A significant breakthrough in bypassing Windows activation has been achieved with the introduction of TSforge, a powerful exploit developed by the MASSGRAVE research group.
This tool is capable of activating every edition of Windows since Windows 7, along with all Windows add-ons and Office versions since Office 2013.
TSforge represents a major advancement in exploiting the Software Protection Platform (SPP), the core system behind Windows activation.
Background and Development
The journey to creating TSforge began with the discovery of the “CID trick” in 2023.
This method involved manipulating Confirmation IDs (CIDs) used in phone activation to bypass validation checks.
Researchers found that by patching the CID validation code in sppobjs.dll, they could use a fake CID for activation, and this activation persisted even after restarting the service.
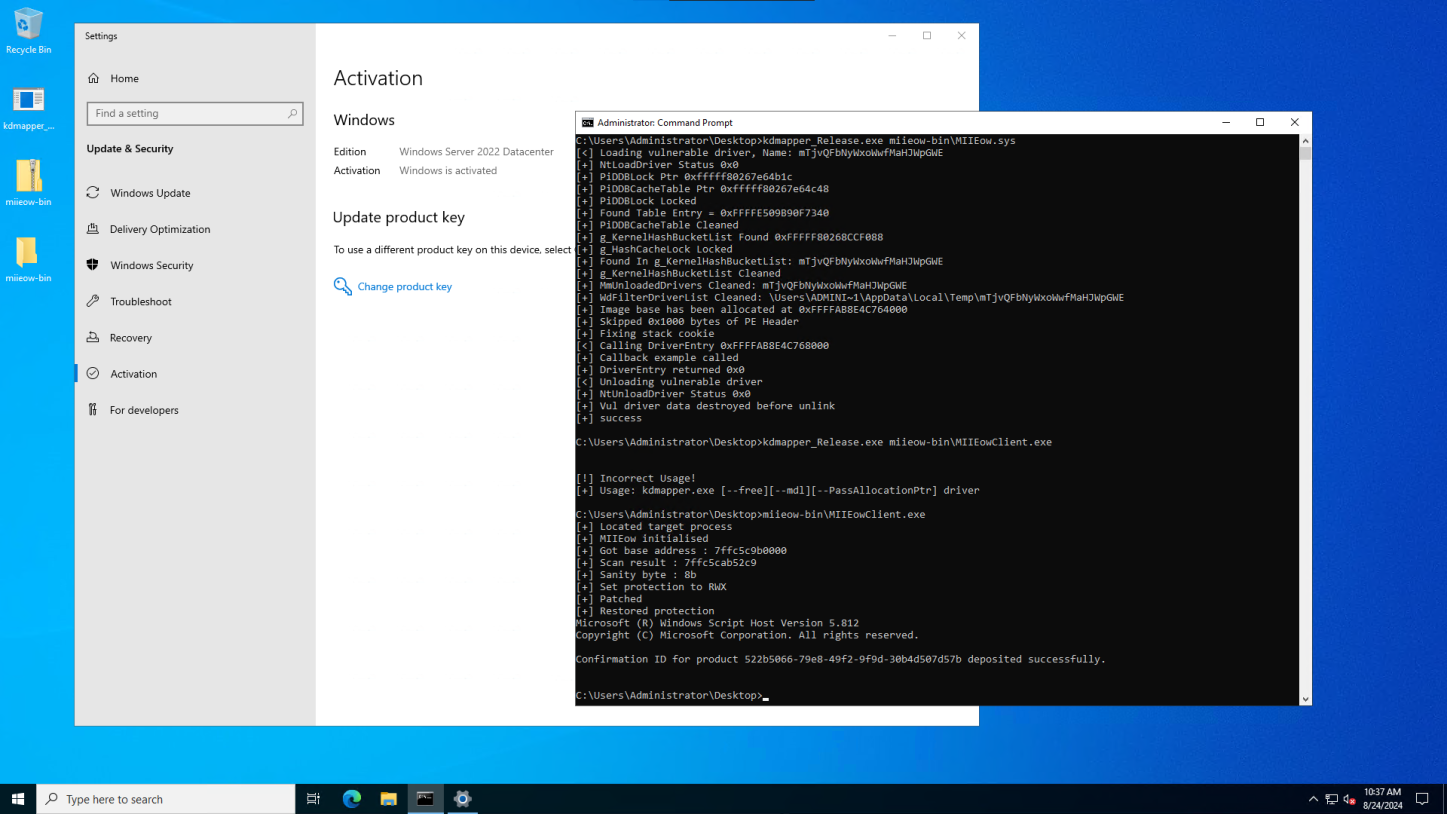
This suggested that once activation data is written, it is not validated again, offering a potential path for universal activation.
