Cybersecurity firm Radware has released alarming data showing that the first half of 2025 marked an unprecedented escalation in digital threats across multiple attack vectors.
Web DDoS attacks surged 39% compared to the second half of 2024, with the second quarter alone witnessing a record-breaking 54% quarter-over-quarter spike.
Application-layer attacks increased by 33%, while bad bot activity jumped 57%, signaling a fundamental shift in the cyber threat landscape.
Attack Patterns Evolve Toward AI-Enhanced Automation
The data reveals a significant tactical shift among threat actors, who are increasingly favoring smaller, sustained attacks under 100,000 requests per second (RPS) rather than massive volumetric assaults.
This change reflects the growing influence of automated, generative AI-enhanced attack tools that have democratized DDoS capabilities among loosely coordinated and emerging threat actors.
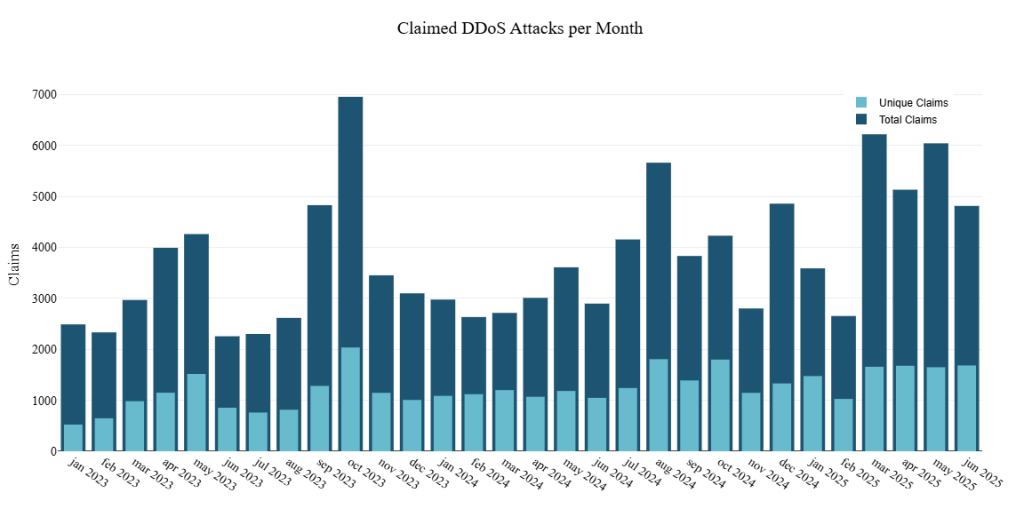
Despite the trend toward smaller attacks, peak incidents reached 10 million RPS, demonstrating that high-end capabilities remain accessible to sophisticated adversaries.
Network-layer (L3/L4) DDoS attacks experienced a dramatic resurgence, increasing 85.5% compared to the second half of 2024, with the average Radware customer facing 7,281 mitigation events per quarter by Q2 2025 a staggering 485% increase from Q1 2022.
The amplification attack landscape was dominated by DNS and NTP vectors, which generated 89.2% of total attack volume. Notably, the Session Initiation Protocol (SIP) emerged as a key target, representing a significant risk to VoIP and communications infrastructure.
Regional Distribution and Hacktivist Activity Intensify
Geographically, the EMEA region continued absorbing over half of all Web DDoS attacks, while the APAC region experienced notable growth in targeting. North America bore the brunt of network DDoS activity, accounting for nearly 46% of all attacks, primarily driven by UDP-based volumetric floods.
Hacktivist activity maintained steady momentum with nearly 9,200 DDoS attacks claimed on Telegram—a 62% increase over the first half of 2024.
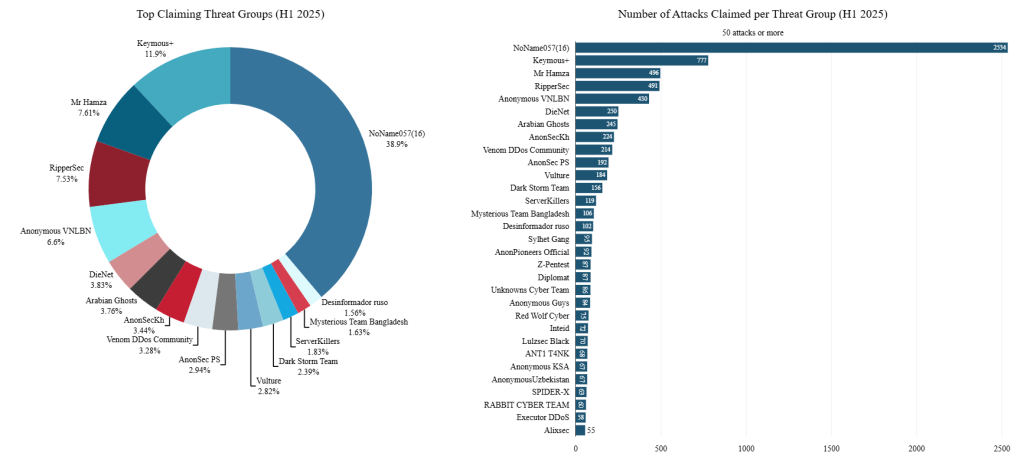
Europe remained the primary target at 45% of all claims, with Israel, the United States, and Ukraine topping the list of most-targeted nations. The notorious NoName057(16) group retained dominance, responsible for nearly 40% of all hacktivist claims.
Government services remained the primary sectoral focus, accounting for 39% of all hacktivist attacks, while manufacturing, finance, and education sectors also faced significant targeting.
The report’s methodology drew from Radware’s cloud scrubbing centers and managed devices, alongside analysis of hacktivist communications across nearly 650 Telegram channels, providing comprehensive visibility into the evolving threat landscape.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates