A sophisticated zero-day exploit targeting WinRAR, one of the world’s most popular file compression utilities, has emerged on dark web marketplaces, highlighting the persistent vulnerabilities in widely used software applications.
The threat actor, operating under the pseudonym “zeroplayer,” is offering an exclusive remote code execution (RCE) vulnerability for $80,000, representing a significant escalation in the underground exploit market.
Technical Analysis of the RCE Vulnerability
According to the report from ThreatMon, the zero-day exploit demonstrates a critical security flaw in WinRAR’s file processing mechanisms, potentially allowing attackers to execute arbitrary code on target systems.
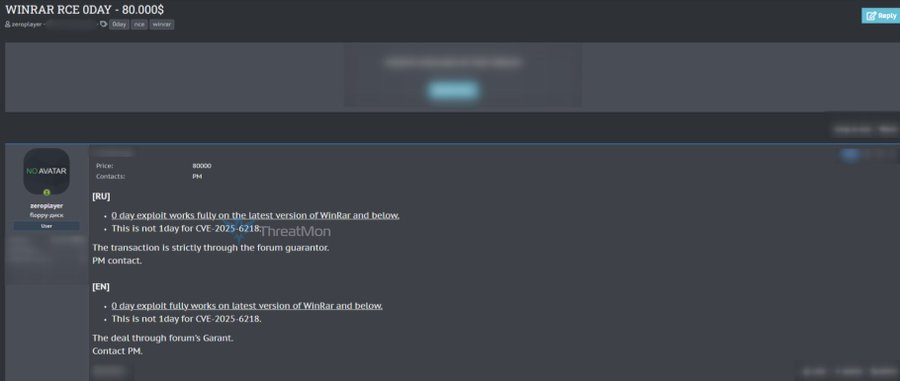
Unlike the previously disclosed CVE-2025-6218 vulnerability, this newly discovered exploit represents a distinct attack vector that affects both current and legacy versions of the software.
The remote code execution capability enables attackers to gain complete control over compromised systems by exploiting buffer overflow conditions or memory corruption vulnerabilities within WinRAR’s parsing engine.
Security researchers emphasize that RCE exploits are perilous because they can be triggered through seemingly innocent file operations.
When victims attempt to extract or view malicious archive files, the exploit can execute payload code with the same privileges as the user running WinRAR, potentially leading to system compromise, data theft, or malware installation.
Underground Market Dynamics and Pricing Structure
The $80,000 price point reflects the exploit’s perceived value in the cybercriminal ecosystem, where zero-day vulnerabilities command premium prices based on their target software’s ubiquity and the difficulty of discovery.
WinRAR’s extensive user base, estimated at over 500 million installations worldwide, makes this exploit particularly attractive to threat actors seeking maximum impact potential.
The pricing also indicates the exploit’s exclusivity, as “zeroplayer” is likely offering limited access to prevent rapid detection and patching by security vendors.
This scarcity model is common in zero-day markets, where sellers balance profit maximization against the risk of exposure through widespread distribution.
Security Implications and Mitigation Strategies
Organizations and individual users face immediate risks from this undisclosed vulnerability, as no official patches are currently available.
The exploit’s compatibility with multiple WinRAR versions suggests a fundamental architectural flaw that may require significant code restructuring to address properly.
Cybersecurity experts recommend implementing defense-in-depth strategies, including application sandboxing, endpoint detection and response (EDR) solutions, and strict file handling policies.
Network administrators should consider temporarily restricting WinRAR usage in critical environments until official security updates become available.
The emergence of this zero-day exploit underscores the ongoing challenges in software security, particularly for applications with extensive file format support and complex parsing capabilities that create numerous potential attack surfaces.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates