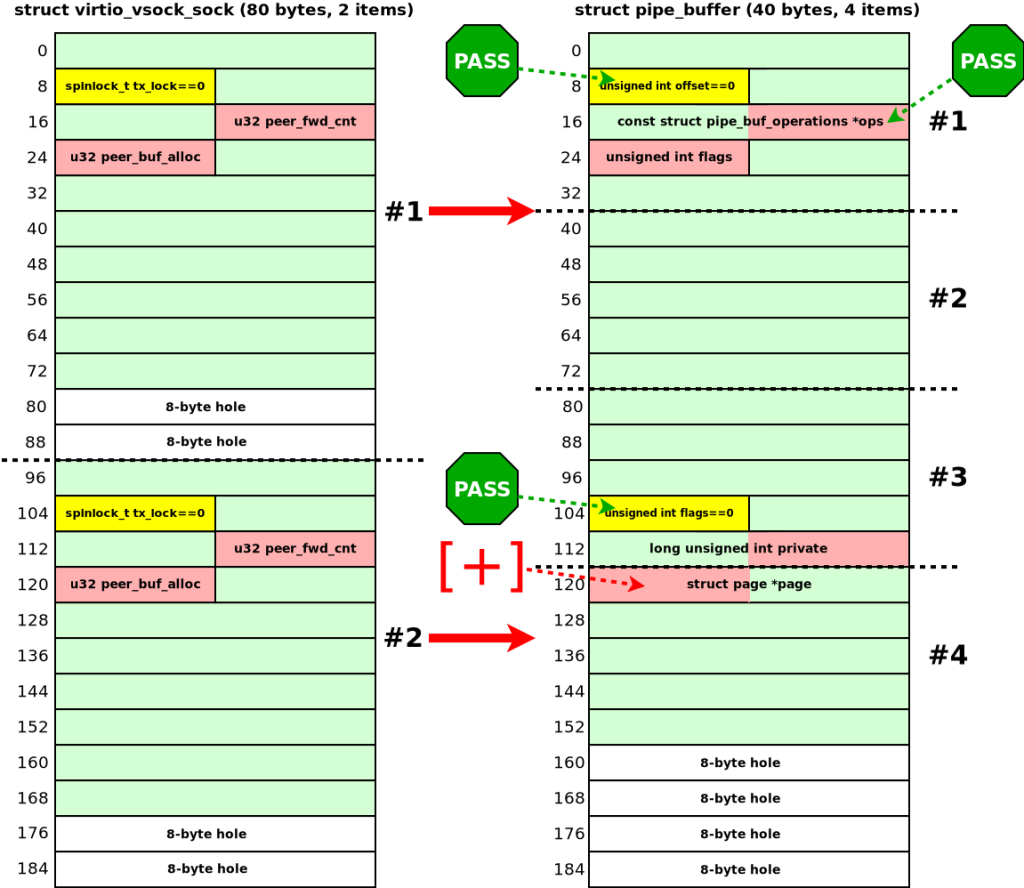
page pointer of the fourth pipe_buffer:This dual capability—leaking kernel addresses and writing to arbitrary memory—allows the attacker to elevate privileges by altering their process credentials seamlessly.
The technique further incorporates race condition speedrun strategies to bypass object pairing checks; rapid syscall invocation interleaved with slab cache pressure effectively subverts standard memory reuse protections.
By adapting concepts from recent privilege escalation vulnerabilities such as Dirty Pipe and Dirty Page Table, the new exploit chain operates even in environments patched against earlier UAF approaches.
The streamlined chain minimizes required syscall interactions and timing complexity, amplifying reliability across diverse kernel versions and configurations.
With CVE-2024-50264 now demonstrated as exploitable in hardened kernels, security teams must prioritize patch deployment and reassess kernel object hardening strategies to mitigate similar future threats.
The kernel-hack-drill project itself highlights the escalating sophistication of exploit research and underscores the ongoing imperative for proactive defense in Linux kernel development.
Find this Story Interesting! Follow us on Google News, LinkedIn and X to Get More Instant Updates