Security researchers at Zscaler ThreatLabz have uncovered YiBackdoor, a sophisticated backdoor malware family first observed in June 2025.
Exhibiting significant code overlaps with the IcedID and Latrodectus malware strains, YiBackdoor appears poised to serve as an initial access vector in ransomware campaigns, enabling threat actors to harvest system intelligence, exfiltrate data, and execute arbitrary commands on compromised hosts.
Technical Innovations Fueling Malicious Operations
YiBackdoor’s initialization phase begins by generating a host-tied mutex to prevent duplicate instances. If clear, the malware determines whether it is already running within a legitimate process by verifying its memory address against loaded DLL ranges.
Upon detecting an external execution context, YiBackdoor spawns a svchost.exe process and injects its own code into it.
The injection leverages a rare hook of the Windows API function RtlExitUserProcess, redirecting the call into the backdoor payload just as the process exits, an approach that may evade conventional endpoint security products.
Once injected, YiBackdoor establishes persistence by copying its DLL into a newly created directory under a pseudo-random name and registering itself via the Windows Run key using a registry value derived from a custom linear congruential generator seeded by the bot ID.
Following persistence, the malware self-deletes the original dropper to thwart forensic analysis.
YiBackdoor’s anti-analysis toolbox focuses on sandbox evasion. It dynamically resolves Windows API functions by hashing module exports, decrypts strings at runtime using XOR operations with unique per-string keys, and probes for virtualization with a two-phase timing check around CPUID instructions.
These techniques, combined with CPUID calls to detect known hypervisors (VMWare, Xen, KVM, VirtualBox, Hyper-V, Parallels), allow the backdoor to abort execution if it suspects a virtual environment.
Advanced Configuration and Modular Capabilities
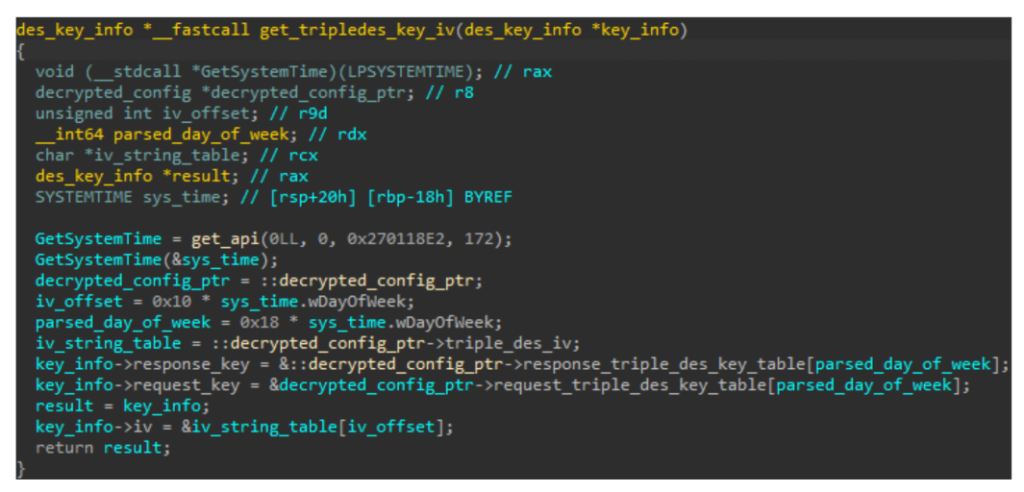
At runtime, YiBackdoor decrypts an embedded configuration blob, which contains up to 300 bytes of C2 addresses, three 64-byte key tables, an IV, two 32-bit URI values, and a 64-byte botnet identifier, using a bespoke byte-wise rotation and XOR algorithm.
The configuration determines C2 communication protocols (HTTP/HTTPS) and constructs dynamic URIs:
http(s)://C2_ADDRESS/BOT_ID/URI1/URI2
Network sessions employ TripleDES encryption keys and IVs derived from the bot ID and current day of week, ensuring daily key variation.
YiBackdoor sends encrypted, Base64-encoded JSON packets via HTTP GET under the X-tag header and parses similarly encrypted responses for incoming commands.
Supported commands include:
- systeminfo: Gathers OS details, running processes, network configuration, domain trusts, installed software, and shares.
- Screen: Captures and exfiltrates desktop screenshots.
- CMD/PWS: Executes arbitrary shell or PowerShell commands.
- Plugin/task: Dynamically installs or invokes plugins, extending functionality beyond the default command set.
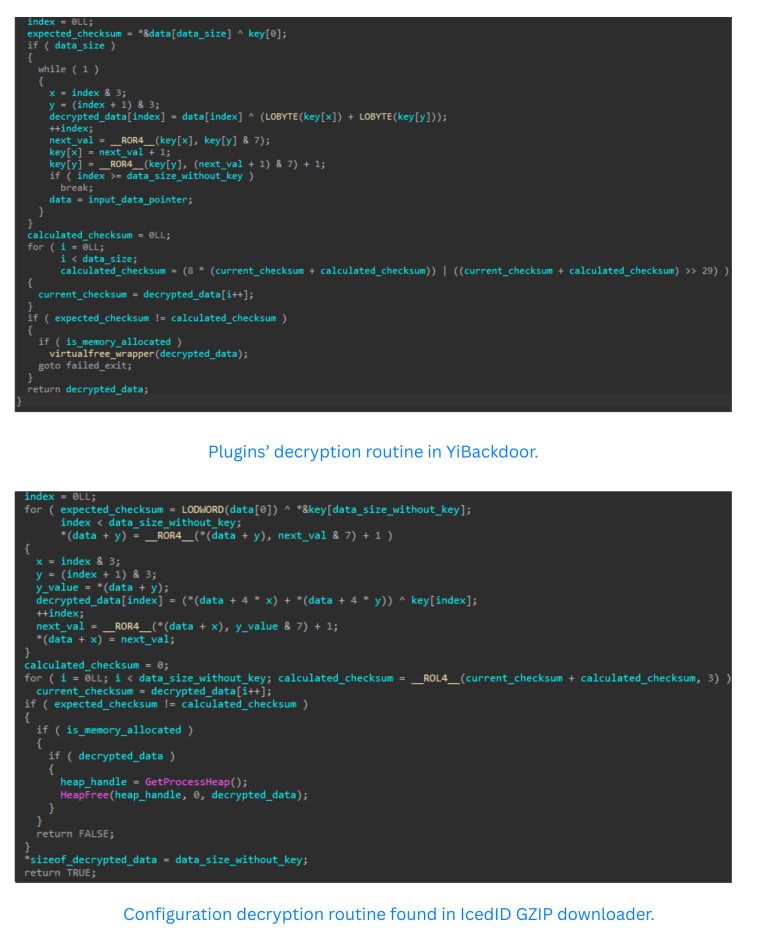
Plugins are received as encrypted .bin files, stored in the Windows temporary directory under randomized names, and decrypted using a multi-stage key rotation algorithm identical to IcedID’s decryption routine.
ThreatLabz analysts note that YiBackdoor’s limited deployment and local IP C2 defaults suggest an active development or testing phase is underway.
However, the observed code re-use from established banking and initial access malware underscores a high likelihood of adaptation in larger ransomware operations.
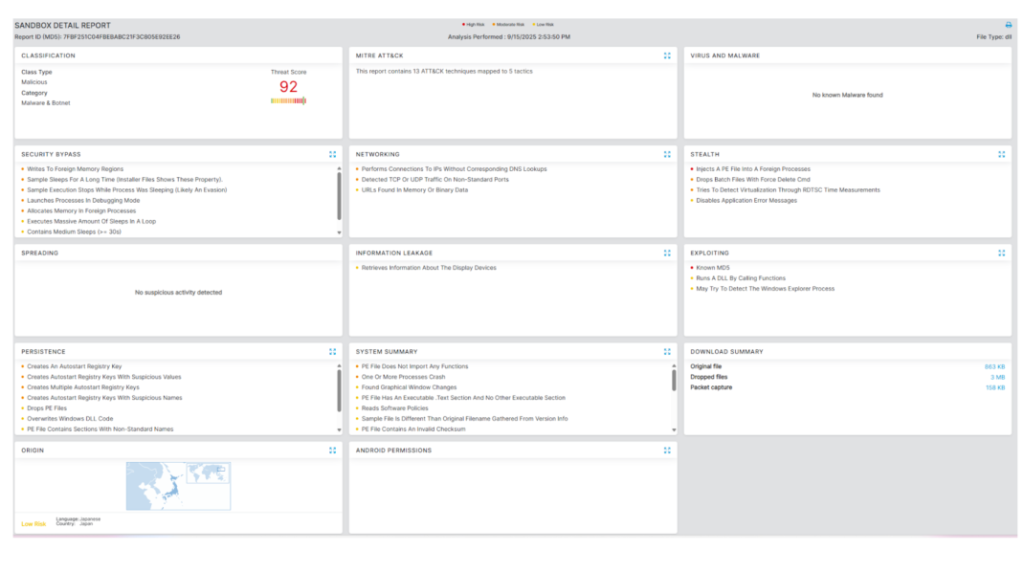
Zscaler Cloud Sandbox detections confirm that existing Zscaler protections can intercept YiBackdoor samples before host compromise, offering enterprises early warning and automated containment against this evolving threat.
Indicators Of Compromise (IOCs)
| Indicator | Description |
|---|---|
| af912f6f4bea757de772d22f01dc853fc4d7ab228dc5f7b7eab2a93f64855fbe | YiBackdoor SHA256 |
| http://136.243.146[.]46:8898 | YiBackdoor C2 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates