Security researchers from Truesec have uncovered a large-scale campaign distributing a weaponized PDF editor known as AppSuite PDF Editor, later revealed to be a delivery mechanism for the TamperedChef information-stealing malware.
The operation, which overlaps with earlier findings from Expel, employed aggressive advertising tactics, including Google Ads, to lure unsuspecting users into downloading the trojanized utility.
The installer, disguised as PDF Editor.exe, carried the following known hash signatures:
- MD5: 6fd6c053f8fcf345efaa04f16ac0bffe
- SHA1: 2ecd25269173890e04fe00ea23a585e4f0a206ad
- SHA256: cb15e1ec1a472631c53378d54f2043ba57586e3a28329c9dbf40cb69d7c10d2c
Once launched, the installer first displayed a standard end-user license agreement (EULA) before signaling installation progress to hxxp://inst.productivity-tools.ai/status/.
It then fetched a secondary executable from hxxp://vault.appsuites.ai/AppSuites-PDF-1.0.28.exe, completing its setup and establishing persistence via registry modifications.
Hidden Persistence and Malicious Activation
Although the PDF editor initially appeared benign, its codebase contained hidden instructions that periodically referenced a JavaScript payload to update command-line arguments (--cm) controlling its behavior.
These arguments included modes like --install, --enableupdate, and the more concerning --fullupdate, which triggered malicious functionality.
On August 21, 2025, Truesec observed widespread activation: compromised systems began to receive TamperedChef’s core modules. Persistence was reinforced through the registry key:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\PDFEditorUpdater
executing with PDF Editor.exe --cm=--fullupdate.
Once activated, the malware harvested sensitive data, targeting browser credential databases via Windows DPAPI. It forcibly terminated browser processes such as Chrome and Edge, likely to unlock files and ensure unimpeded access to stored credentials and cookies.
Industrialized Malware Distribution Tactics
The timing of the campaign is notable. Domains central to the distribution were registered around June 26, 2025, providing nearly two months of “grace period” before the malware’s destructive capabilities were unleashed, mirroring the 60-day life cycle of a typical ad campaign.
This deliberate staging maximized the user base before activation. The malware was also digitally signed using certificates from multiple shell companies, for example, ECHO Infini SDN BHD and GLINT By J SDN.
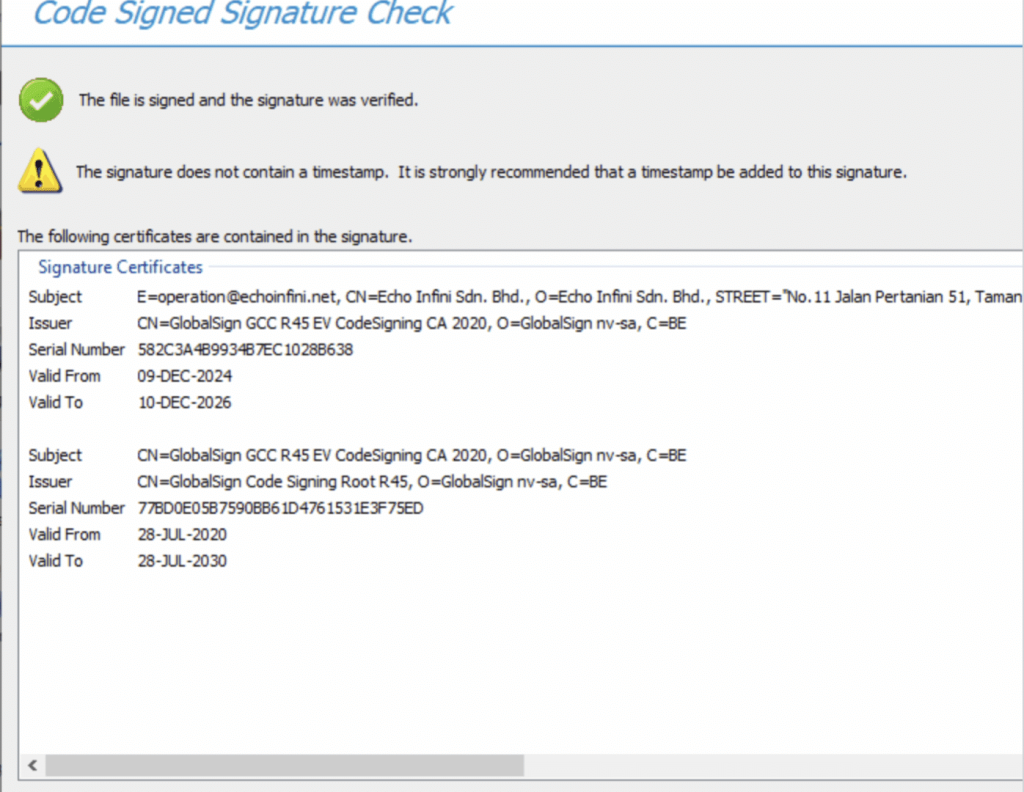
BHD, whose websites appear to be AI-generated and share standard addresses. In some cases, the installer bundled a re-signed version of the open-source tool Elevate.exe, potentially to enable privilege escalation at a later stage.
Analysis further ties this group to the earlier distribution of questionable software, such as OneStart and Epibrowser, which were connected to the same command-and-control networks as TamperedChef, implying a longstanding operation that has been active since at least 2024.
A Growing Supply-Chain Style Threat
This campaign highlights the risks associated with downloading seemingly harmless productivity software from unknown vendors. By leveraging trusted-looking digital certificates and Google’s ad ecosystem, the attackers masked their malicious intent until activation, compromising corporate environments across Europe.
Security experts urge vigilance in software vetting and recommend reporting suspicious campaigns to both local CERTs and platforms such as Google to reduce exposure and mitigate further attacks.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates