A critical Windows shortcut vulnerability is enabling advanced persistent threat actors to execute covert malware deployment campaigns against diplomatic and government entities worldwide.
Designated as ZDI-CAN-25373 and disclosed in March 2025, the flaw allows threat actors to disguise malicious commands within Windows LNK files by manipulating whitespace padding in the COMMAND_LINE_ARGUMENTS structure.
This UI misrepresentation technique has been rapidly adopted by multiple nation-state espionage groups from North Korea, China, Russia, and Iran for data theft and intelligence collection operations.
The vulnerability exploits Windows shortcut file handling by inserting excessive whitespace characters into the command-line argument structure, effectively hiding malicious PowerShell commands from user inspection while maintaining full execution capability.
When victims open what appears to be a legitimate document shortcut themed around diplomatic meetings, conference agendas, or policy documents, the concealed commands automatically execute in the background.
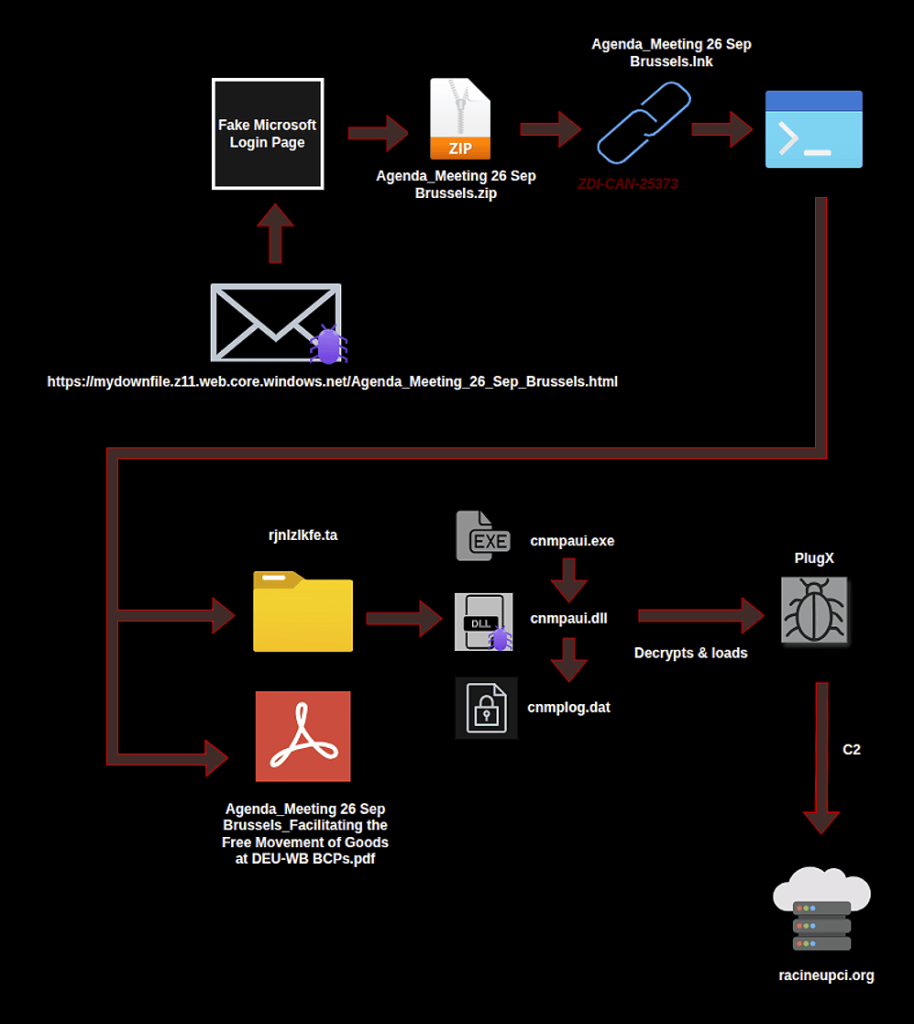
The technique proves particularly effective in spearphishing campaigns, where threat actors craft LNK files with names like “Agenda_Meeting 26 Sep Brussels.lnk” to leverage authentic details of a diplomatic event and bypass user suspicion.
Technical Exploitation Mechanics and Attack Chain Deployment
The exploitation methodology demonstrates sophisticated multi-stage execution designed to evade endpoint detection systems. Upon execution, weaponized LNK files run obfuscated PowerShell commands that decode embedded TAR archives stored within the shortcut itself.
These archives contain three critical components deployed through DLL side-loading: a legitimate digitally signed Canon printer assistant utility (cnmpaui.exe), a malicious loader DLL (cnmpaui.dll), and an RC4-encrypted payload file (cnmplog.dat) containing remote access trojan malware.
The legitimate Canon executable, signed with a valid certificate issued by Symantec Class 3 SHA256 Code Signing CA, provides the attack chain with a trusted process context.
Although the certificate expired in April 2018, Windows continues to trust binaries with valid timestamps proving they were signed during the certificate’s validity period.
When the signed executable launches, Windows’ DLL search order behavior causes it to load the malicious cnmpaui.dll from the current directory before checking system directories.
This malicious DLL then decrypts the payload using a hardcoded 16-byte RC4 key and loads the final-stage malware in-memory directly into the legitimate process’s address space, enabling execution within a trusted context that circumvents reputation-based security controls.
The attack demonstrates rapid vulnerability weaponization timelines concerning security professionals. Multiple advanced persistent threat groups integrated ZDI-CAN-25373 exploitation into operational tradecraft within six months of the March 2025 public disclosure.
Chinese-affiliated threat actor UNC6384 deployed the technique against Hungarian and Belgian diplomatic entities throughout September and October 2025, while parallel campaigns targeted Serbian government agencies and Italian diplomatic organizations using identical exploitation methodologies.
The threat actors maintain command-and-control infrastructure across multiple domains, including racineupci[.]org, dorareco[.]net, and naturadeco[.]net, all configured to communicate over port 443 to blend with legitimate encrypted web traffic.
Microsoft has not released an official patch for ZDI-CAN-25373 as of October 2025.
Organizations should implement immediate defensive measures, including disabling automatic LNK file resolution in Windows Explorer, blocking identified command-and-control infrastructure at network perimeters, and conducting endpoint searches for Canon printer utilities executing from non-standard directories, such as user AppData folders.
The persistent exploitation of this vulnerability across multiple nation-state campaigns underscores the critical need for proactive threat hunting and enhanced monitoring of Windows shortcut file execution, particularly in the diplomatic and government sectors, where targeted intelligence collection operations are most concentrated.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates