A recent malvertising campaign has weaponized Bing search ads to deliver trojanized versions of the PuTTY terminal emulator, leading unsuspecting users, including privileged administrators, into a dangerous compromise chain.
An investigation by LevelBlue’s Managed Detection and Response (MDR) Security Operations Center uncovered how a fake download of PuTTY escalated into system persistence, credential theft attempts, and targeted Active Directory attacks.
Malvertising Disguise: PuTTY as a Trap
Threat actors crafted fraudulent ads that appeared when users searched for terms like “PuTTY download” or “PuTTY plink download.”
These campaigns directed traffic to look‑alike websites such as puttyy[.]org, puttysystems[.]com, and putty[.]network, where a trojanized PuTTY executable awaited.
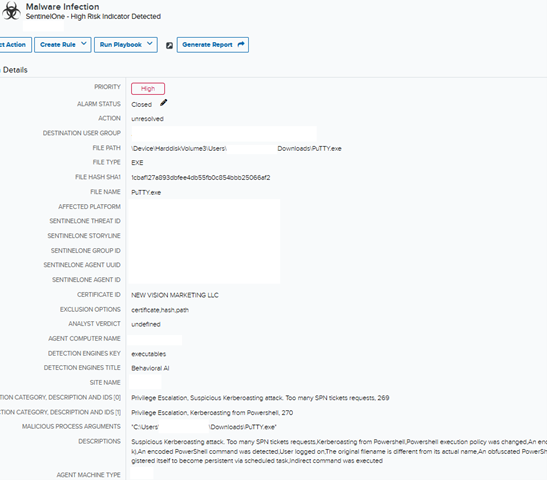
Unlike the legitimate tool maintained by the official PuTTY Project, these files bore misleading signatures, one notable example signed by “NEW VISION MARKETING LLC,” which was an immediate red flag.
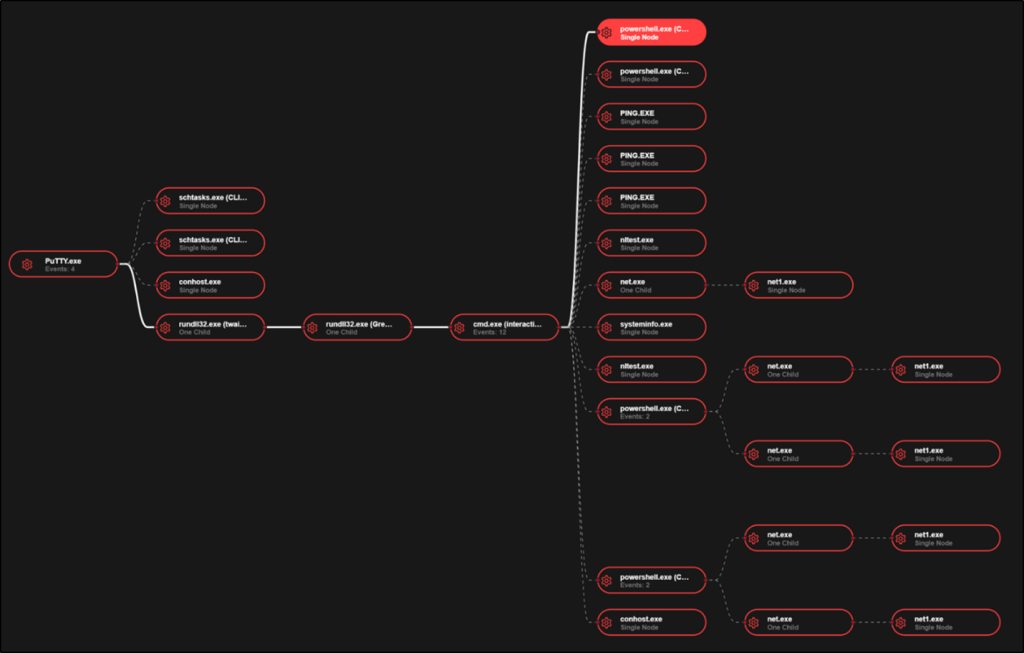
Once victims executed the malware, it established persistence by creating scheduled tasks under names like “Security Updater” or “FireFox Agent INC.” These tasks continuously launched malicious DLL files, including twain_96.dll and green.dll.
Analysis confirmed these components as variants of the Broomstick/Oyster malware family, known for enabling remote command execution, persistence through rundll32.exe, and communication with hardcoded command‑and‑control servers.
SentinelOne telemetry further revealed that the malicious PuTTY initiated outbound connections to compromised infrastructure, spawned cmd.exe for reconnaissance, and facilitated hands‑on‑keyboard intrusion techniques favored by ransomware operators.
Kerberos Abuse: In‑Memory Kerberoasting Attacks
Beyond persistence, the attackers employed a streamlined PowerShell script to conduct Kerberoasting entirely in memory. The script borrowed elements from red‑team frameworks such as PowerSploit’s Invoke‑Kerberoast but avoided disk artifacts, maximizing stealth.
By loading .NET assemblies to request service tickets, the attackers exploited environments still relying on weak RC4‑HMAC encryption for Kerberos authentication.
Directory queries identified accounts with Service Principal Names, and tickets were then requested, extracted, and parsed into hashes directly compatible with cracking tools like Hashcat.
Event logs within the affected environment reflected RC4-HMAC-encrypted ticket issuance, confirming that attackers had positioned themselves to brute‑force valuable service account credentials.
Since service accounts are frequently highly privileged within Active Directory, the compromise of such credentials could enable lateral movement and rapid escalation across enterprise systems.
Containment, Lessons, and Persistent Risks
Upon detection, the LevelBlue SOC moved quickly to disconnect the impacted endpoints from the network, disable compromised accounts, and conduct fleet‑wide hunts for related indicators of compromise.
Custom SentinelOne detection rules were deployed to proactively identify persistence mechanisms associated with this campaign, while remediation guidance was provided to affected customers.
However, reinvestigation revealed new malicious ads and payloads surfacing only days after takedowns had been issued, pointing toward the resilience of adversaries exploiting weak verification in online advertising platforms.
For defenders, the case reinforces three critical imperatives: ensure that privileged staff use only vetted and centrally managed administrative tools, enforce stronger Kerberos configurations that mandate AES encryption, and maintain continuous visibility into anomalous endpoint activity.
This malvertising campaign demonstrates that even familiar and trusted applications such as PuTTY can be subverted to serve as entry points for significant Active Directory compromise.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates