The notorious North Korean-linked Lazarus Group has significantly enhanced its malware delivery capabilities through sophisticated new techniques in its ongoing Contagious Interview campaign.
Recent analysis reveals the cybercriminal organization has developed three distinct payload delivery mechanisms for its primary malware families—BeaverTail, InvisibleFerret, and OtterCookie—demonstrating a continuous evolution in their attack methodologies while maintaining their core operational tactics.
Technical Innovation in Malware Delivery
The Lazarus Group has implemented three primary delivery mechanisms that showcase their adaptive approach to evading detection systems.
The first technique utilizes an eval function-based delivery system, where malicious code performs POST requests to external domains such as fashdefi[.]store using port 6168.
This method captures the server response and executes the content dynamically, effectively bypassing traditional detection mechanisms that rely on static code analysis.
The second approach demonstrates sophisticated evasion tactics through URL fragmentation and false token implementation.
Attackers strategically split complete URLs into multiple code segments and leverage legitimate hosting services like Vercel.App as command and control servers.
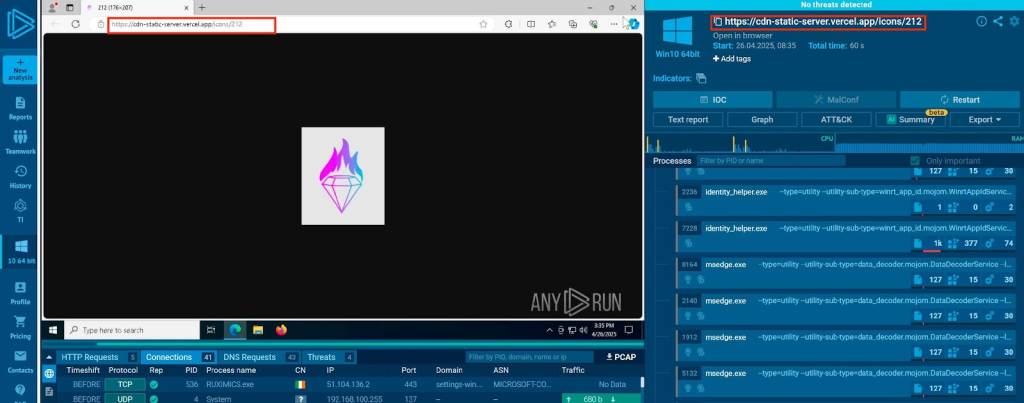
This technique includes the use of bearer tokens, specifically a “logo” token, to authenticate and receive encoded payloads while serving legitimate favicon files to unauthorized requests.
Evolution of Attack Methodologies
The third delivery mechanism represents the most advanced iteration, combining elements from previous techniques while introducing novel error-handling approaches.
Instead of relying solely on eval functions, this method utilizes try/catch blocks programmed to return 500 API errors, subsequently delivering malicious code through custom errorHandler functions.
This approach demonstrates the group’s commitment to continuous innovation while preserving its fundamental attack logic.
Implications for Cybersecurity Defense
The rapid development of these sophisticated delivery techniques raises significant concerns about the potential use of artificial intelligence in malware development.
The presence of syntax errors and insufficient code review suggests automated code generation, challenging traditional defense mechanisms that depend on pattern matching and direct code detection.
The Lazarus Group’s enhancement of its malware delivery capabilities through OtterCookie and related payloads represents a concerning escalation in its technical sophistication.
Security researchers anticipate further innovations in the coming months, necessitating more robust detection rules and dynamic analysis capabilities to counter these evolving threats.
Organizations must adapt their cybersecurity strategies to address these advanced persistent threat actors who continue to refine their attack methodologies while maintaining their core operational objectives.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates