The cyber threat landscape has witnessed a significant escalation in recent years, with a staggering increase in compromised login credentials and the proliferation of information-stealing malware.
According to the Flashpoint 2025 Global Threat Intelligence Report, threat actors compromised over 3.2 billion credentials in 2024, marking a 33% rise from the previous year.
This surge in compromised credentials has been largely driven by the meteoric rise of infostealers, which have become a primary vector for ransomware and high-impact data breaches.
The Rise of Infostealers and Ransomware
Infostealers have emerged as a dominant threat vector, responsible for sourcing 75% of the stolen credentials in 2024.
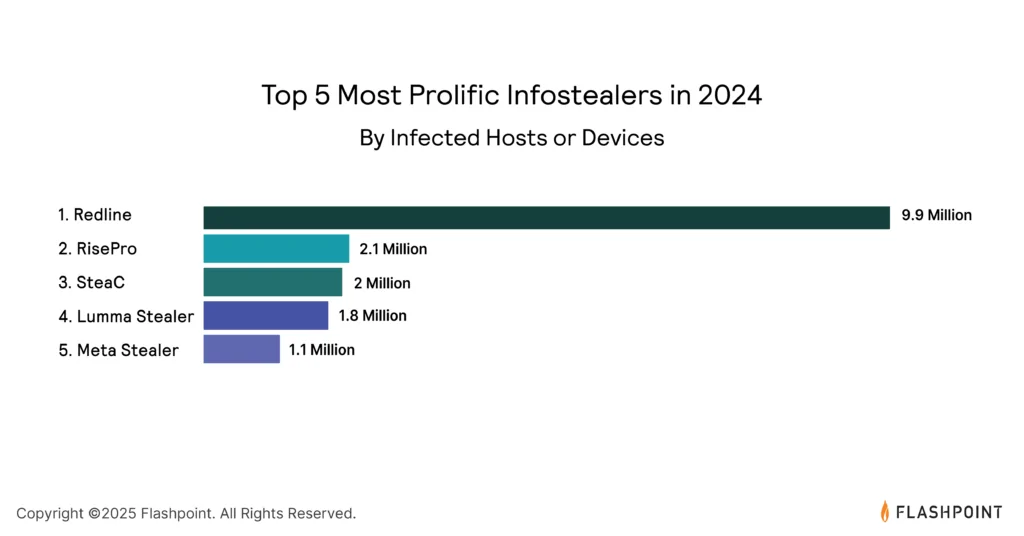
These malware tools have infected over 23 million devices worldwide, leveraging their simplicity, effectiveness, and low overhead costs to fuel ransomware attacks and data breaches.
The ease with which infostealers can be obtained and deployed has made them a preferred choice among threat actors seeking to compromise sensitive information.
As a result, organizations must remain vigilant and proactive in monitoring for these threats to prevent significant security breaches.
The increase in compromised credentials has also contributed to a rise in ransomware attacks, which saw a 10% increase across all sectors in 2024.
This follows a substantial 84% increase from the previous year, highlighting the evolving nature of cyber threats.
The most prolific ransomware-as-a-service (RaaS) groups, including Lockbit, Ransomhub, Akira, Play, and Qilin, were responsible for over 47% of the reported attacks in 2024.
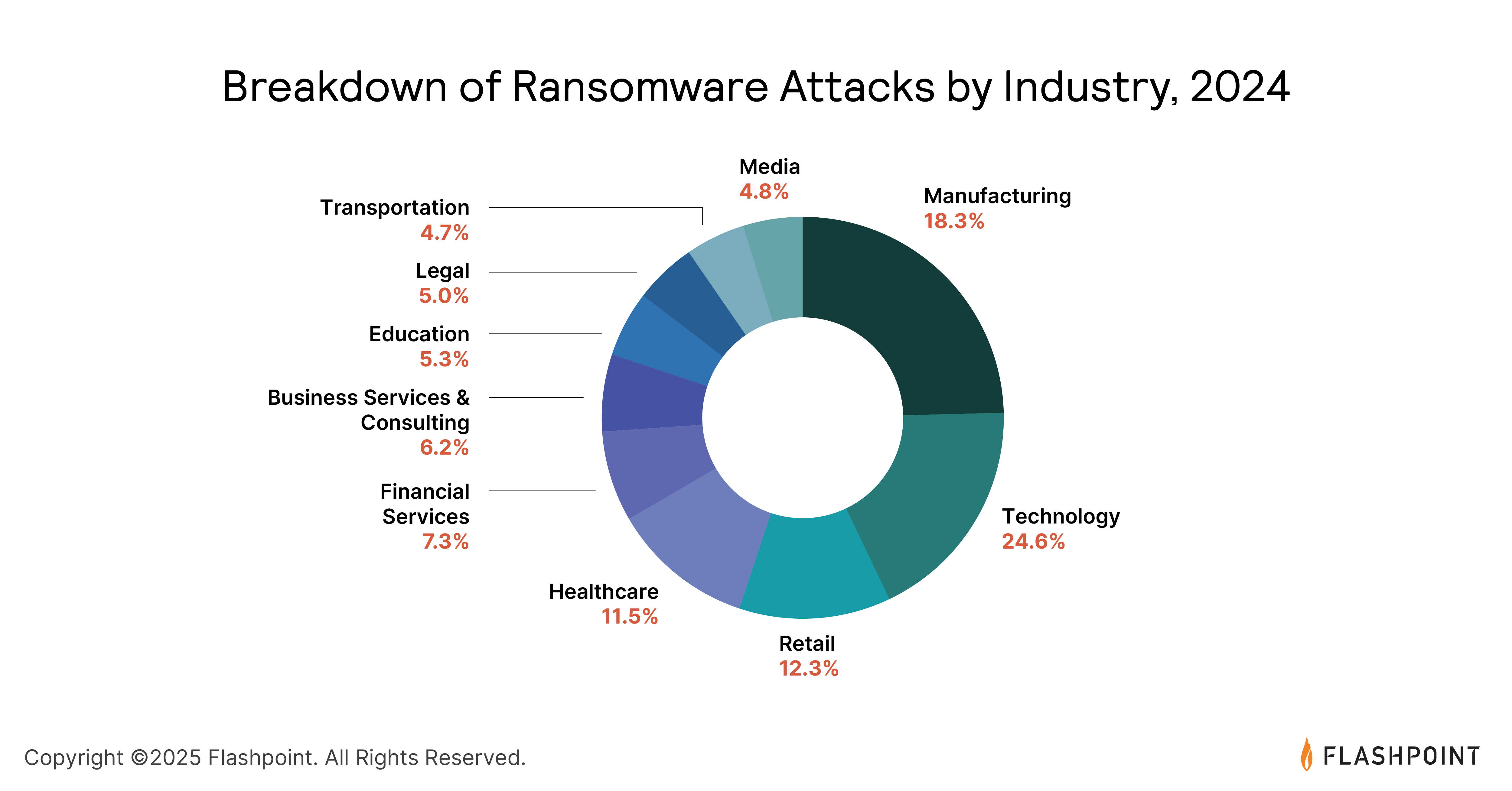
Additionally, data breaches experienced a year-over-year increase of approximately 6%, underscoring the need for robust security measures and incident response plans.
Vulnerabilities and Exploits
The threat landscape is further complicated by the growth in vulnerabilities.
In 2024, Flashpoint aggregated 37,302 vulnerabilities, with over 39% having publicly available exploit code.
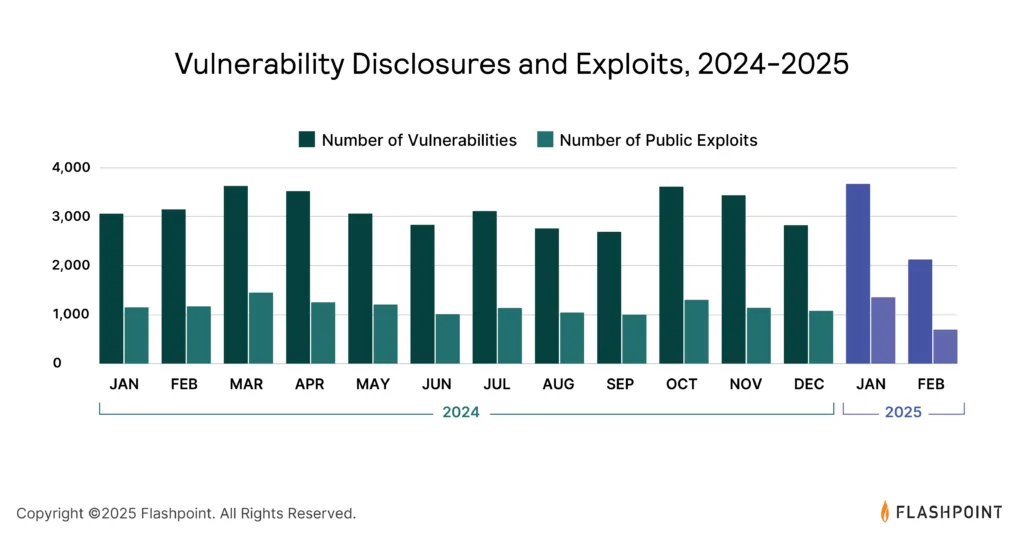
This presents a significant challenge for security teams, as threat actors can exploit these vulnerabilities to gain unauthorized access to systems.
The increasing attack surface and the availability of exploit code emphasize the importance of prioritizing vulnerability management based on exploitability rather than severity alone.
In response to these evolving threats, organizations must adopt a proactive and holistic security approach.
This includes leveraging actionable intelligence to strengthen security postures and staying informed about the tactics, techniques, and procedures (TTPs) of threat actors.
By doing so, organizations can better navigate the complexities of the cyber threat landscape and safeguard their critical assets against emerging risks.