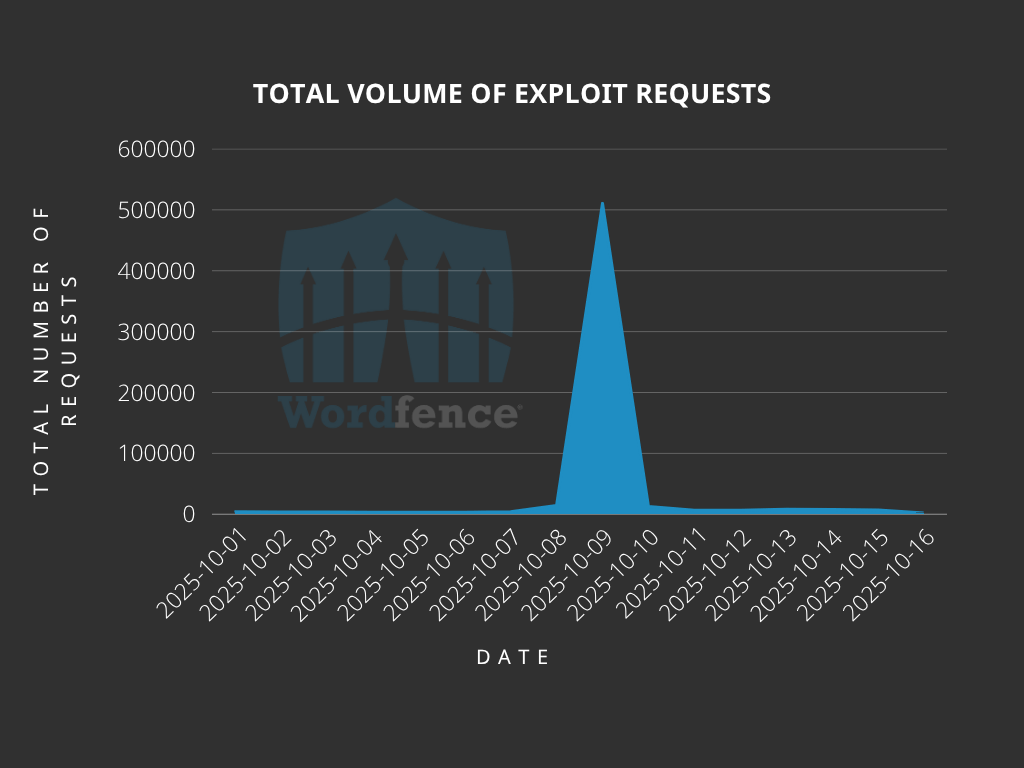
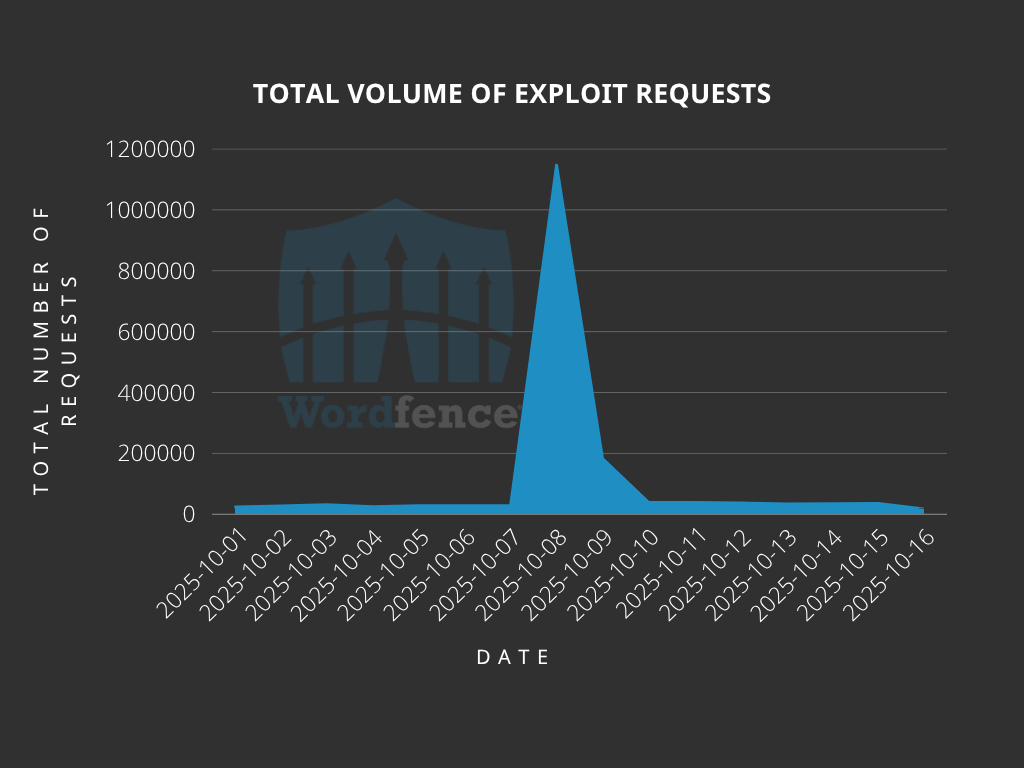
Critical vulnerabilities in two popular WordPress plugins are under active mass exploitation, with Wordfence blocking over 8.7 million attack attempts targeting arbitrary plugin installation flaws.
The security firm warns that threat actors launched their latest exploitation wave on October 8, 2025, nearly one year after the vulnerabilities were first disclosed and patched.
Missing Authorization Enables Unauthenticated Remote Code Execution
The vulnerabilities affect GutenKit and Hunk Companion, WordPress plugins with over 40,000 and 8,000 active installations, respectively.
Both flaws carry a critical CVSS score of 9.8 and allow unauthenticated attackers to install malicious plugins and execute remote code on vulnerable WordPress sites.
GutenKit versions up to 2.1.0 contain CVE-2024-9234, while Hunk Companion versions 1.8.4 and below are affected by CVE-2024-9707, with CVE-2024-11972 serving as a bypass for the initial patch attempt.
The root cause in both plugins stems from improperly configured REST API endpoints with missing capability checks.
GutenKit’s vulnerability exists in the install_and_activate_plugin_from_external() function, accessible via the gutenkit/v1/install-active-plugin REST endpoint, where the permission callback is set to __return_true in a dangerous way.
This configuration allows any unauthenticated visitor to invoke the endpoint and install plugins from remote sources. Similarly, Hunk Companion’s tp_install() function exposes the hc/v1/themehunk-import REST endpoint without proper authorization, enabling attackers to install arbitrary plugins from the WordPress repository.
Sophisticated Attack Campaign Delivers Multiple Backdoors
Analysis of actual exploit attempts reveals that attackers are deploying highly sophisticated malicious payloads disguised as legitimate plugins. One observed attack installed a GitHub package containing password-protected scripts with spoofed All in One SEO headers that automatically grant administrator access.
The payload also includes base64-encoded file management scripts that enable upload, deletion, and permission modification, along with heavily obfuscated PHP files designed to maintain persistent access.
Wordfence researchers identified a particularly deceptive file, vv.php, that starts with a valid PDF header but contains obfuscated PHP code capable of mass defacement, network sniffing, and remote code execution.
In attacks targeting Hunk Companion, threat actors attempt to install wp-query-console, a legitimate plugin that contains an unpatched remote code execution vulnerability, demonstrating their strategic approach when direct arbitrary file upload is unavailable.
The most aggressive attackers originate from IP addresses including 3.141.28.47 with 349,900 blocked requests against Hunk Companion, and 13.218.47.110 with 82,900 attempts against GutenKit.
Malicious payloads are hosted on compromised domains, including ls. fatec[.]info, dari-slideshow[.]ru, and file-sharing platform catbox[.]moe.
Wordfence Premium users received firewall protection on September 27 and October 10, 2024, while free version users gained protection after a 30-day delay on October 27 and November 9, 2024.
Despite these protections and available patches, the October 2025 exploitation wave demonstrates that thousands of sites remain vulnerable.
WordPress administrators must immediately update to GutenKit version 2.1.1 and Hunk Companion version 1.9.0, and audit their /wp-content/plugins directories for suspicious installations, including directories named “up,” “background-image-cropper,” “ultra-seo-processor-wp,” or “oke.”
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates