A critical zero-day vulnerability affecting Windows systems that allows attackers to gain maximum system privileges through a novel Kerberos-based attack technique.
The vulnerability, designated CVE-2025-33073, was patched by Microsoft on June 10, 2025, as part of their monthly Patch Tuesday security updates.
RedTeam Pentesting discovered the Reflective Kerberos Relay Attack in January 2025, which exploits a fundamental weakness in how Windows handles Kerberos authentication.
The vulnerability represents a significant evolution of relay attacks that have plagued Active Directory environments for years.
While Microsoft implemented protections against NTLM reflection attacks in 2008 with MS08-068, this new technique circumvents those safeguards by using Kerberos instead of NTLM protocols.
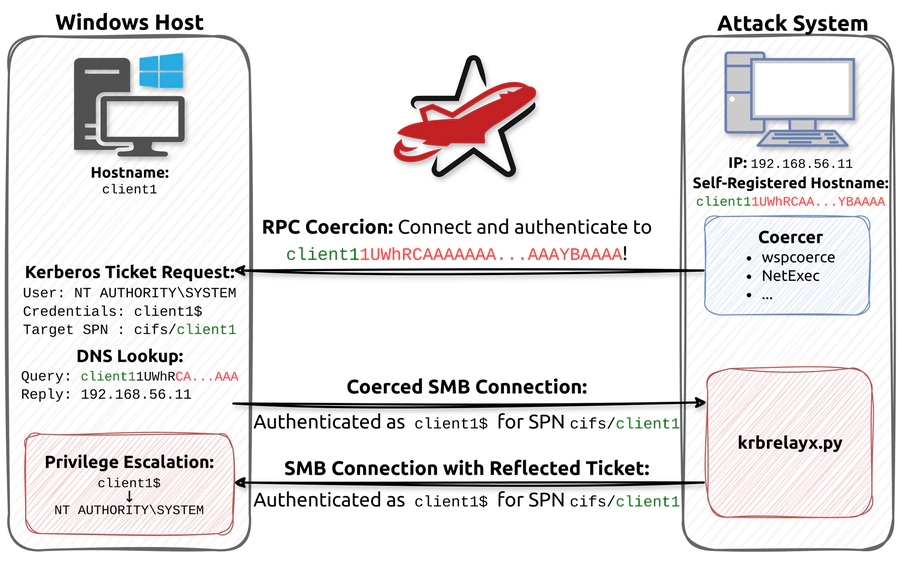
The attack enables threat actors to coerce any Windows host to authenticate back to an attacker-controlled system via SMB, then relay the computer account’s Kerberos ticket back to the original host.
This process results in the attacker obtaining NT AUTHORITY\SYSTEM privileges, the highest level of access on Windows systems, effectively providing complete control over the compromised machine.
Zero-Day Vulnerability
The Reflective Kerberos Relay Attack involves several sophisticated technical components that make it particularly dangerous.
Attackers begin with authentication coercion, a well-known technique allowing low-privileged accounts to force Windows hosts to connect and authenticate to attacker-controlled systems using their computer accounts.
The attack leverages the CredUnmarshalTargetInfo/CREDENTIAL_TARGET_INFORMATIONW technique, originally pioneered by Google Project Zero’s James Forshaw, which allows attackers to register hostnames that cause Kerberos tickets to be issued for entirely different hosts than intended.
This creates a scenario where Windows systems become confused about the authentication target, believing they are performing local loopback authentication when they are actually communicating with external attackers.
Researchers had to overcome Windows’ natural preference for NTLM over Kerberos in certain scenarios by modifying existing tools to force Kerberos authentication.
The vulnerability appears to exploit Windows’ privilege escalation mitigation mechanisms, causing the system to reuse high-privileged process tokens instead of creating fresh, appropriately restricted ones.
Windows Ecosystem Prompts
The vulnerability affects a broad range of Windows systems, including Windows 10, Windows 11, and Windows Server versions from 2019 through 2025.
RedTeam Pentesting reported no awareness of any Windows version that remains immune to this attack vector, making the scope of potential impact extensive across enterprise and consumer environments.
However, successful exploitation requires specific conditions to be met. Both authentication coercion and SMB relaying must be possible for the attack to succeed.
SMB relaying is prevented when server-side SMB signing is enforced, which is enabled by default on domain controllers and newer Windows 11 24H2 client systems.
Microsoft acknowledged the severity of the vulnerability and released patches within RedTeam Pentesting’s three-month disclosure timeline.
The company also awarded researchers a $5,000 bug bounty after initially declining the reward1. Organizations are strongly advised to apply the June 2025 Patch Tuesday updates immediately to protect against this critical vulnerability that could provide attackers with complete system compromise capabilities.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.