In the ever-evolving landscape of cybersecurity, a new threat has emerged that challenges the integrity of digital authentication processes. Known as the Silver SAML attack, this technique enables attackers to forge SAML responses, specifically targeting Entra ID systems.
That Report aims to shed light on this sophisticated attack mechanism, its implications for cloud security, and the measures that can be taken to safeguard against it.
The Mechanism Behind Silver SAML Attacks
Silver SAML represents a significant evolution in cyber attack techniques, building upon the foundation laid by its predecessor, Golden SAML. While Golden SAML attacks focus on forging authentication to cloud applications by exploiting SAML (Security Assertion Markup Language) tokens, Silver SAML introduces a more nuanced approach.
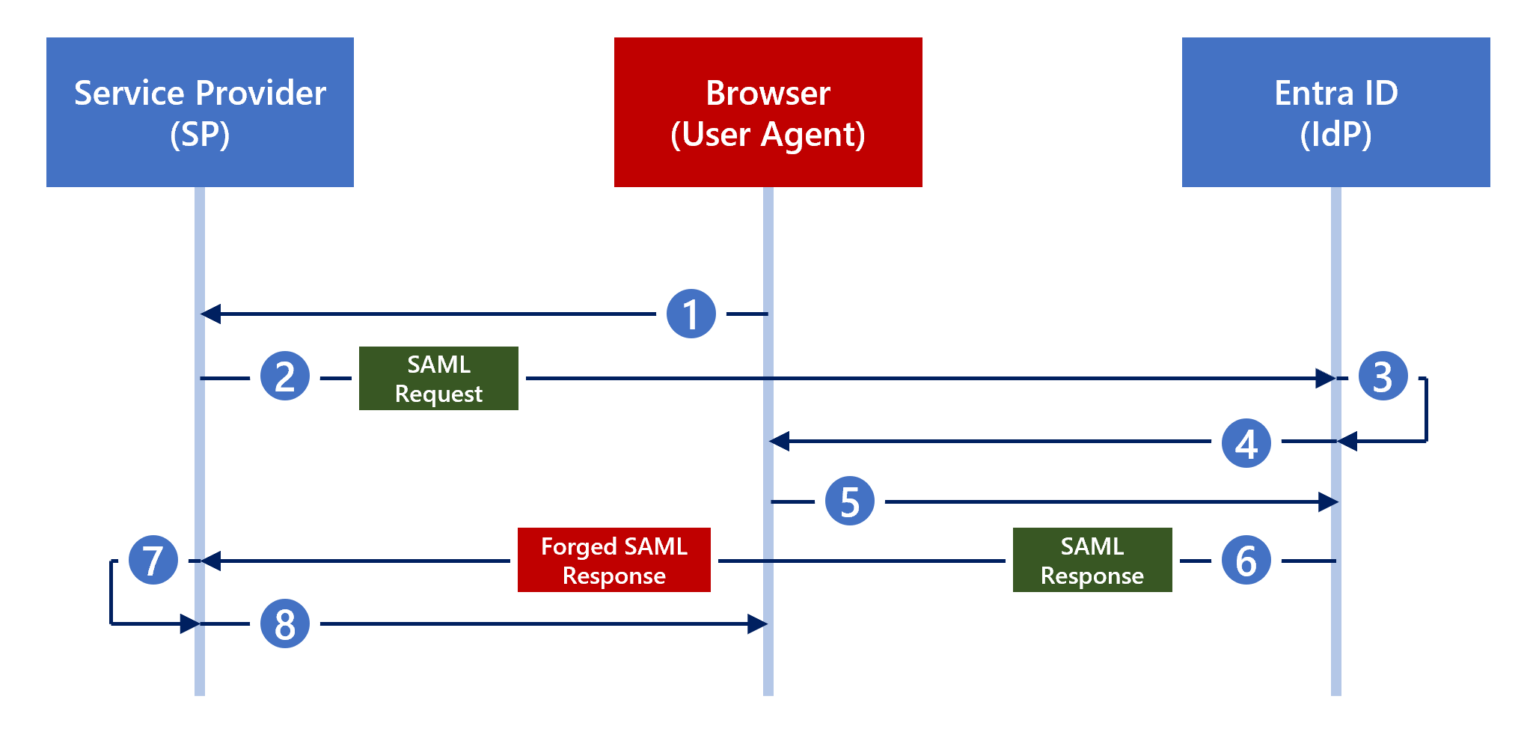
Silver SAML attacks exploit vulnerabilities in the Security Assertion Markup Language (SAML) authentication process. SAML is widely used for single sign-on (SSO) services, allowing users to access multiple applications with one set of login credentials.
By forging SAML responses, attackers can impersonate legitimate users, gaining unauthorized access to a wide range of services and sensitive information. This method involves manipulating SAML responses to gain unauthorized access to cloud resources, posing a serious threat to organizations’ cloud infrastructure.
Golden SAML in the Cloud
Golden SAML attacks have been known for their ability to compromise cloud-based applications and services by forging SAML authentication objects. This technique allows attackers to impersonate any user and gain access to any application that supports SAML authentication, such as Azure, AWS, and vSphere, with any privileges they desire. The shift to cloud infrastructure has made traditional Active Directory (AD) systems part of a larger federation, increasing the attack surface for potential exploits.
The Threat to Entra ID Systems
Entra ID, formerly known as Azure AD, is a critical component of many organizations’ identity and access management systems. The Silver SAML attack specifically targets these systems, allowing attackers to bypass authentication mechanisms. This vulnerability poses a significant risk, as it can lead to data breaches, unauthorized access to critical infrastructure, and potential financial losses.
The emergence of Silver SAML as a sophisticated cyber attack technique highlights the need for continuous vigilance and proactive security measures. Organizations must stay informed about the latest threats and implement comprehensive security strategies to protect their cloud environments.
Regular security audits, advanced threat detection, and strict access controls are essential to mitigate the risk of Silver SAML attacks. By taking these steps, organizations can safeguard their valuable assets and maintain the trust of their customers and stakeholders.
The Evolution of SAML Attacks
The concept of forging SAML responses is not entirely new. Previously known as the Golden SAML attack, this technique has been documented and utilized in various cyber incidents, including the notable SolarWinds campaign.
The Silver SAML attack represents an evolution of this technique, with a specific focus on compromising Entra ID systems. The scope of information at risk underscores the importance of robust security measures to protect against such attacks.
Silver SAML attacks can expose a wide range of sensitive information, including user identities, authentication credentials, and access privileges. By manipulating SAML responses, attackers can potentially access any application within an organization’s cloud environment, leading to data breaches and unauthorized access to critical resources.
Mitigation and Defense Strategies
To protect against Silver SAML attacks, organizations must adopt a multi-layered security approach. This includes:
- Regularly Updating and Patching Systems: Ensuring that all systems are up-to-date with the latest security patches can help mitigate vulnerabilities that attackers might exploit.
- Monitoring and Auditing: Implementing comprehensive monitoring and auditing of authentication processes can help detect unusual patterns or unauthorized access attempts.
- Enhancing Security Configurations: Reviewing and tightening security configurations, especially those related to SAML and Entra ID systems, can reduce the attack surface.
- Employee Awareness and Training: Educating employees about the latest cybersecurity threats and best practices can help prevent phishing and other tactics used to gain initial access to systems.
To defend against Silver SAML attacks, organizations must adopt a multi-layered security approach. This includes monitoring for unusual SAML response patterns, implementing strict access control and authentication measures, and employing advanced threat detection systems.
Additionally, organizations should ensure that their SAML implementations are secure and regularly audited for vulnerabilities. Preventing replay attacks by keeping a cache for processed assertions during the time an assertion is not expired is also crucial.
The Importance of Vigilance
The emergence of the Silver SAML attack underscores the importance of continuous vigilance in the cybersecurity domain. As attackers evolve their techniques, organizations must stay informed and proactive in implementing robust security measures to protect their digital assets and sensitive information.
The Silver SAML attack represents a significant threat to organizations relying on SAML for authentication. By understanding the nature of this attack and implementing effective mitigation strategies, organizations can safeguard against unauthorized access and maintain the integrity of their digital identities.
Silver SAML represents a significant threat to cloud security, but with the right precautions and response strategies, organizations can effectively defend against these sophisticated attacks.