Security researchers have identified a sophisticated phishing technique that exploits HTML conditional statements to display different content depending on whether recipients view emails in Microsoft Outlook or other email clients.
This method allows cybercriminals to hide malicious links from corporate security systems while still directing victims to credential-stealing websites when accessed through non-Outlook platforms.
A recent phishing campaign targeting Czech bank customers initially appeared to contain a critical error that raised suspicions among security analysts.
The email masqueraded as a legitimate communication from a major Czech financial institution, requesting account holders to update their personal information through a provided link.
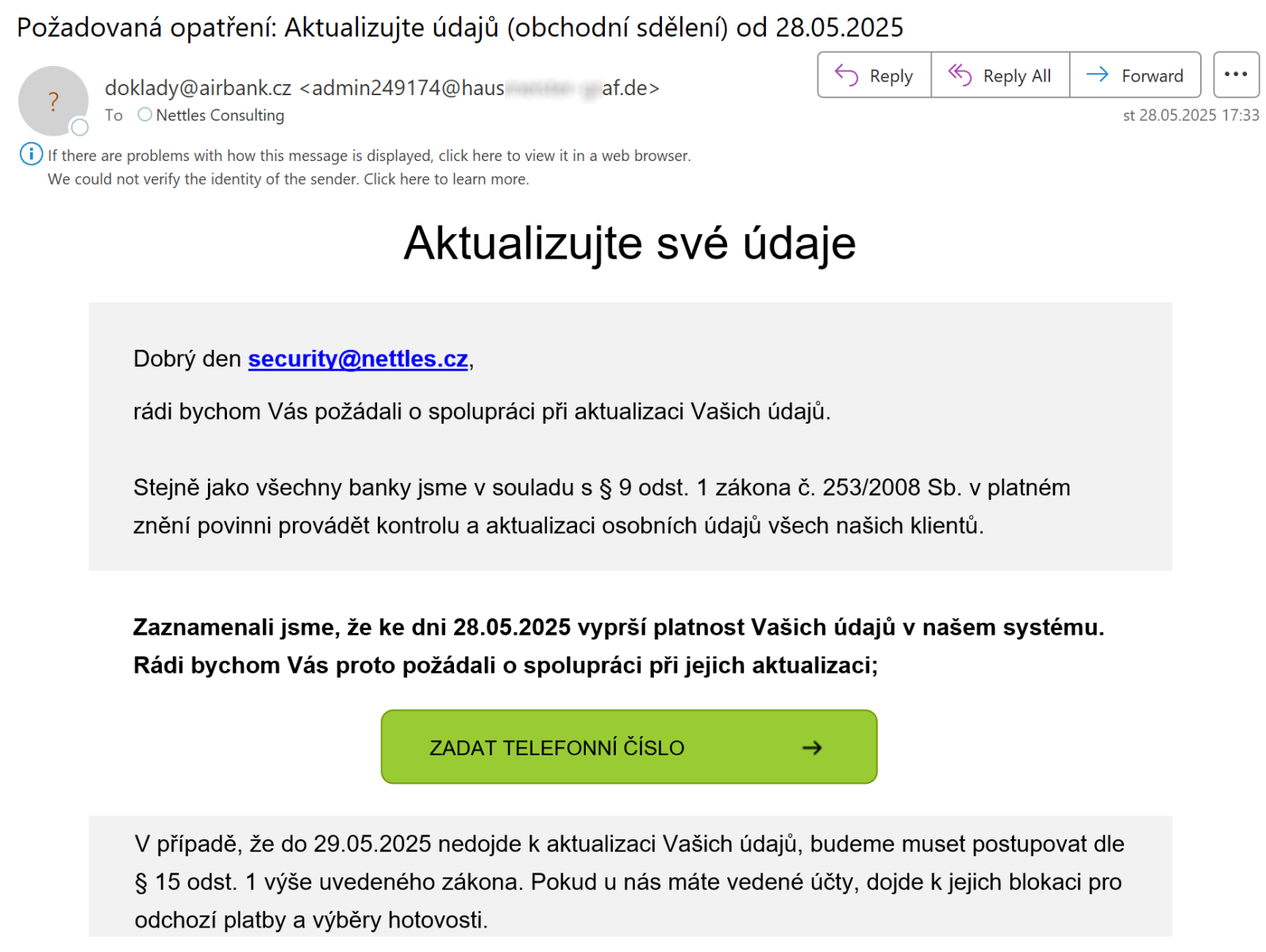
However, when investigators examined the message, they discovered an unexpected anomaly: hovering over the call-to-action button revealed that the embedded link actually pointed to the bank’s legitimate domain.
Initial assessment suggested the threat actors had made a fundamental mistake, possibly sending an incomplete phishing template before replacing the legitimate URLs with malicious ones.
Such errors, while uncommon, have been documented in previous cybercriminal operations. However, deeper analysis of the email’s HTML source code revealed a far more sophisticated attack methodology that demonstrated advanced technical knowledge and strategic planning.
Outlook Users
The phishing campaign leverages HTML conditional comments, specifically the <!--[if mso]> and <!--[if !mso]> statements, which were originally designed to ensure consistent email rendering across different platforms.
These Microsoft-specific conditional statements allow developers to specify content that should display exclusively in Outlook (mso) or in all other email clients and browsers (!mso).
The malicious implementation creates two parallel content streams within a single email message.
When opened in Microsoft Outlook, recipients see a hyperlink directing them to the legitimate banking website, effectively creating a benign appearance that would pass most automated security scans.
Conversely, when the same email is accessed through alternative email clients such as Gmail, Apple Mail, or web browsers, the conditional logic activates the malicious pathway, redirecting users to credential-harvesting websites designed to steal banking credentials and personal information.
The technical structure follows this pattern: legitimate links are encapsulated within Outlook-specific conditional tags, while malicious URLs are embedded within the inverse conditional statements that target non-Outlook environments.
This dual-layer approach ensures that corporate security systems scanning emails in Outlook-based environments encounter only legitimate links during automated analysis.
Security Implications
According to Report, this technique presents particular challenges for enterprise security teams, as many corporate environments rely heavily on Microsoft Outlook for email communications.
The attack strategy demonstrates sophisticated understanding of corporate security architectures, where organizations typically implement multiple layers of protection including DNS filtering, web traffic analysis, and automated link scanning systems.
By presenting legitimate links to these security mechanisms, the phishing campaign can potentially bypass automated detection systems that rely on URL reputation analysis.
The technique also exploits user behavior patterns, as employees receiving banking communications at work email addresses might already be suspicious of such messages, making them less likely to interact with obviously malicious content.
While this conditional comment abuse technique has been documented since at least 2019, its practical implementation remains relatively uncommon in active phishing campaigns.
However, as cybercriminals continue developing increasingly sophisticated evasion techniques, security teams must adapt their detection methodologies to identify such conditional-logic-based attacks and educate users about these emerging threats.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Update