A cybersecurity researcher has disclosed a novel User Account Control (UAC) bypass method that exploits Windows’ built-in Private Character Editor, allowing attackers to gain elevated privileges without user consent.
The technique, published by Matan Bahar, a Red Team Security Researcher at White-Hat, demonstrates how legitimate Windows utilities can be weaponized to circumvent critical security mechanisms.
Exploiting Windows Font Editor for Privilege Escalation
The newly discovered technique leverages eudcedit.exe, Windows’ Private Character Editor located in C:\Windows\System32, which is designed for creating and editing user-defined characters (EUDC: End-User Defined Characters).
These custom glyphs can be mapped to Unicode code points for use in documents and applications. However, Bahar’s research reveals how this seemingly innocuous utility can serve as a vector for UAC bypass.
The exploit works by taking advantage of eudcedit.exe’s application manifest configuration, which contains specific instructions for Windows to elevate the program automatically.
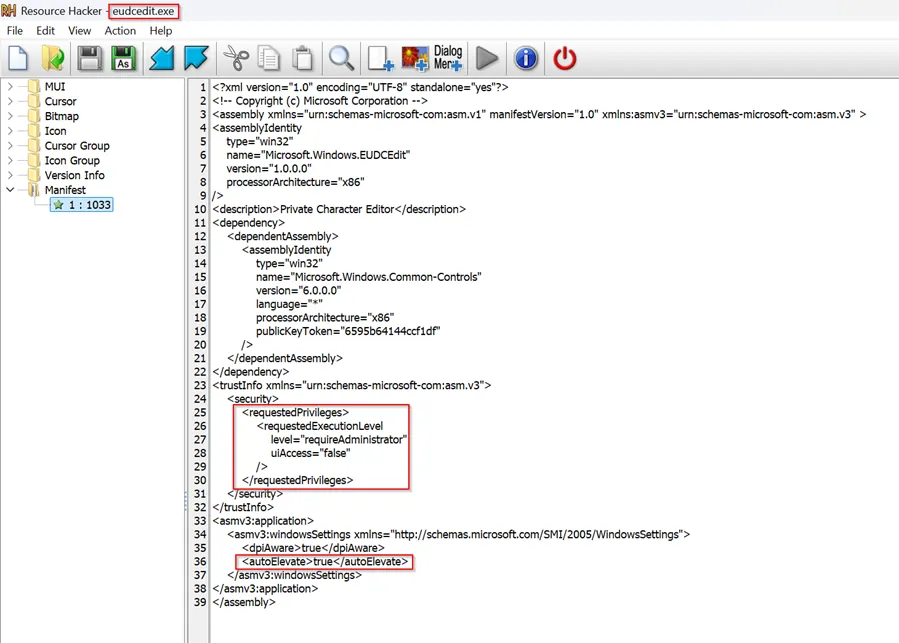
Two critical tags in the manifest enable this behavior: <requestedExecutionLevel level="requireAdministrator" /> instructs Windows to run the binary with full administrative rights, while <autoElevate>true</autoElevate> directs the system to bypass the UAC prompt for trusted binaries when launched by users already in the Administrators group.
When these manifest entries are combined with UAC configured permissively (such as “Elevate without prompting”), Windows launches eudcedit.exe immediately with high integrity privileges without displaying a UAC dialog box.
This creates an opportunity for attackers who have already achieved initial access to escalate their privileges seamlessly.
Attack Methodology and Security Implications
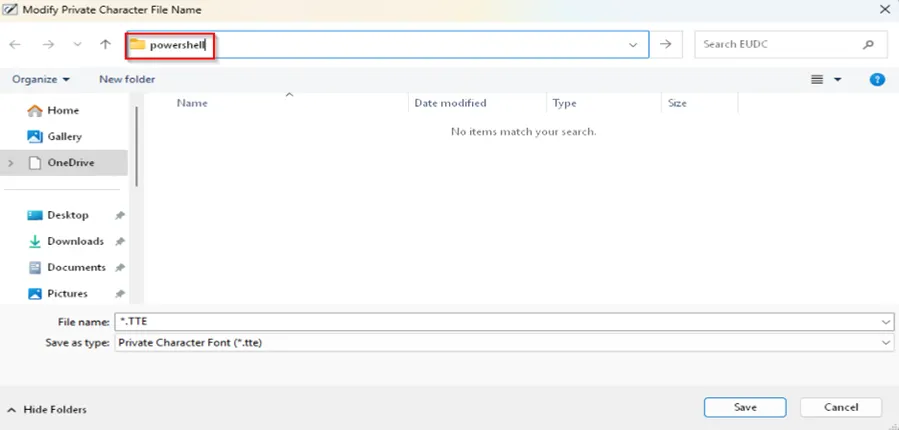
The attack sequence involves launching eudcedit.exe, navigating to the File menu, selecting “Font Links,” choosing the second option, and clicking “Save As.”
In the resulting dialog window, typing “PowerShell” completes the UAC bypass, granting the attacker an elevated PowerShell session with administrative privileges.
This technique is particularly concerning because it exploits a legitimate Windows utility that users and security software typically trust.
Unlike traditional UAC bypass methods that might trigger security alerts or require complex exploitation techniques, this approach leverages the operating system’s trust mechanisms against itself.
The discovery highlights ongoing challenges in Windows security architecture, where legitimate administrative tools can be repurposed for malicious activities.
While UAC was introduced in Windows Vista as a gatekeeper to prevent unauthorized privilege escalation attempts, techniques like this demonstrate that determined attackers can still find ways to circumvent these protections.
Security professionals should be aware of this technique when conducting threat hunting activities and consider implementing additional monitoring for unusual eudcedit.exe process execution patterns.
Organizations may also need to reassess their UAC configuration policies to minimize exposure to such bypass techniques while maintaining operational functionality.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates