In an effort to track the infrastructure activity of threat actors, cybersecurity researchers emphasize the critical importance of analyzing digital artifacts such as TLS certificates and server configurations.
These traces provide valuable insights into past and ongoing operations, allowing defenders to both identify malicious activity and anticipate future attacks.
The Insikt Group of Recorded Future previously examined GhostWolf a network infrastructure cluster attributed to the suspected Chinese state-sponsored threat actor RedGolf, also known by aliases like APT41, BARIUM, and Earth Baku.
Their March 2023 report identified connections to KEYPLUG malware, which has recently been linked to attacks targeting Italian organizations in 2024.
Building on this foundation, researchers have used historical TLS certificate data to uncover evidence of a continued or imitated infrastructure tied to the suspected actor.
Advanced Techniques in Infrastructure Analysis
The investigation used the Indicators of Compromise (IoC) shared in the Insikt Group’s report, particularly focusing on 39 IP addresses.
A recurring pattern emerged involving a wolfSSL certificate a lightweight, open-source SSL/TLS library designed for secure communication in embedded systems.
However, subtle changes in certificate fields, such as the “Organizational Unit” (OU) value being altered from “Consulting_1024” to “Support_1024,” provided a critical fingerprint for tracking the actor’s activity.
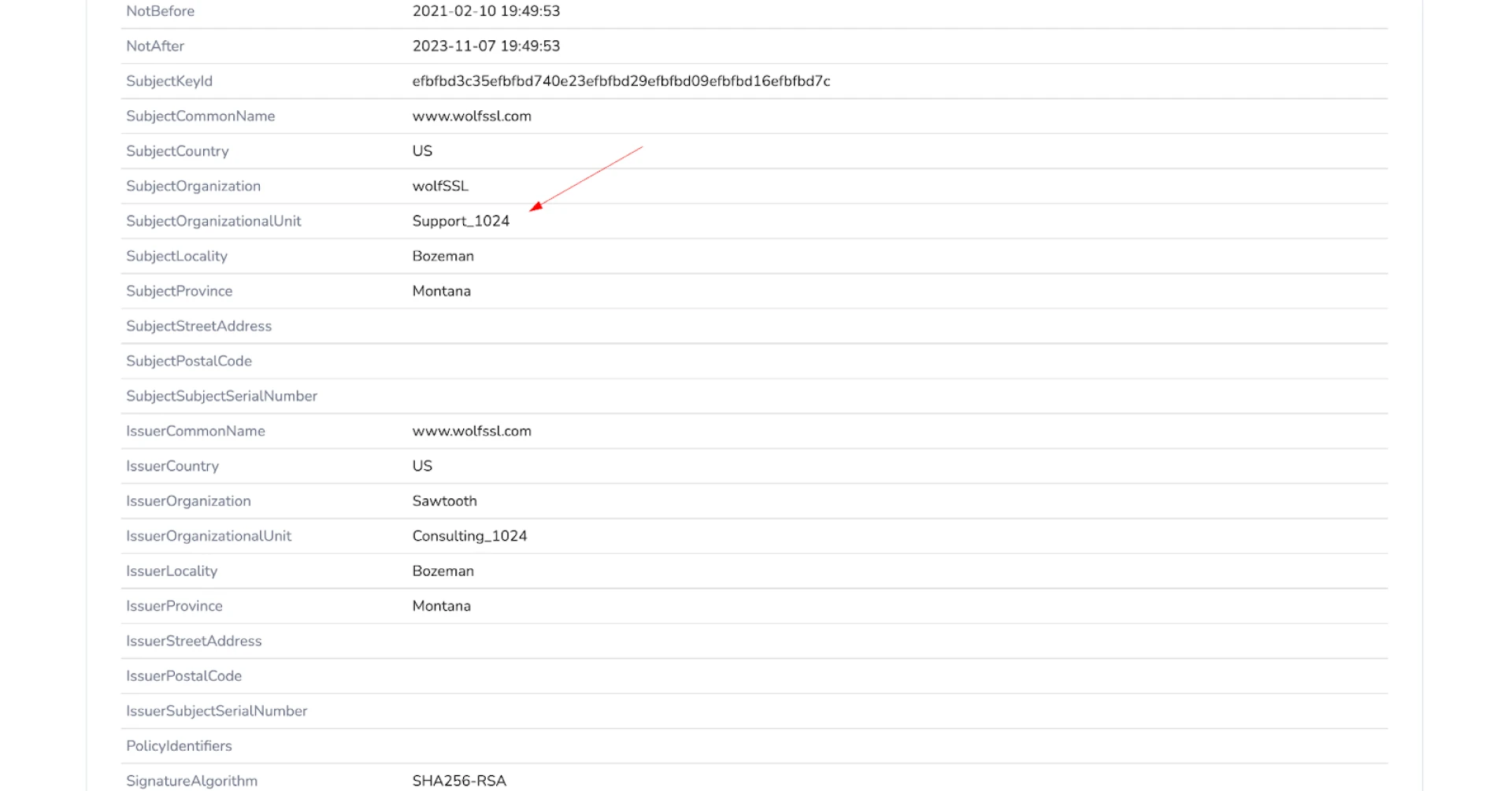
These nuanced modifications, which adjusted the SHA-256 hash and JA4X fingerprint of the certificates, allowed researchers to differentiate the malicious infrastructure from legitimate configurations.
JA4X, an advanced TLS fingerprinting method extending the widely used JA3 method, played a pivotal role in narrowing the scope of investigation.
It enhanced detection capabilities by incorporating additional metadata, enabling researchers to identify 41 servers sharing the fingerprint c9d784bbb12e_c9d784bbb12e_83900cc62ac7.
Ongoing Operation Insights
Most of the servers operated on port 443 (commonly used for HTTPS), displaying network responses indicative of Command and Control (C2) communication.
Further, the servers’ geolocation and hosting providers spanning countries like Singapore, India, the United States, Hong Kong, and Canada align with previous infrastructure reports.
One notable observation connected an active server hosted at 67.43.234[.]150 to earlier reports of KEYPLUG malware activity targeting Italian organizations.
The proximity of IP addresses and overlapping SSL certificates reinforce potential links to the GhostWolf cluster, though conclusive attribution remains challenging.

The discovery of additional certificates tied to the JA4X fingerprint has raised questions about whether these represent a GhostWolf variant or a broader infrastructure subset.
For instance, a certificate on the server 114.55.6[.]216, hosted by Aliyun Computing Co. in China, resembled the wolfSSL example certificate but exhibited overlapping issue dates and configurations observed in prior findings.
This investigation by Hunt highlights the persistent reuse of modified TLS certificates and server configurations by sophisticated threat actors.
While the GhostWolf infrastructure’s ties to RedGolf or APT41 are not definitively proven, the observed activity underscores the need for meticulous infrastructure monitoring and proactive defenses.