HijackLoader, a modular malware loader first identified in 2023, continues to evolve with sophisticated techniques aimed at bypassing malware analysis and sandbox detection.
Recent updates to its modules, analyzed by Zscaler ThreatLabz, reveal advanced anti-virtual machine (VM) checks and call stack spoofing methods, underscoring its growing threat to cybersecurity defenses.
Call Stack Spoofing: A New Layer of Obfuscation
One of the most notable additions to HijackLoader is its implementation of call stack spoofing.
This tactic manipulates the return addresses in the call stack to obscure the origin of malicious function calls, such as API or system calls.
By using fabricated stack frames, HijackLoader conceals its activity from endpoint detection mechanisms.

The malware leverages the base pointer register (EBP) to traverse and patch stack frames with legitimate-looking return addresses from system DLLs like ntdll.dll or kernelbase.dll.
This technique is further combined with the “Heaven’s Gate” method, enabling seamless transitions between 32-bit and 64-bit code execution for direct syscalls.
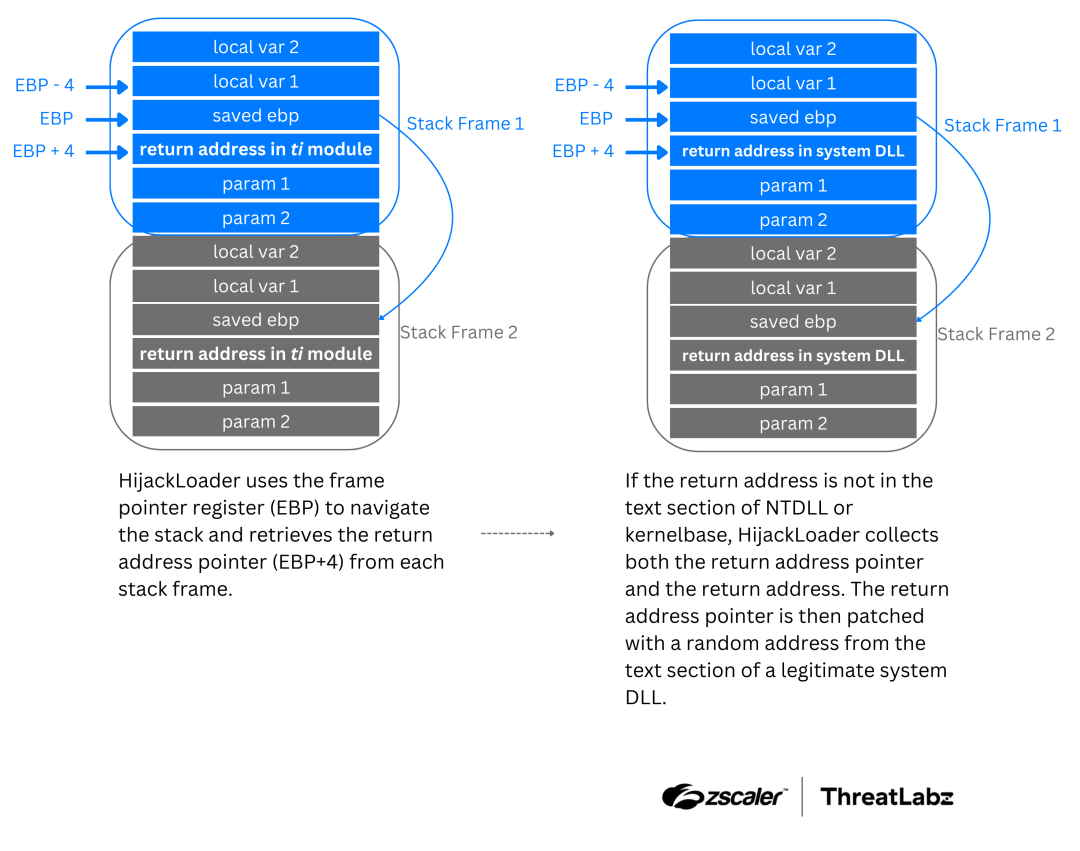
Modules such as modCreateProcess, modUAC, and modTask also employ call stack spoofing but without utilizing direct syscalls or Heaven’s Gate.
These modules instead invoke Windows API functions directly while maintaining obfuscated call stacks.
Sophisticated Anti-VM Detection
The newly introduced ANTIVM module is designed to detect virtualized environments and sandbox systems commonly used for malware analysis.
It employs multiple checks, including:
- Timing analysis of the CPUID instruction to identify anomalies in execution time.
- Detection of hypervisor presence by inspecting specific CPU flags.
- Validation of system hardware configurations, such as physical memory size and processor count.
- Behavioral checks, including username verification and execution path analysis.
These measures allow HijackLoader to terminate execution if it detects conditions indicative of a virtualized or sandboxed environment, thereby thwarting analysis efforts.
Another significant update is the modTask module, which establishes persistence by creating scheduled tasks.
According to the Report, this module uses configurations stored in the PERSDATA structure to execute tasks either at regular intervals or upon user login.
Before initiating these tasks, HijackLoader employs XOR-based obfuscation on its modules to further complicate detection.
The continuous evolution of HijackLoader highlights its adaptability and focus on evasion.
By integrating advanced anti-detection techniques such as call stack spoofing and anti-VM checks, it poses a significant challenge for traditional malware detection tools.
As these capabilities expand, organizations must adopt more robust threat detection mechanisms that leverage behavioral analysis and machine learning to counteract such sophisticated threats.
Find this Story Interesting! Follow us on LinkedIn, and X to Get More Instant Updates