A recently highlighted security flaw on Lenovo machines has drawn attention to a lingering risk for organizations relying on Microsoft’s AppLocker to enforce application whitelisting.
The issue centers on a writable file, MFGSTAT.zip, found in the Windows folder of Lenovo devices, which can be exploited to bypass AppLocker’s default restrictions and execute unauthorized code.
Writable System File Enables AppLocker Bypass
Security researcher Oddvar Moe discovered that the MFGSTAT.zip file, present by default on many Lenovo systems, is writable by any authenticated user.
This is significant because AppLocker’s default rules typically allow execution of files located within the C:\Windows directory, under the assumption that standard users cannot write to this protected area.
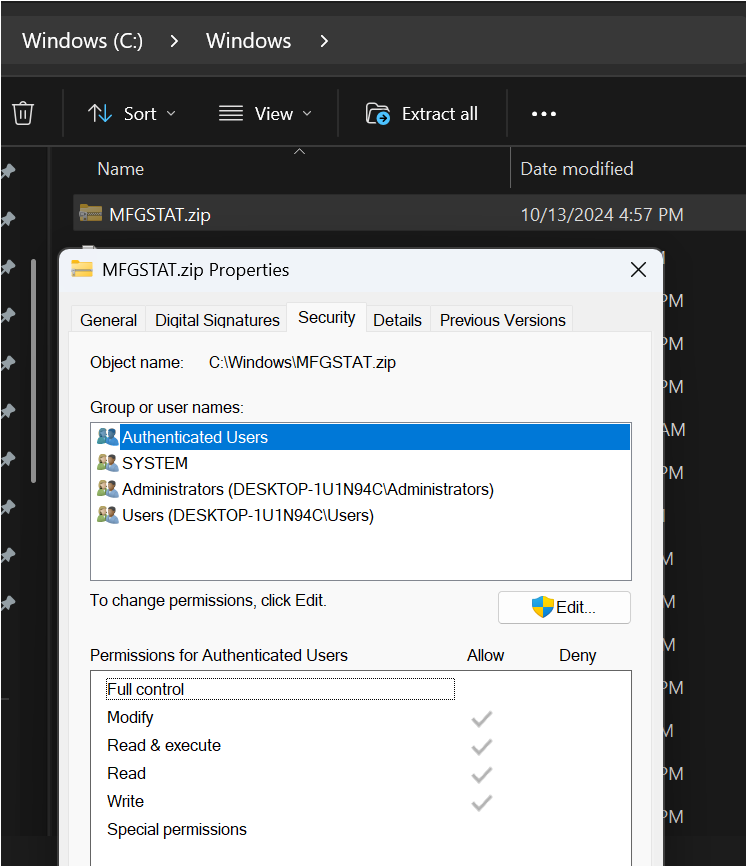
However, the presence of a writable file in this directory undermines that assumption.
Attackers can exploit this by embedding a malicious executable into an alternate data stream (ADS) of the MFGSTAT.zip file—a lesser-known NTFS feature that allows hidden data to be attached to files.
The attacker then leverages a legitimate, whitelisted Windows binary (such as AppVLP.exe) to execute the embedded code, effectively bypassing AppLocker’s controls.
This technique does not require administrative privileges and can be performed by any standard user, making it a potent vector for privilege escalation and malware execution.
Lenovo’s Response and Mitigation Guidance
Upon notification, Lenovo acknowledged the issue but opted not to release a patch.
]Instead, the company issued guidance advising users and administrators to manually delete the vulnerable MFGSTAT.zip file from affected systems.
For enterprise environments, Lenovo recommends using Group Policy Preferences, SCCM, or similar management tools to automate the removal process.
Security experts warn that this case underscores a broader problem with relying solely on AppLocker’s default rules, especially in environments where OEM images may introduce unexpected writable files or folders in trusted directories.
They recommend that organizations:
- Regularly audit file and folder permissions within trusted paths like C:\Windows.
- Customize AppLocker policies to restrict execution in any directory where users have write access.
- Remove or secure unnecessary files introduced by OEM system images.
The MFGSTAT.zip vulnerability serves as a reminder that application whitelisting solutions like AppLocker must be carefully configured and regularly reviewed to remain effective against evolving attack techniques.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates