A concerning development has emerged in the cybersecurity landscape, as a threat actor has reportedly advertised Remote Code Execution (RCE) access to an unidentified company in the United Kingdom.
The claim was made public through a post on a dark web forum, sparking fears of potential exploitation and data breaches.
What is RCE and Why is it Dangerous?
According to the post from Dark Web Informer, Remote Code Execution (RCE) is a critical vulnerability that allows attackers to execute arbitrary commands on a target system.
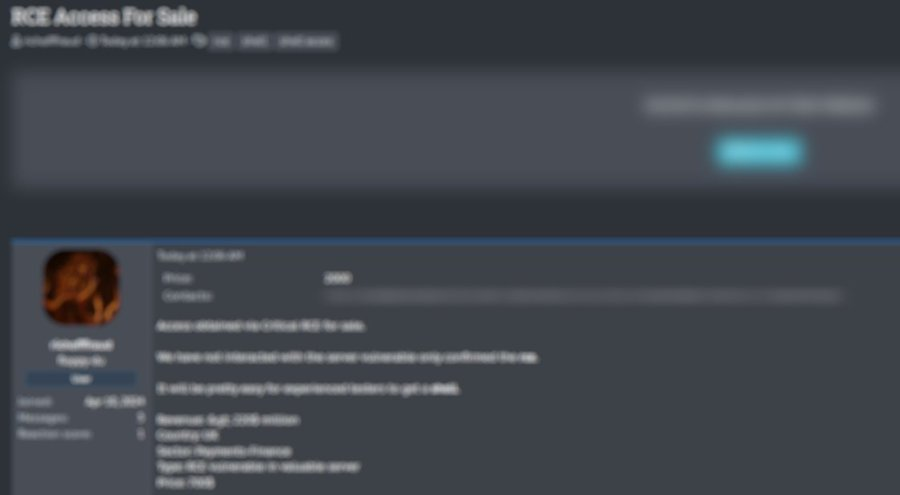
This type of access can grant cybercriminals full control over an organization’s network, enabling them to steal sensitive data, deploy ransomware, or disrupt operations entirely.
The sale of such access on underground marketplaces represents a significant threat, as it lowers the barrier for other malicious actors to exploit the vulnerability.
The unidentified UK company targeted in this case has not been named publicly, but the situation underscores the growing risks businesses face from cybercrime.
If the claim by the threat actor is legitimate, the consequences could be severe, ranging from financial losses to reputational damage.
Details of the Dark Web Listing
The advertisement for the RCE access was highlighted by a dark web monitoring account on social media.
According to the post, the threat actor is actively seeking buyers for this access, though details about the company or how the vulnerability was discovered remain undisclosed.
Such listings are not uncommon in underground forums, where cybercriminals trade exploits and stolen data.
Typically, these transactions involve cryptocurrency payments to maintain anonymity.
The price for RCE access can vary widely depending on factors such as the size of the company and the potential value of its data.
While it’s unclear how much this particular access is being sold for, similar listings in the past have fetched thousands of dollars.
Implications and Preventative Measures
This incident serves as a stark reminder for organizations to prioritize cybersecurity.
Businesses must conduct regular vulnerability assessments and implement robust security measures to mitigate risks.
Patching known vulnerabilities quickly and training employees on cybersecurity best practices can significantly reduce exposure to such threats.
Authorities and cybersecurity experts are likely monitoring this situation closely. If verified, efforts may be made to identify and neutralize the threat actor before any damage occurs.
However, with cybercrime evolving rapidly, organizations must remain vigilant against increasingly sophisticated attacks targeting their systems and data.
Also Read: