In a significant cybersecurity discovery, security researcher Henry N. Caga uncovered a cross-site scripting (XSS) vulnerability within a Google sub-domain, potentially allowing hackers to hijack user sessions, conduct phishing attacks, distribute malware, and steal data.
This vulnerability, found in the aihub.cloud.google.com domain, underscores the critical importance of robust cybersecurity measures even within the infrastructures of tech giants like Google.
The Discovery Process
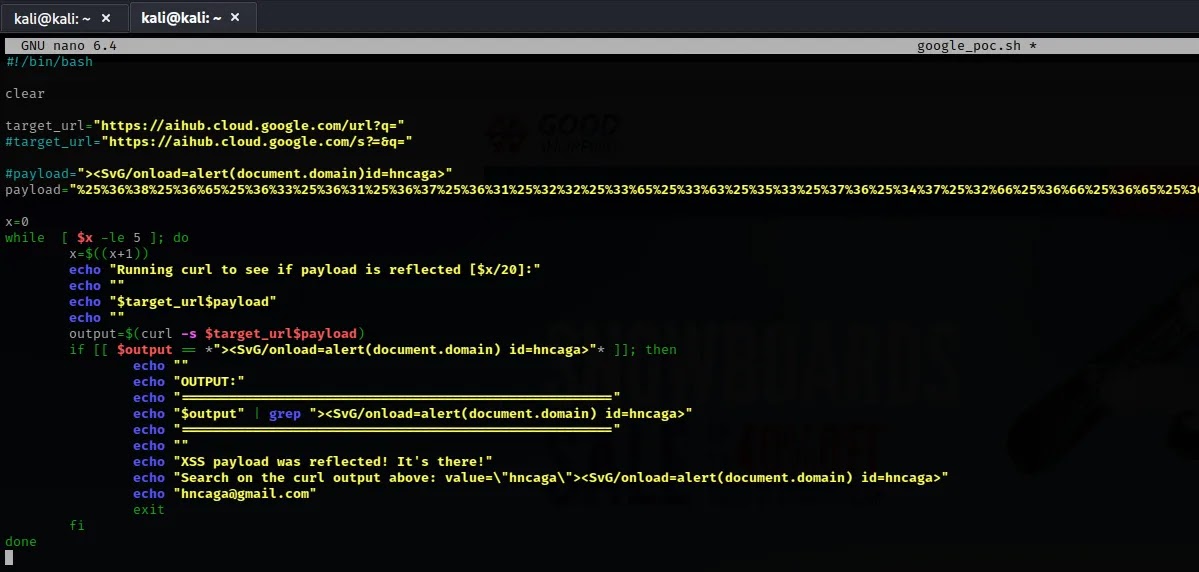
Caga’s investigation began with a suspicion towards the URL https://aihub.cloud.google.com/url?q=https://cidadesmineradoras.com.br, which he believed might be vulnerable.
His initial attempts to exploit the ‘q’ parameter with various payloads were unsuccessful until he employed a double-encoded payload that exposed the XSS vulnerability.
This method involved a meticulous documentation process using Burpsuite, a tool for testing web security.
Despite the initial challenge of Google’s security team being unable to replicate the XSS pop-up, Caga’s persistence paid off.
He developed a bash script to repeatedly request the vulnerable URL, which confirmed the inconsistency of the vulnerability’s trigger.
This script was a crucial part of his investigation, leading to the successful identification of the vulnerability.

Reporting and Resolution of XSS Vulnerability
Following the principles of responsible disclosure, Caga promptly reported his findings to Google’s security team.
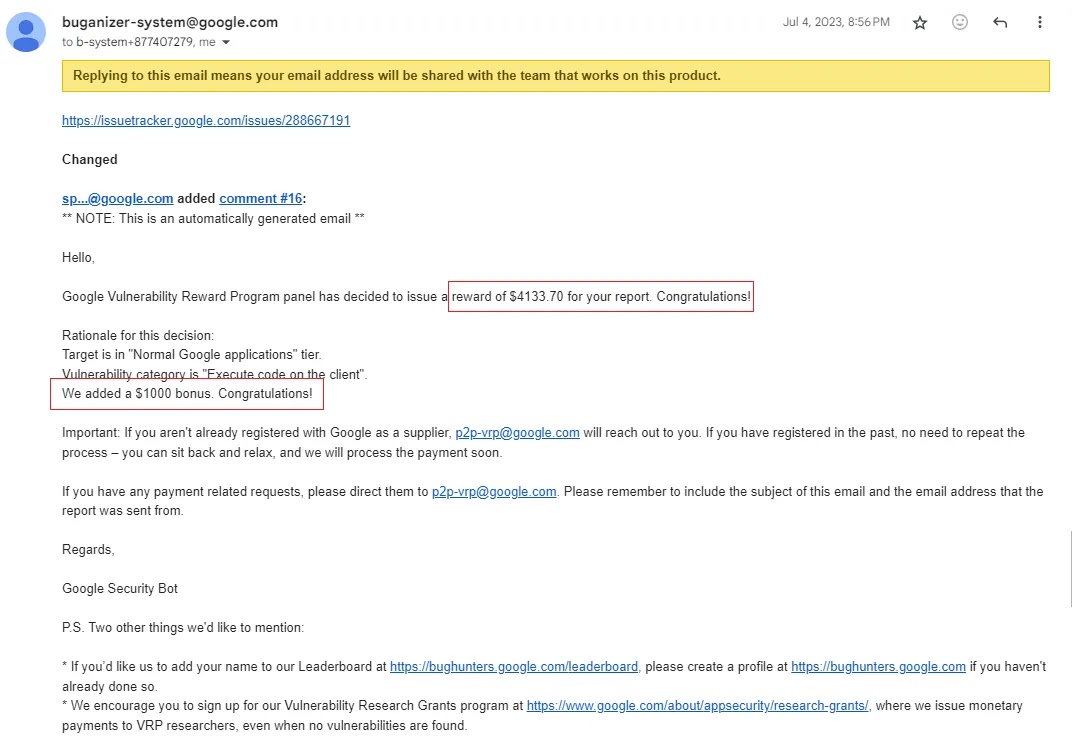
The team quickly acknowledged the severity of the issue, upgrading its priority and expressing gratitude for the discovery with a reward of $4,133.70 to Caga, which included a $1,000 bonus for his comprehensive report and proof of concept scripts.
The XSS vulnerability had far-reaching implications, including the potential for session hijacking, phishing attacks, malware distribution, and data theft.
Such vulnerabilities pose significant risks to user security and can damage the reputation of companies like Google, known for their secure services.
The Impact and Resolution
The discovery of this vulnerability serves as a reminder of the ongoing need for vigilant cybersecurity measures.
It highlights the importance of collaboration between users, developers, and security professionals in maintaining a secure online environment.
Google’s prompt and professional response to the vulnerability report, including the resolution of the issue, was commended by Caga.
On March 15, 2024, he received an update from Google’s security team that the vulnerability had been resolved.
However, the site began returning a 502 error, which was clarified by Google as a result of the deprecation of aihub and its migration to Vertex AI since January 2024.
This incident not only showcases the critical role of security researchers in identifying and mitigating vulnerabilities but also emphasizes the importance of companies like Google in taking swift action to protect their users.
The collaborative effort between Caga and Google’s security team ensured the continued protection of users worldwide, reinforcing the significance of robust cybersecurity policies and practices in today’s digital age.
Also Read: Russian Cyber Criminals use Hacked Routers
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.