To develop TSforge, researchers had to understand where and how activation data is stored.
They identified key locations such as data.dat and tokens.dat files, along with registry keys under HKEY_LOCAL_MACHINE\SYSTEM\WPA.
According to MASSGRAVE, these components form the “trusted store,” which holds critical activation data in encrypted form.
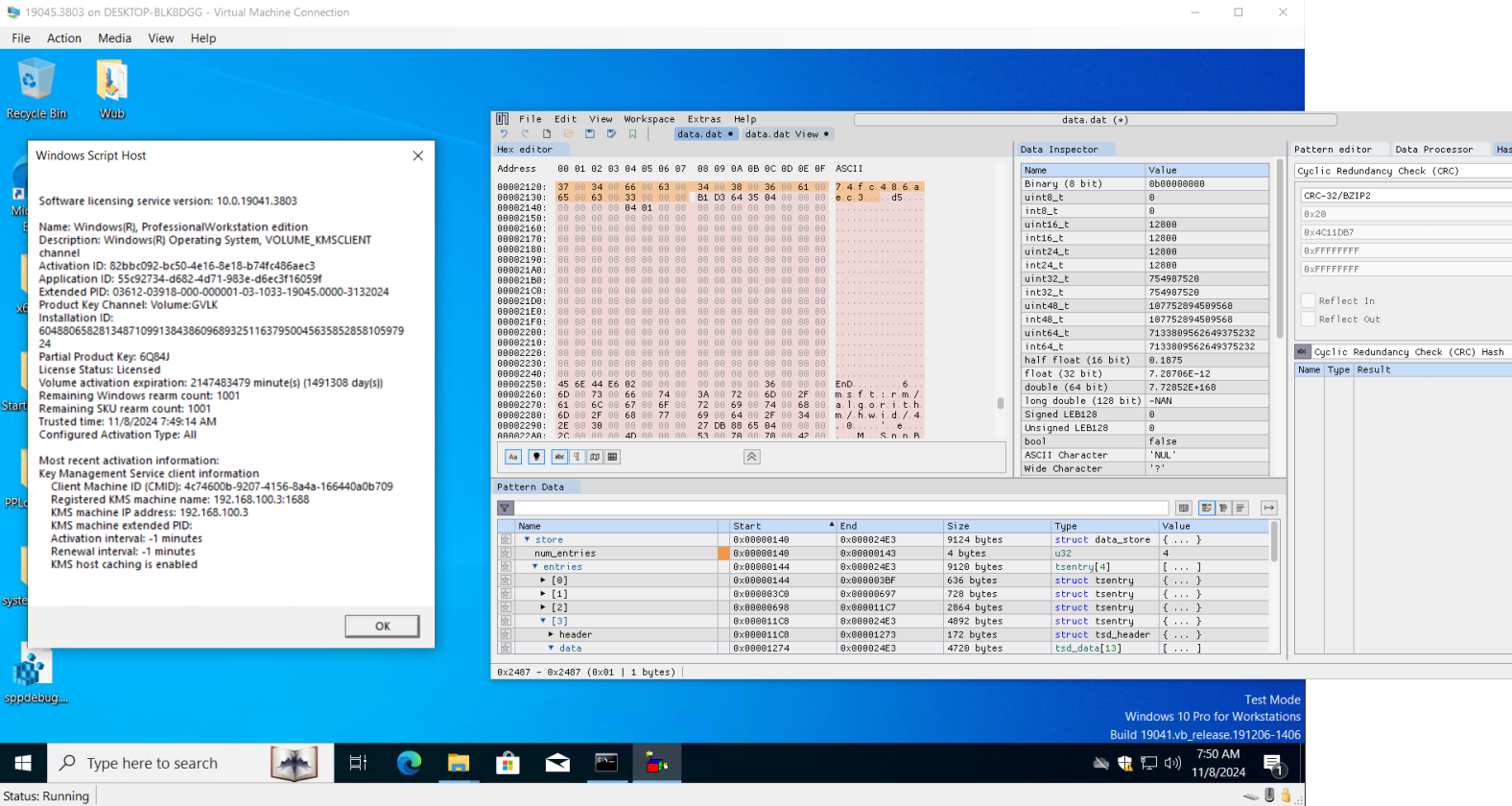
By analyzing leaked Windows beta builds, particularly those related to Windows 8 development, researchers gained insights into the spsys.sys driver, which handles encryption and decryption of the trusted store on older Windows versions.
Technical Breakthroughs
A crucial breakthrough came from reverse-engineering the spsys.sys driver using leaked beta builds.
This allowed researchers to understand the encryption mechanisms and derive the private RSA keys used by SPP.
By simulating the bytecode system used in the RSA decryption routine, they were able to track and dump the inputs and outputs of modular multiplications, ultimately deriving the production and test private keys for SPP.
With these keys, TSforge can decrypt and modify the physical store, enabling the activation of any Windows edition without needing debuggers or kernel exploits.
Additionally, researchers developed a method to replicate product key metadata, bypassing the need for actual keys.
They also created a universal Hardware ID (HWID) that applies to all hardware configurations, allowing activation to be transferred between machines.
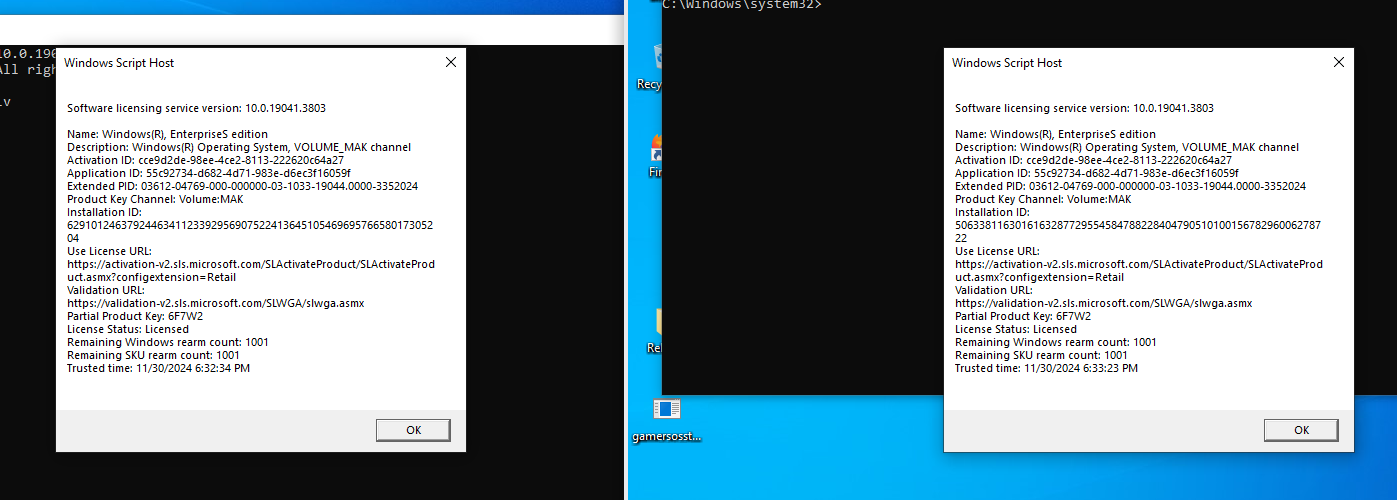
TSforge marks a significant milestone in bypassing Windows activation, showcasing the complexity and depth of research required to exploit SPP.
Despite its success, the researchers acknowledge that SPP remains a robust DRM system with unexploited components, such as signed XML licenses.
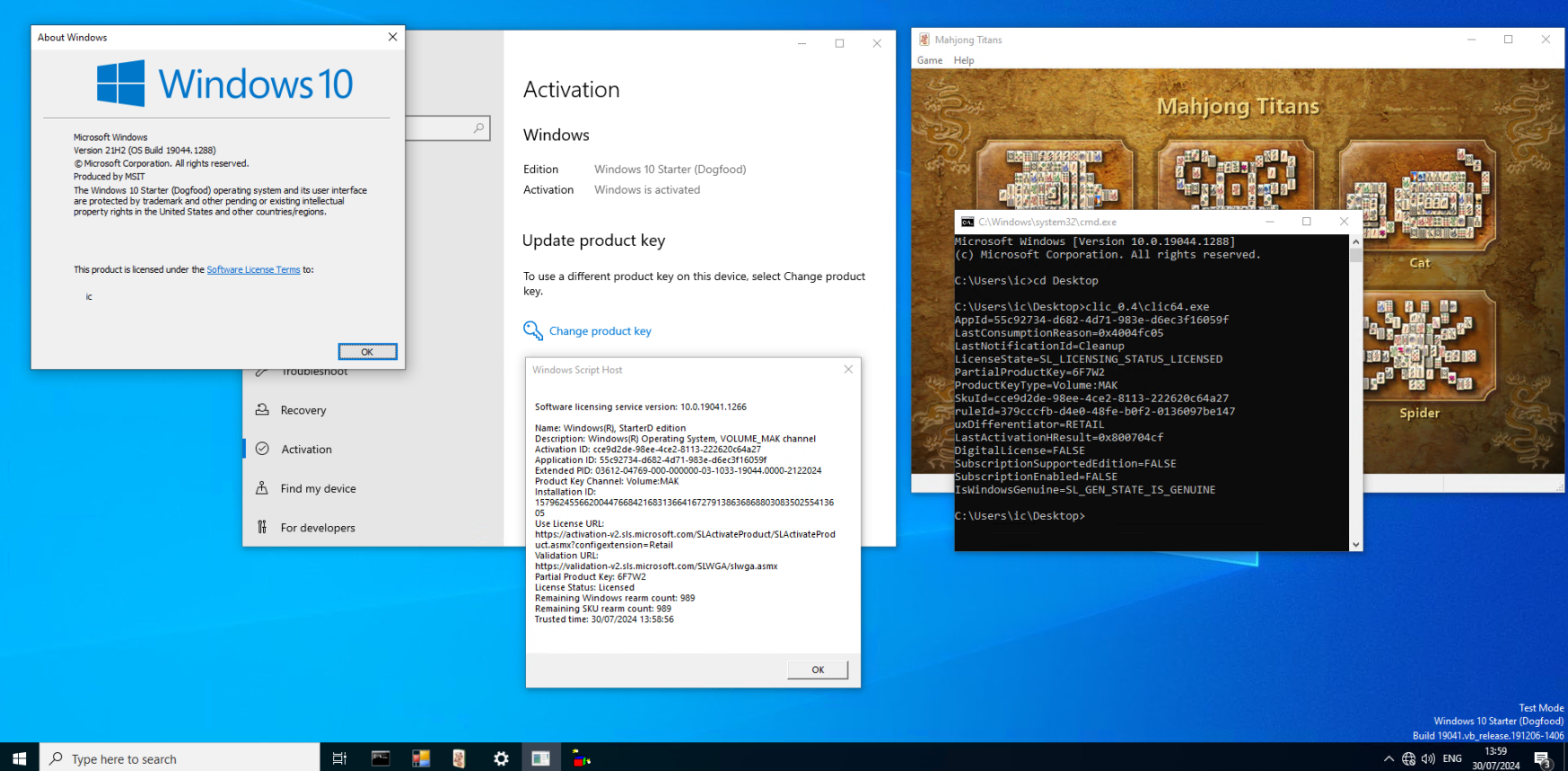
The development of TSforge highlights the ongoing cat-and-mouse game between Microsoft’s security measures and the ingenuity of researchers seeking to understand and bypass them.