A new campaign attributed to the South Asian threat actor Bitter (APT-Q-37) has been uncovered by Qi’anxin Threat Intelligence Center, exposing a sophisticated multi-stage attack chain that leverages a WinRAR zero-day vulnerability to deploy custom C# backdoors for data theft and persistent access.
Dual Attack Vectors: Macros and Archive Exploits
Qi’anxin analysts discovered two distinct infection pathways used by Bitter to implant identical backdoors. In the first method, the attackers distribute a malicious Excel Add-In file named Nominated Officials for the Conference—xlam, which contains a VBA macro.
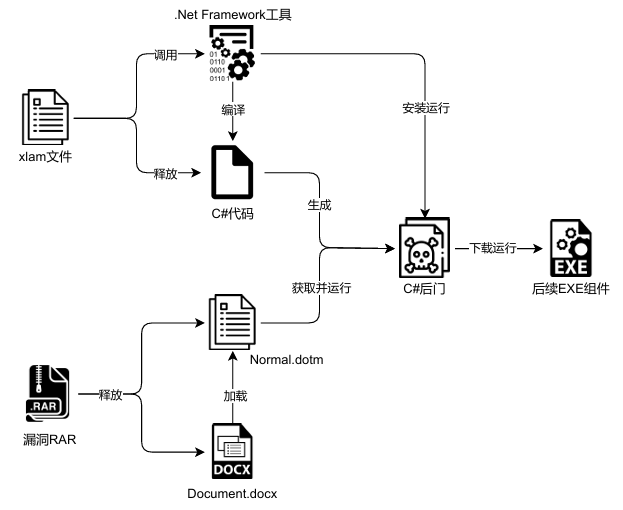
When macros are enabled, the script constructs a file named cayote.log holding Base64-encoded C# source code. Using system tools csc.exe and InstallUtil.exe from the .NET Framework, the macro compiles and installs the resulting payload vlcplayer.dll into C:\ProgramData\USOShared.
The macro script creates persistence by generating kefe.bat in the Startup folder, which launches a scheduled task contacting hxxps://www.keeferbeautytrends.com/d6Z2.php?rz=, a domain tied to prior Bitter activities.
The second attack vector exploits a previously unknown WinRAR path traversal vulnerability, likely predating CVE-2025-8088.
The weaponized archive Provision of Information for Sectoral for AJK.rar attempts to overwrite the legitimate Normal. dotm template in *C:\Users<username>\AppData\Roaming\Microsoft\Templates*.
When victims decompress the archive in specific directories, the malicious Normal, dotm replaces Word’s default template, ensuring malware execution each time Word runs.
Upon triggering, macros are embedded in Normal. dotm connects to \koliwooclients.com\templates, retrieving winnsc.exe, a compiled backdoor identical to vlcplayer.dll, underscoring a shared origin.
C# Backdoor and Command Infrastructure
The Bitter group’s backdoor exhibits advanced modular control through encrypted HTTP communications.
The malware collects system details, OS version, host name, and user directory before transmitting them via POST to hxxps://msoffice.365cloudz.esanojinjasvc.com/cloudzx/msweb/drxbds23.php. The C2 server responds with parameters dictating further payload downloads and execution routines.
Follow-up network activity was observed toward additional domains, including teamlogin.esanojinjasvc.com, used for receiving execution status and transferring secondary executables.
Evidence links all infrastructure to the esanojinjasvc.com domain cluster registered in April 2025, aligning with other Bitter-controlled assets.
Qi’anxin’s assessment concludes that Bitter is testing new infection techniques, combining software compilation abuse with archive exploitation for stealthy persistence. The group continues to refine its tradecraft against high-value targets across government, defense, and energy sectors.
Qi’anxin advises users to update WinRAR, disable macro execution, avoid opening unsolicited attachments, and analyze suspicious files using their sandbox at sandbox.ti.qianxin.com.
IOC
MD5
b165b489c5f8c4e136364664502d68f1
18164f7b3d320a79b6db634f718a1095
f6f2fdc38cd61d8d9e8cd35244585967
C&C
keeferbeautytrends.com
koliwooclients.com
esanojinjasvc.com
URLs
hxxps://msoffice.365cloudz.esanojinjasvc.com/cloudzx/msweb/drxbds23.php
hxxps://msoffice.365cloudz.esanojinjasvc.com/cloudzx/msweb/drdxcsv34.php
hxxps://msoffice.365cloudz.esanojinjasvc.com/cloudzx/msweb/drxcvg45.php
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates