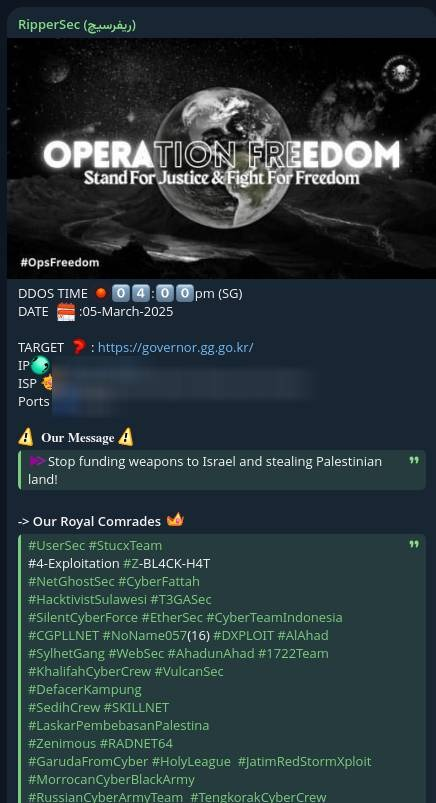
Pro-Palestinian hacktivist group RipperSec has claimed responsibility for a distributed denial-of-service (DDoS) attack targeting the official website of South Korea’s Gyeonggi Province Governor Kim Dong-yeon, according to an alert posted by cybersecurity intelligence platform FalconFeeds.
The attack, which temporarily disrupted access to the site, underscores growing concerns about state-affiliated cyber infrastructure vulnerabilities to politically motivated threat actors.
Telemetry data indicates the website, now fully restored, experienced intermittent outages consistent with application-layer DDoS patterns.
Technical Profile of RipperSec’s Attack Methodology
RipperSec, a Malaysia-based collective active since June 2023, utilized its signature MegaMedusa tool to execute the attack—a Python-based framework designed to overwhelm web servers through HTTP/S request floods.
The tool employs 10 randomization techniques, including dynamic user-agent spoofing, referrer forgery, and randomized URL path generation, to evade signature-based detection systems.
Forensic analysis suggests attackers leveraged MegaMedusa’s proxy chaining capabilities, routing traffic through compromised IoT devices and residential proxies to mask the attack’s origin.
The group’s Telegram channel, boasting over 2,000 subscribers, has previously documented 196 DDoS incidents since January 2024, primarily targeting Israeli government portals and institutions perceived as supporting Zionist policies.
This marks their first confirmed operation against South Korean infrastructure, signaling potential geopolitical alignment with anti-Western narratives.
Target Analysis: Gyeonggi Province’s Strategic Significance
As South Korea’s most populous province (26 million residents) and economic hub contributing 21% of national GDP, Gyeonggi’s digital infrastructure represents high-value critical infrastructure.
Governor Kim, a former Deputy Prime Minister elected in 2022, has spearheaded international partnerships with U.S. states like Utah and California, including clean energy initiatives and semiconductor supply chain collaborations.
While no explicit pro-Israeli stance exists in these agreements, RipperSec’s targeting may reflect broader opposition to South Korea’s Western-aligned foreign policy.
Mitigation and Response
The Gyeonggi Provincial Government’s IT division implemented rate-limiting rules and upstream filtering through Akamai Prolexic, restoring full functionality within 47 minutes.
No data exfiltration or lateral movement was detected, confirming the attack’s confinement to service disruption.
South Korea’s National Police Agency has activated its Cyber Investigation Bureau to trace the attack’s botnet infrastructure, with preliminary findings pointing to hijacked satellite receivers—a tactic previously observed in December 2024 DDoS campaigns against financial institutions.
Implications for Regional Cybersecurity
This incident highlights two emerging threats:
- Weaponized IoT Proliferation: Over 240,000 compromised satellite receivers in South Korea alone provide ample attack surface for DDoS botnets, exacerbated by lax firmware security standards.
- Hacktivist-Government Convergence: RipperSec’s collaboration with 14 other groups, including Tengkorak Cyber Crew and Morrocan Cyber Black Army, suggests increasing coordination among anti-establishment collectives.
Governor Kim’s office has announced a KRW 12 billion ($9 million) investment into AI-driven threat detection systems, prioritizing real-time anomaly identification in network traffic patterns.
As hacktivist groups continue refining asymmetric attack tools like MegaMedusa, the need for cross-border cybersecurity cooperation—particularly in semiconductor-dependent economies like Gyeonggi—has reached critical urgency.
Also Read: