Cybersecurity researchers have identified a massive exploitation campaign targeting Fortinet FortiWeb Web Application Firewall (WAF) instances, with threat actors leveraging a critical SQL injection vulnerability to deploy webshells across dozens of systems globally.
The attacks, which began shortly after public proof-of-concept (PoC) exploits became available, highlight the rapid weaponization of newly disclosed security flaws by malicious actors.
Technical Analysis of CVE-2025-25257 Vulnerability
According to the post from The Shadowserver Foundation, the vulnerability at the center of this campaign, designated CVE-2025-25257, represents a severe pre-authenticated SQL injection flaw affecting the FortiWeb graphical user interface.
With a Common Vulnerability Scoring System (CVSS) severity rating of 9.6 out of 10, this critical vulnerability allows unauthenticated attackers to execute arbitrary code remotely through specially crafted HTTP requests.
The flaw specifically resides within the FortiWeb Fabric Connector component, which facilitates integration between the WAF and other Fortinet security products.
Security researcher Kentaro Kawane of GMO Cybersecurity discovered the vulnerability, which enables attackers to bypass authentication mechanisms entirely.
The SQL injection vector allows malicious actors to manipulate database queries, potentially extracting sensitive information or executing unauthorized commands on the underlying system.
This type of attack is particularly dangerous because it requires no prior authentication, making any internet-exposed FortiWeb instance vulnerable to exploitation.
Active Exploitation Campaign and Global Impact
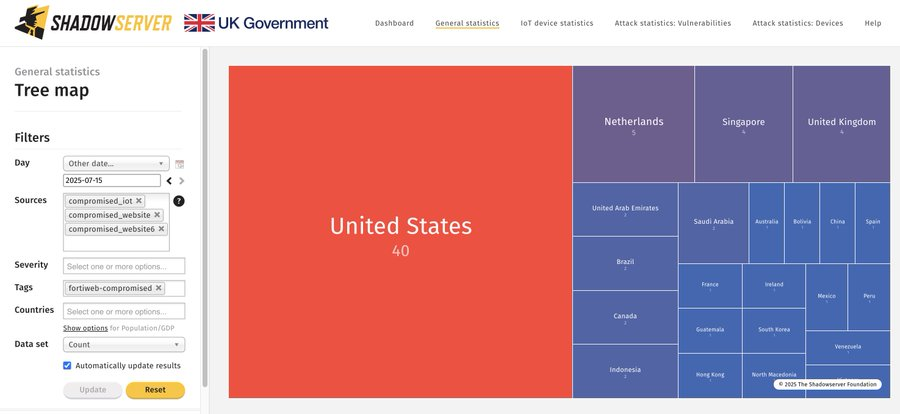
The Shadowserver Foundation reported tracking 77 compromised FortiWeb instances as of July 16, 2025, representing a slight decrease from 85 systems identified the previous day.
The organization confirmed that active exploitation began on July 11, coinciding with the public release of exploit code by cybersecurity firm WatchTower and other researchers.
This timing demonstrates the concerning speed at which threat actors can operationalize publicly available exploits.
The attack methodology involves deploying webshells—malicious scripts that provide persistent backdoor access to compromised systems.
These webshells enable attackers to maintain control over infected devices, execute commands, and potentially pivot to other network resources.
The United States accounts for the highest number of compromised devices at 40, followed by the Netherlands, Singapore, and the United Kingdom.
Additionally, 223 FortiWeb management interfaces remain exposed to the internet, creating potential targets for further compromise.
Mitigation Strategies and Vendor Response
Fortinet disclosed the vulnerability on July 8, 2025, and promptly released security patches to address the flaw.
The company has urged customers to upgrade to secure versions, including FortiWeb 7.6.4, 7.4.8, 7.2.11, or 7.0.11 and later releases.
For organizations unable to immediately deploy patches, Fortinet recommends disabling the HTTP/HTTPS administrative interface as a temporary workaround to block the primary attack vector.
The incident highlights the crucial importance of rapid patch deployment in enterprise environments, especially for internet-facing security appliances that serve as primary defensive barriers against cyber threats.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates