A comprehensive research study has uncovered alarming security vulnerabilities in popular VPN applications, revealing that seemingly distinct providers share not only common ownership but also dangerous security flaws that compromise user privacy.
The investigation identified three families of VPN providers whose combined download counts exceed 700 million on the Google Play Store, all harboring critical vulnerabilities that allow attackers to decrypt user traffic.
The research builds upon previous investigations that linked VPN providers Innovative Connecting, Autumn Breeze, and Lemon Clove to Chinese security firm Qihoo 360, which the United States government sanctioned for its connections to the People’s Liberation Army.
However, this new study expands the scope significantly, identifying additional provider families through sophisticated analysis of business filings, Android APK files, and network infrastructure.
Hard-Coded Credentials Expose Millions of Users
The most concerning finding involves hard-coded Shadowsocks passwords embedded directly in the VPN applications’ code.
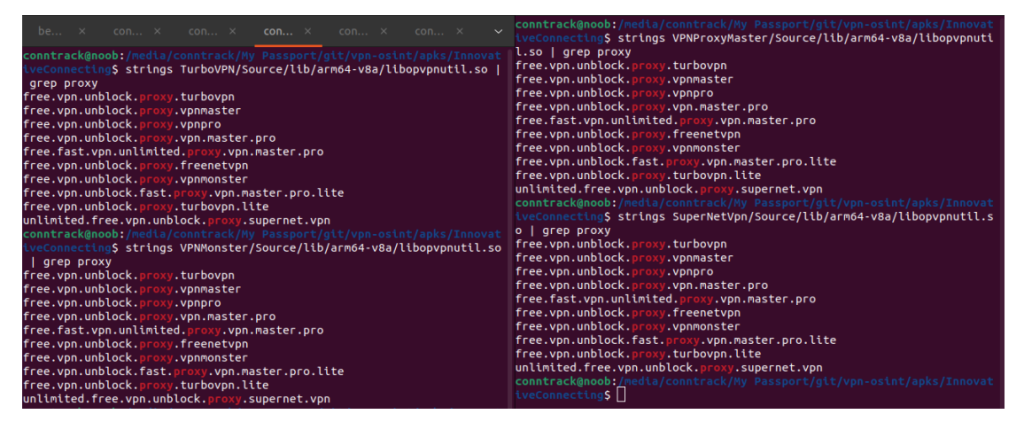
Family A, comprising eight applications such as TurboVPN, VPN Monster, and Snap VPN, contains identical hard-coded passwords in encrypted configuration files.
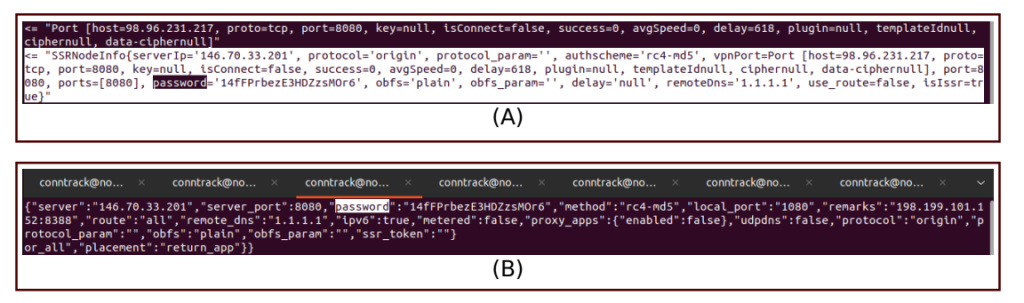
dump for the VPNMonster process (bottom).
These credentials are stored in the assets/server_offline. The file is encrypted using AES-192-ECB, but the application itself deterministically generates the decryption key.
“An attacker can use these credentials to decrypt all of the traffic for all of the clients of these providers,” the researchers warn.
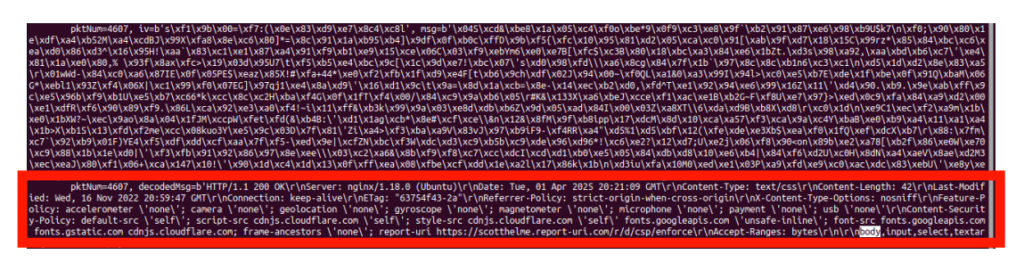
traffic; lower, encircled in red: decrypted traffic.
The study demonstrated this vulnerability by successfully intercepting and decrypting live traffic from affected applications, showing how network eavesdroppers could access users’ supposedly protected communications.
Family B providers, including Global VPN and XY VPN, exhibit similar vulnerabilities with obfuscated passwords stored in the libcore.so shared library.
Each application in this family offers 33 built-in servers with 19 open ports, all using the same compromised authentication system.
Shared Infrastructure Reveals Hidden Connections
The research employed novel forensic techniques to map relationships between supposedly independent VPN providers. By analyzing shared cryptographic credentials, the team confirmed that different providers operate identical server infrastructure.
They successfully established connections to servers using credentials extracted from one provider’s application to access another provider’s services.
Additional evidence of shared ownership includes nearly identical decompiled Java code, shared libraries, and assets across different applications.
The researchers found characteristic files like aaa_new.png, cert.pem, and proxy.builtin present across multiple seemingly unrelated VPN applications.
Beyond the hard-coded password vulnerabilities, all identified applications suffer from blind in/on-path attack susceptibilities, weak encryption implementations using deprecated ciphers like RC4-MD5, and unauthorized location data collection despite privacy policy claims to the contrary.
These findings highlight the critical importance of ownership transparency in the VPN ecosystem and demonstrate how deceptive business practices often correlate with compromised security implementations.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates