Cybersecurity researchers at CYFIRMA have identified a sophisticated Windows-based keylogger dubbed “TinkyWinkey,” first observed in late June 2024, that employs advanced system programming techniques to maintain persistent surveillance of infected machines.
The malware demonstrates exceptional stealth capabilities by operating as both a Windows service and executable, capturing extensive system intelligence while evading detection through legitimate process injection.
Dual-Component Architecture Ensures Persistent Operation
TinkyWinkey operates through a two-tier system comprising the “Tinky Service” and “Winkey Keylogger” components. The service component manages lifecycle operations, including installation, startup, and deletion, while launching the keylogger within active user sessions.
This architecture enables the malware to survive system reboots through the automatic startup of services.
The keylogger module captures comprehensive system intelligence by invoking multiple reconnaissance functions, including get_windows_info(), get_cpu_info(), get_ip_address(), and get_ram_info().
Particularly notable is its use of the undocumented RtlGetVersion API from ntdll.dll to bypass application compatibility shims and obtain accurate OS version information.
The malware combines __cpuid intrinsics with GetSystemInfo() calls to enumerate detailed processor specifications and logical core counts.
Network profiling occurs through Winsock initialization, where the malware retrieves hostname information via gethostname() and resolves IPv4 addresses using. getaddrinfo().
Memory capacity enumeration leverages GlobalMemoryStatusEx() to query total physical RAM specifications and create detailed system fingerprints stored in UTF-8-encoded log files.
Advanced Keystroke Interception and Process Injection
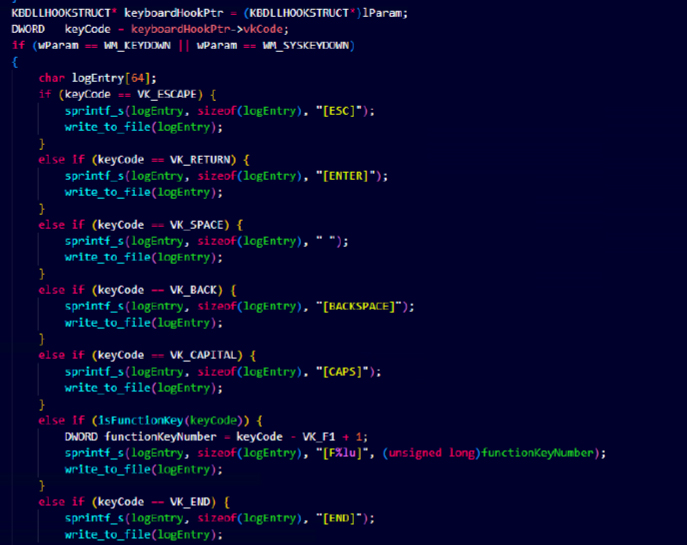
The keylogger implements low-level keyboard hooks (WH_KEYBOARD_LL) to capture all system-wide input, including alphanumeric characters, function keys, navigation controls, and media keys.
The malware accurately handles Unicode characters across multiple languages by monitoring keyboard layout changes (HKL) and employing ToUnicode() with WideCharToMultiByte() conversion for proper character encoding.
Foreground window monitoring through WinEventHook on EVENT_SYSTEM_FOREGROUND enables correlation between keystrokes and specific applications, significantly enhancing the value of captured credentials for banking portals, email clients, and browsers.
Sophisticated Evasion Through DLL Injection
TinkyWinkey’s loader component performs reliable DLL injection into trusted processes, specifically targeting explorer.exe.
The injection process involves remote memory allocation via VirtualAllocEx(), writing the DLL path into allocated memory, and creating remote threads using LoadLibraryW().
This technique ensures stealthy execution within legitimate process contexts while maintaining full access rights for memory allocation and thread creation.
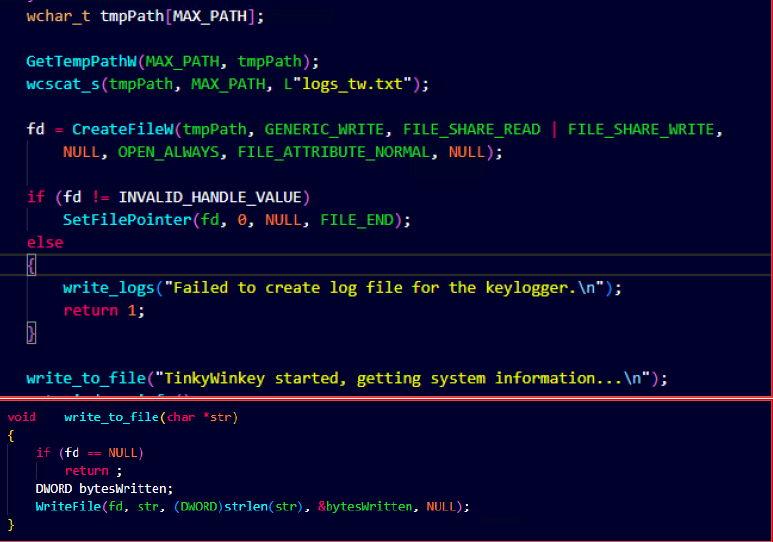
The malware creates persistent log files named logs_tw.txt in system temporary directories, serving as centralized repositories for both system reconnaissance data and captured user activity.
Organizations should monitor for unusual service installations, unexpected DLL injections into system processes, and persistent logging patterns as potential indicators of compromise.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates