A critical vulnerability in the Case Theme User WordPress plugin is under active exploitation, allowing unauthenticated attackers to bypass authentication and log in as arbitrary users, including administrators, simply by knowing or guessing a victim’s email address.
Disclosed on August 22, 2025, and assigned CVE-2025-5821 with a CVSS 3.1 score of 9.8 (Critical), this flaw affects all plugin versions up to and including 1.0.3.
With over 12,000 active installations and widespread inclusion in premium themes on ThemeForest, the impact is significant for sites relying on the plugin’s Facebook social login functionality.
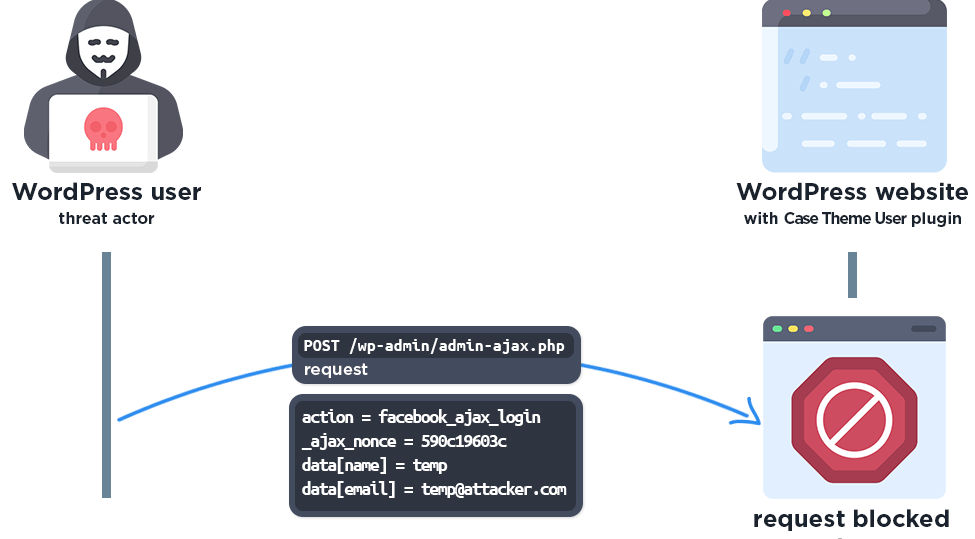
The core issue resides in the facebook_ajax_login_callback() function within the Case_Theme_User_Ajax class. Upon receiving AJAX requests at wp-admin/admin-ajax.php, the plugin verifies a nonce and checks for required data[name] and data[email] parameters.
It then constructs a temporary user with a predictable username and password derived from the Facebook display name. If the sanitized username already exists, the plugin attempts to log in the user by matching both username and generated password.
Crucially, it then retrieves the user account by email and sets the authentication cookie for that account without verifying ownership of the email address.
This logic enables an attacker first to register a temporary account using any email address, and subsequently, upon a request specifying a victim’s email address, gain immediate access to the victim’s account, regardless of the account’s privileges.
Exploit Timeline and Attack Data
The patch was released on August 13, 2025, and Wordfence Premium, Care, and Response customers received firewall rules on June 10, 2025, 30 days ahead of free users on July 10, 2025.
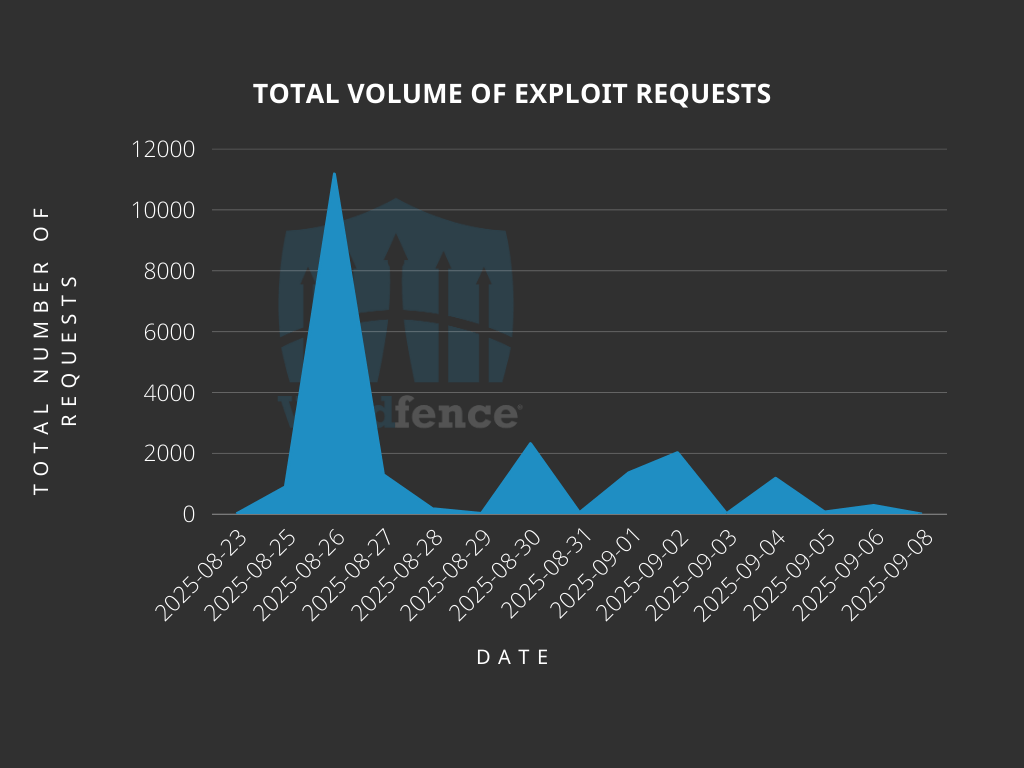
Attackers, however, began targeting the flaw as early as August 23, 2025. Wordfence Firewall has since blocked over 20,900 exploit attempts. Notable spikes in activity occurred on August 26, August 30, and September 2, indicating coordinated mass-scanning efforts.
Standard administrative email addresses such as [email protected], [email protected], and [email protected] feature prominently in attack logs, reflecting threat actors’ attempts to enumerate valid emails before exploitation.
The most active sources of blocked requests include IPv6 address 2602:ffc8:2:105:216:3cff:fe96:129f (over 6,300 attempts), 146.70.186.142 (over 5,700), 107.175.179.8 (over 5,000), 2602:ffc8:2:105:216:3cff:fe40:4b78 (over 2,400), and 89.117.42.68 (over 500).
Site administrators should review logs for AJAX requests from these addresses as potential indicators of attempted exploitation.
Site owners must update Case Theme User to version 1.0.4 immediately to eliminate this authentication bypass flaw. Even with a firewall rule in place, continued reliance on an unpatched version risks site compromise, data theft, or complete administrative takeover.
Forward this advisory to colleagues and clients using premium themes bundled with Case Theme User to ensure broad awareness.

For sites suspected of compromise, Wordfence Care and Wordfence Response offer incident response and cleanup services, with 24/7 availability and rapid mitigation support. Continuous monitoring and timely patching remain essential to defend against evolving WordPress threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates