A significant update to the Vidar information-stealing malware has emerged, marking a new phase in its evolution and reasserting its dominance following the decline of Lumma Stealer. Known as Vidar 2.0, this new version was announced on October 6, 2025, by the developer “Loadbaks” on underground forums.
The update features a complete rewrite in C, advanced multi-threading, and enhanced credential theft efficiency that challenges browser-level encryption protections such as Chrome’s AppBound system.
Rebuilt in C with Multithreaded Data Theft
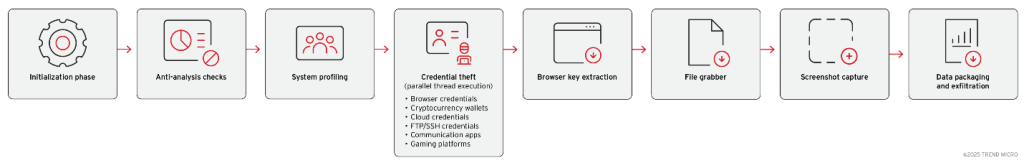
Vidar 2.0’s transition from C++ to pure C represents a notable architectural overhaul aimed at maximizing stability and performance. The malware now leverages a multithreaded design, allowing it to exploit multi-core processors efficiently.
Each thread handles distinct data-collection tasks, from browser credentials to cryptocurrency wallets, dramatically reducing the time Vidar remains active on compromised systems.
This parallelized approach improves both exfiltration speed and evasion, as the malware minimizes observable system footprint and operational duration.
Vidar dynamically adjusts its thread count based on hardware specifications, allocating additional worker threads on robust systems while conserving resources on weaker ones.
The optimization ensures smooth performance on various targets while maintaining stealth against endpoint monitoring tools.
Memory Injection Bypasses Browser Encryption
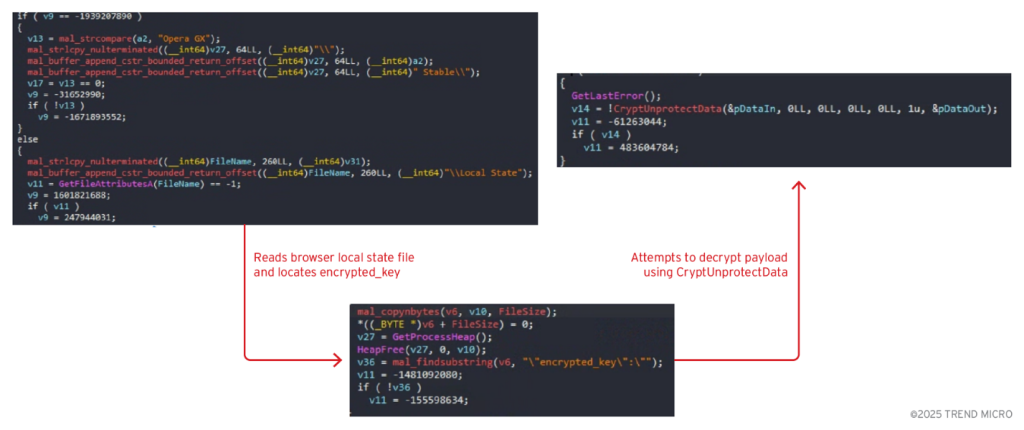
A crucial enhancement in Vidar 2.0 lies in its ability to bypass advanced browser encryption mechanisms. Developers claim the stealer uses “unique AppBound bypass methods” unavailable in public toolkits.
Binary analysis confirms that Vidar directly injects code into active browser processes, including Chrome, Edge, and Firefox, to extract decryption keys from live memory rather than from encrypted local storage.
By retrieving keys through reflective DLL or shellcode injection and transmitting them via named pipes, the malware sidesteps Chrome’s AppBound encryption that binds credentials to specific applications.
This method allows Vidar to steal not only browser-stored passwords but also tokens and session data for cloud services, gaming platforms, and communication apps like Discord and Telegram.
Its file grabber searches user directories for crypto wallet files such as 0.indexeddb.leveldb and \Monero, as well as authentication caches for AWS and Azure accounts.
Vidar’s polymorphic binary builder ensures that each compiled sample carries distinct signatures through control-flow flattening and embedded numeric state machines, hindering static detection and reverse engineering.
Trend Micro’s Trend Vision One™ platform has already deployed detections for Vidar 2.0’s indicators of compromise, offering real-time protection and threat intelligence for enterprise defenders.
As Lumma Stealer’s market influence fades, Vidar 2.0’s technical leap and $300 licensing model have positioned it as the next major infostealer of 2025, one that combines speed, stealth, and precision theft across the modern web.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates