Cybersecurity researchers at AhnLab Security Intelligence Center (ASEC) have discovered a sophisticated malware campaign targeting users seeking to download YouTube videos, distributing proxyware that steals internet bandwidth for profit.
The attack represents an evolution of previous proxyjacking campaigns that infected over 400,000 Windows systems globally.
The malicious scheme exploits users’ desire to download YouTube content by creating fake download websites that appear legitimate but serve as malware distribution points.
When users attempt to download videos, they are redirected to advertising pages or prompted to download malicious software disguised as legitimate tools.

GitHub-Based Distribution Network
The threat actors have established a sophisticated distribution infrastructure using GitHub as their primary malware hosting platform.
Multiple repositories containing malicious payloads have been identified, with the malware masquerading as “QuickScreenRecoder” (quick-screen-recorder.exe). Despite appearing as a simple installer, the executable triggers a complex PowerShell-based infection chain.
Once executed, the malware performs extensive sandbox and virtual machine detection to evade analysis. It subsequently downloads and installs NodeJS, retrieves malicious JavaScript code, and registers a scheduled task named “DefragDiskCleanup” to maintain persistence.

This JavaScript component establishes communication with command-and-control servers, transmitting system information and receiving additional PowerShell commands for proxyware installation.
Dual Proxyware Deployment Strategy
The campaign primarily deploys DigitalPulse proxyware, the same software used in previous large-scale proxyjacking operations.
However, researchers have also identified instances where Honeygain proxyware is distributed instead, indicating the threat actors’ flexibility in their monetization approach.
When installing Honeygain proxyware, the malware deploys “hgsdk.dll” alongside a launcher called “FastCleanPlus.exe,” which is registered as a scheduled task.
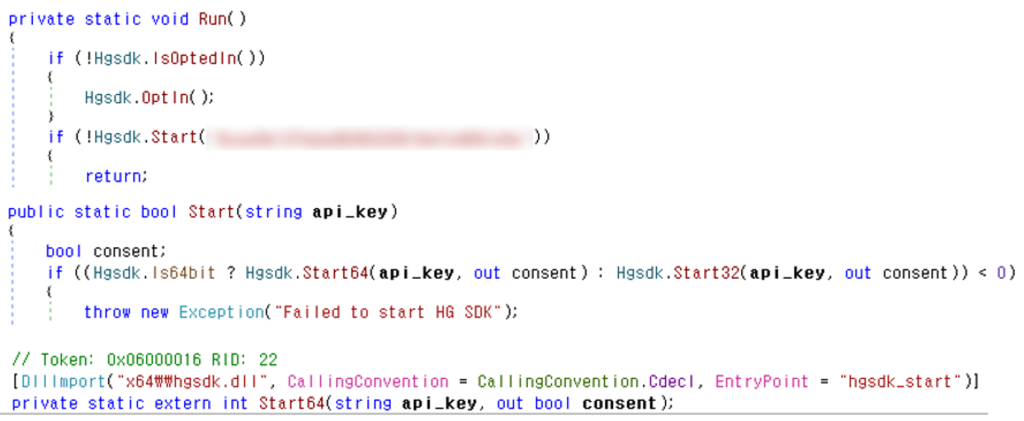
The launcher specifically calls the hgsdk_start() function with the attacker’s API credentials, enabling unauthorized bandwidth sharing.
This proxyjacking technique mirrors cryptojacking attacks but focuses on stealing network bandwidth rather than computing power for cryptocurrency mining.
Infected systems unknowingly share their internet connection with external parties, generating revenue for the attackers while potentially degrading network performance for legitimate users.
The campaign reveals concerning trends in malware distribution, notably the exploitation of legitimate platforms such as GitHub and the targeting of users seeking free software alternatives.
Security experts recommend extreme caution when downloading software from unofficial sources and emphasize the importance of using reputable antivirus solutions.
AhnLab has released multiple detection signatures for the campaign, with file detection capabilities implemented in July 2025, indicating the ongoing nature of this threat.
Users who suspect infection should immediately scan their systems and monitor network usage for unusual activity patterns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates