Security researchers at Oligo Security have uncovered a critical set of vulnerabilities in Apple’s AirPlay protocol and SDK, collectively dubbed “AirBorne,” that put billions of Apple and third-party IoT devices at risk of remote code execution (RCE), data theft, and more.
These flaws, including wormable zero-click exploits, threaten Apple’s ecosystem and millions of third-party devices integrating AirPlay functionality.
Technical Overview
AirPlay, Apple’s proprietary streaming protocol, communicates over TCP port 7000 using a hybrid of HTTP and RTSP, with commands and data serialized in property list (plist) format.
Vulnerabilities in the way AirPlay parses and handles these plists, especially type confusion and buffer overflows-form the core of the AirBorne attack surface.
Key Vulnerabilities
| CVE | CWE Description | Attack Type | Affected Devices/Software |
|---|---|---|---|
| CVE-2025-24252 | CWE-416: Use After Free | Zero-Click RCE | macOS, iOS, iPadOS, tvOS, visionOS |
| CVE-2025-24132 | CWE-121: Stack-based Buffer Overflow | Zero-Click RCE | AirPlay SDK, CarPlay |
| CVE-2025-24271 | CWE-306: Missing Authentication for Critical Func | One-Click RCE | macOS, iOS, iPadOS, tvOS, visionOS |
| CVE-2025-24137 | CWE-843: Type Confusion | One-Click RCE | macOS, iOS, iPadOS, tvOS, visionOS |
| CVE-2025-24206 | CWE-288: Authentication Bypass | User Interaction Bypass | macOS, iOS, iPadOS, tvOS, visionOS |
Zero-Click RCE: Attackers can exploit use-after-free (CVE-2025-24252) and stack-based buffer overflow (CVE-2025-24132) vulnerabilities to execute arbitrary code on devices without any user interaction.
When chained with ACL and user interaction bypasses (CVE-2025-24206), these become wormable-capable of spreading autonomously across networks.
One-Click RCE: By exploiting improper access controls (CVE-2025-24271) and type confusion (CVE-2025-24137), attackers can compromise devices with minimal user involvement, such as a single click to accept an AirPlay connection.
Other Attack Vectors: The vulnerabilities also enable local arbitrary file read, sensitive information disclosure, man-in-the-middle (MITM) attacks, and denial of service (DoS).
For example, a type confusion in plist handling (CVE-2025-24129) can crash AirPlay processes or leak sensitive data.
Example Exploit Code
A simplified example of an exploit targeting the type confusion vulnerability in the /getProperty endpoint:
textPOST /getProperty HTTP/1.1
Host: <target-ip>:7000
Content-Type: application/x-apple-binary-plist
Content-Length: <length>
[binary plist data with unexpected CFType]
If the server expects a CFDictionary but receives a CFArray, calling CFDictionaryGetValue will crash the process or allow code execution, depending on the CoreFoundation version.
Impact and Mitigation
With over 2.35 billion active Apple devices and tens of millions of third-party AirPlay-enabled products globally, the reach of AirBorne is unprecedented.
Attack scenarios include:
- Espionage and eavesdropping via compromised microphones
- Ransomware and lateral movement across corporate networks
- Supply-chain attacks via infected third-party devices
- Distraction or data theft in vehicles using CarPlay
Mitigation Steps:
- Update Devices: Apple has released patches (e.g., macOS Sequoia 15.4, iOS/iPadOS 18.4). Immediate update is critical.
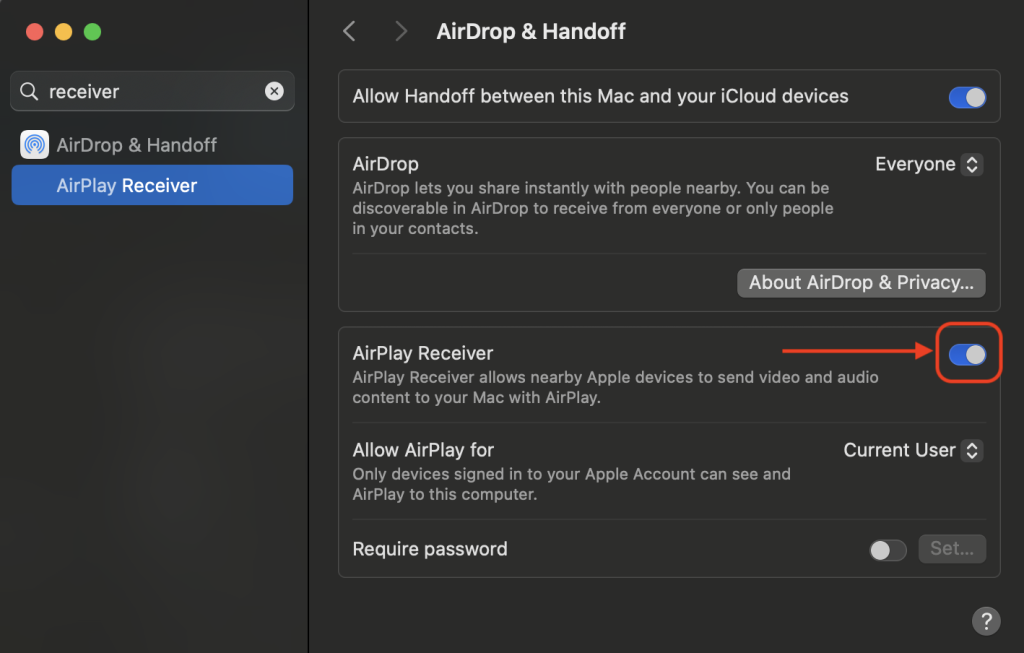
- Disable AirPlay Receiver if not needed.
- Restrict AirPlay Access: Limit port 7000 to trusted devices only.
- Configure AirPlay for “Current User” to reduce attack surface.
The Airborne vulnerabilities represent a significant escalation in wireless attack vectors against Apple and IoT ecosystems.
Users and organizations are urged to update and harden their devices without delay to prevent exploitation.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates