Security researchers have uncovered critical vulnerabilities in instant messaging applications that could allow attackers to gain complete control over target devices through specially crafted messages.
The DARKNAVY research team’s comprehensive analysis reveals how malicious actors can exploit client-side attack surfaces in popular messaging platforms like WeChat, potentially compromising billions of users worldwide without requiring any user interaction.
The newly identified attack vectors primarily target the file processing capabilities built into instant messaging clients.
Researchers demonstrate how attackers can craft malicious files disguised as legitimate content to achieve remote code execution.
The technique mirrors the notorious CVE-2019-8641 vulnerability discovered in Apple’s iMessage platform, where a specially designed file could grant attackers complete control over target iPhones without any user interaction.
WeChat’s file processing system, designed to enhance user experience through file previews and content extraction, creates significant security exposure when handling untrusted content.
Attackers can exploit these processing functions by embedding malicious code within seemingly harmless files, including images, documents, or multimedia content.
The attack becomes particularly dangerous because modern IM clients automatically parse rich media content, making the exploitation completely transparent to victims.
The research also highlights vulnerabilities in custom protocol handling, where attackers abuse URL validation weaknesses to redirect users to phishing sites or trigger unauthorized actions.
The weixin:// protocol used by WeChat for in-app navigation represents another potential attack vector when combined with malicious file processing.
New iPhone Vulnerability
The security implications extend far beyond individual applications, affecting the broader instant messaging ecosystem that serves as “digital arteries” for modern society.
These platforms handle critical activities including social interactions, financial transactions, and business communications for billions of users globally, making successful attacks particularly devastating.
Browser engine vulnerabilities compound the security risks, with researchers identifying that CVE-2023-41064 and CVE-2023-4863 in the libwebp component affected multiple mainstream IM applications including WeChat, DingTalk, and QQ.
The embedded browser components in these applications often lag behind official releases, potentially exposing users to known vulnerabilities that remain unpatched.
Mini-program ecosystems introduce additional attack surfaces, as third-party developers receive extensive system permissions including file system access, sensor invocation, and API calls.
Malicious mini-programs can leverage these permissions to conduct sophisticated attacks if proper permission management is lacking.
Mitigations
WeChat has implemented several security mechanisms to address these vulnerabilities, including multi-process sandboxing that isolates rendering processes from the main application.
Security experts recommend that users maintain updated application versions and exercise caution when opening files from unknown sources, while organizations should implement comprehensive security monitoring for instant messaging platforms.
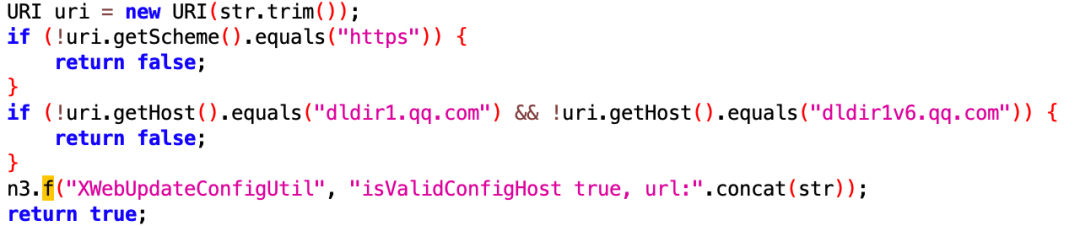
The platform employs strict validation for sensitive operations, restricting debugging functions and enforcing HTTPS-only protocols with domain validation for configuration changes.
The application uses cloud-based permission arrays to control JSBridge interface access, providing fine-grained control over webpage capabilities.
Additionally, WeChat’s mini-program architecture separates rendering and logic layers into isolated threads, preventing cross-layer privilege escalation attacks.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.